Securing ICS Environments
ICS (Industrial Control Systems) cyber security deals with the security of the control systems and associated processes, equipment, and instrumentation that are used in a wide range of sectors.
We have unique expertise in industrial environments and understand the particular challenges of securing and testing them. We have a broad and rich knowledge of ICS technologies including PLCs, IEDs, HMIs, RTUs, IMS, Smart Instruments, and IIoT.
What are we dealing with?
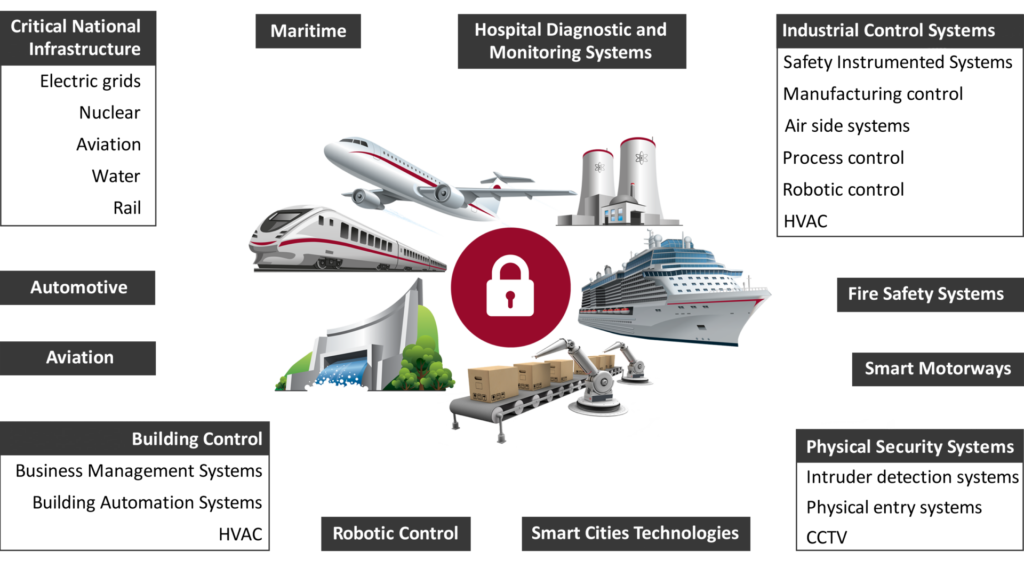
We are also acutely aware of the risks presented by vulnerable legacy systems and devices which may not be patchable.
A significant part of our ICS work involves hardware level assessments of ICS devices, in many cases discovering and responsibly disclosing vulnerabilities.
Challenges
One of the biggest ICS challenges is segregation: Understanding segregating ICS from corporate networks and implementing it correctly.
Our work regularly uncovers unintended connectivity between corporate and ICS networks.
This could enable an attacker to pivot from the corporate network to gain access to control systems.
ICS is becoming ever more integrated into business systems. This increases the risk that outages to business systems could affect the availability, integrity, confidentiality, and even safety of ICS.
The convergence with IT technologies and the expectations of IT professionals can create a culture clash with operations and engineering.
Companies are often reliant on third parties or OEMs to design, build and maintain their ICS systems.
This creates more reliance on remote support access, which adds more layers of complexity to securing systems.
The introduction of Cloud services into ICS environments challenges the understanding of how ICS can be managed and raises concerns about the potential effects on cyber security.
The pace of change in ICS technologies needs to be manged to ensure that safety and quality are not affected.
Operational security issues
There can be friction and a lack of understanding between engineering operations and OT / IT cyber security.
Reliance on hardware and systems which, due to their age and legacy status, can be difficult to maintain and secure.
Difficulty in hiring resources with the correct skills and experience and lack of internal ICS cyber security capability creates challenges, such as being able to determine ICS cyber security maturity.
Reliance on third parties and OEMs for maintenance and support.
Technical security issues
Modern ICS systems are reliant on commercial off-the-shelf operating systems and networks that can be
vulnerable to the same threats as IT systems, such as malware and ransomware.
Poor segmentation and segregation within ICS networks and between ICS and IT networks.
Requirements for ICS data to be available to corporate networks to inform business decisions.
Ensuring new ICS systems are secure by design.
ICS integration to Cloud services.
Lower layers of the Purdue Reference Model are subject to their own threats and vulnerabilities.
ICS system upgrade cycles can be 20+ years, resulting in having to secure unsupported legacy technologies.
ICS Cyber Security Services
ICS Security and Assurance
ICS (Industrial Control Systems) cyber security deals with industrial equipment which may include OT (Operational Technology) devices.
We have unique expertise in industrial environments and understand the peculiar challenges of securing them.
There is an increasing realisation of the need for cyber security in industrial environments.
This has been driven by regulatory requirement in the form of the EU’s NIS Directive, as well as some high profile incidents such as with the Colonial pipeline ransomware attack, and the Oldsmar water facility breach.
This has demanded a steep learning curve in operations and engineering departments across industry, and a realisation that traditional IT security practices do not always translate well into ICS environments.
Knowledge and Experience
Team of specialist OT cyber engineers, with experience running gas control rooms, water treatment plants, substation satcom telemetry, oil refineries etc.
Specialist expertise in hardware security, hence work on PLCs, RTUs, SMETS 1 & 2 meters, IHDs, EV chargers.
You benefit from their practical working knowledge of the challenges of dealing with highly regulated industries.
With industry recognised certifications they have the talent and insight to understand the problems you face and are able to help you enhance and assure your ICS security.
We offer ICS security services in two areas:
Testing
Consultancy
We have advised UK regulators on implementation of NIS / NIS2 / CAF.
The UK Government has changed policy in light of our vanilla research.
We carry out work for:
- UK DNOs (Distribution Network Operators)
- Nearly half of the UK’s OES (Operators of Essential Services)
- We have helped OES with RIIO-2 submissions
- Vertically integrated energy companies
- Communications Service Providers
ICS Cyber Security Testing
We work with you to assure your ICS and identify where you can make improvements.
Testing can be undertaken on new systems as part of the design lifecycle or on operational systems during designated maintenance outage windows or while in operation. The services we provide include:
ICS Hardware Pen Testing
ICS devices (PLCs / RTUs / Smart Instrumentation etc.) tested in labs or on site
Undertake for OEMs or end-users
ICS Build Reviews
Against industry standard baselines
Against company standards or requirements
ICS Boundary Testing
- ICS / IT boundary testing
- ICS to corporate network
- Corporate to ICS network
- Remote access
- Firewall reviews
ICS Infrastructure Pen Testing
- Testing ICS servers and networks
- Network segmentation and segregation
- Identifying vulnerabilities
- Wireless scanning of ICS environment
ICS Red Teaming
Inclusion of ICS environments within scope of a Red Teaming exercises
ICS Cyber Security Consultancy
We work with you to ensure that during system design and system operation you are using best practices to secure your ICS.
We advise you on ensuring that new ICS plant systems are designed and implemented securely and integrating them into existing security operations.
We also deliver risk assessments to help prioritise and inform the choice of security controls. We help you align ICS security with industry standards and, where gaps are identified, advise you on how to fill these gaps.
Our ICS consultancy services include:
Secure By Design
- Security within the design lifecycle
- Develop secure design requirements
- Assurance for systems to meets security requirements
- Integration with existing security infrastructure
Risk Assessment and Threat Modelling
- Systems in design or operational plant
- Prioritise and inform security controls
Standards Aligned Maturity Assessments
- Gap analysis
- Roadmap to alignment
ICS Security Governance Review
- Review and advise on ICS security governance
- Review existing ICS security policies, processes, and procedures
ICS Supply Chain Assurance
- Review ICS supply chain security requirements
- Review supply chain alignment with requirements
Incident Response
- IR maturity review
- IR policy development
- IR first responder training
- IR tabletop exercises
ICS Security and Network Architecture Review
- Review the security architecture of systems against standard architectures
- Configuration reviews
- Review of Cloud integrations into ICS environments
Test and Simulate

Free Pen Test Partners Socks!!!
Pen Test Partners socks are THE hot security accessory this season, if you're a security professional get yours now!