Purpose of the incident response retainer
An incident response retainer gives you immediate access to our Digital Forensics and Incident Response team and tooling. You get a direct line to experienced responders who can triage, contain, and investigate without delay.
It removes the blockers that slow help when you need it most. Contracts, NDAs, supplier due diligence, and purchase orders are agreed up front, so engagement starts the moment you call.
Trusted and accredited
We’re proud to be NCSC Assured for Cyber Incident Response (CIR) one of only a handful of providers to earn this recognition.
It means our people, processes, and technical capability have been independently assessed by the UK’s National Cyber Security Centre, giving you confidence that we’re equipped to handle even the most sensitive incidents.
With us, you can be confident that when an incident occurs, you can quickly engage our experts to minimise disruption, mitigate potential damage, and restore your operations swiftly and effectively
Incident Response Retainer packages
We offer a range of DFIR retainer packages that suit organisations of all sizes and risk profiles. Each tier is designed to provide increasing levels of support, speed, and value, ensuring that when incidents occur, your organisation is equipped with expert guidance and rapid response capabilities.
All packages include free onboarding to align our teams and tooling with your environment, and as you move up the tiers, you’ll gain access to faster triage times, reduced day rates, and additional proactive services. Whether you’re looking for peace of mind or comprehensive threat visibility, there’s a retainer level to match your needs.
What you get
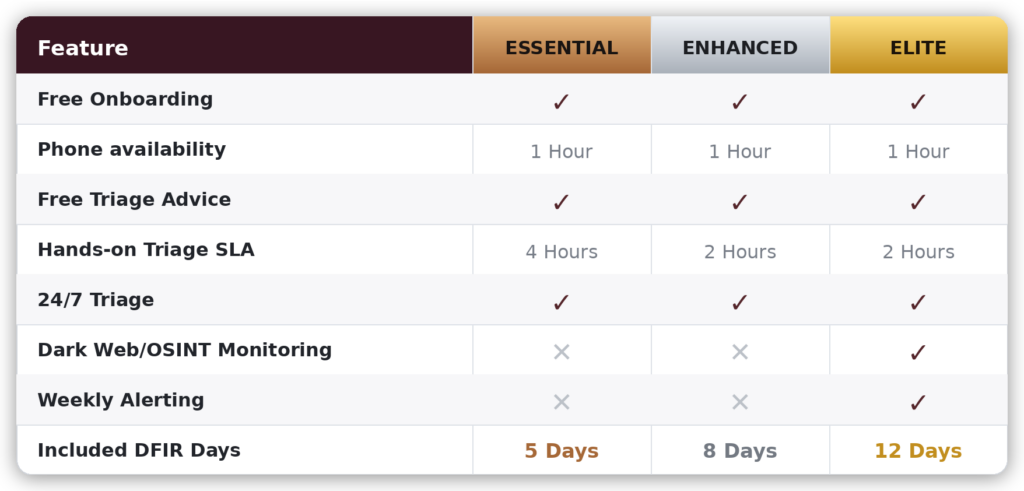
Who is it for?
Essential retainer
Perfect for teams seeking guaranteed availability and a faster response time during critical incidents.
Enhanced retainer
This is a robust option for organisations that want more coverage and significantly improved rates. Enhanced clients receive faster response times and deeper engagement across incidents.
Elite retainer
The Elite package is our most advanced tier, providing premium access, rapid response, and proactive threat intelligence capabilities for clients operating in high-risk or high-profile environments.
Clients on the Elite retainer also benefit from our Open Source Intelligence (OSINT) and Dark Web Monitoring service, providing early visibility into risks and threats emerging in open and covert digital spaces.
Tooling and lab capability
We leverage advanced remote incident response tooling to swiftly and effectively address incidents. We can swiftly deploy our agents into your environment, allowing us to quickly reach the attack’s core.
From our dedicated DFIR lab, we can conduct in-depth threat hunting, gather vital data for further analysis, and search for identified indicators of compromise to uncover additional impacted systems. In some cases, we can assist in containing an active breach by neutralising malicious services and rogue processes.
We are committed to providing exceptional service and building long-term partnerships with our clients. We understand the challenges you face, and we’re here to provide the support and guidance you need, every step of the way.
Detect & Respond

Free Pen Test Partners Socks!!!
Pen Test Partners socks are THE hot security accessory this season, if you're a security professional get yours now!