As is probably clear from our blog and public talks aviation cyber security is an area of huge interest to us. Some of us are also light aircraft pilots, so the crossover of two of our loves makes for some fascinating research.
Over the last few years we’ve managed to get access to several airplanes that have been recently retired. As the various breakers yards are backed up with planes retired during the pandemic, many fully functional planes are available that will never fly again.
However, a big problem for us is that the planes get dismantled, often between visits. On several occasions we’ve gone to an airframe to figure out the on board systems, go back to the lab to prepare custom connectors and tools, then come back a month later to find out that it’s been taken apart into many many pieces.
Some planes have been preserved though.
Last week we hired a retired Boeing 747 for a PTP event. This allowed us to share our passion and research with the wider team at PTP.
Aviation cyber talks
We had a series of accessible talks for everyone, explaining our many findings in aviation systems, plus a hackathon for the tech team to get their hands dirty on the many and complex systems on board.
Alex presented, showing the various interfaces, networks and protocols on board a plane and the security issues that each has led to:

Phil did a talk about hacking the various in flight entertainment systems we’ve looked at of late:

Nino gave a talk about vulnerabilities in electronic flight bags and the consequences of that to flight safety. We’ve cropped this image as there are some fairly serious undisclosed vulnerabilities in the talk!

Exploring the plane
Our team of around 100 people also got to explore the plane, including the parts that are usually off limits to passengers.
For the first time we got to get right up front, past the nosewheel bay. That took some serious crawling, and we found some first class menus that had managed to work their way down!

We also got to explore the pressurised hold, through the doors from the avionics bay. Those containers are full of concrete, to stop the plane from tipping backwards and ending upon it’s tail!

Business class made for a great spot to analyse the In Flight Entertainment system (IFE) disc images (see further down).


Drinking Champagne in First Class was a treat.

We borrowed a pilot who used to fly 747s to explain the various systems to everyone. Nearly all the cockpit systems are fully functional, though they were powered down for our visit for safety, as we were exploring the avionics bay.

Alex and I did tours of the avionics Electronic and Equipment (E&E) bay. explaining what the various LRUs do:

And of course we pretended to be Steven Seagal in Executive Decision, accessing the First Class cabin from the secret hatch underneath:

New findings
We’ve been meaning to have a thorough look at the IFE on board for some time. During an earlier visit the IFE wasn’t working and one of the LRUs supplying power to it had failed. That meant we had to look at the hardware and disc images instead.
We aren’t going to drop any new vulnerabilities in this blog, but here’s what we’re working on right now:
- The Cabin Management Terminal (CMT) was of particular interest. We’ve looked at older versions of this IFE and found multiple issues. A CMT is for the cabin crew to manage everything on the passenger domain (PIESD) and usually also has interfaces to the Airline Information Services Domains (AISD). This makes it a very interesting bridge between two networks. It doesn’t have any access to the ACD though, which is a good thing!
However, this CMT wouldn’t power up so we had to image the disc. Fortunately it was an easily removable SSD:


But once we had removed some of the covers, we found a whole lot more unexpected systems:

Most importantly, the media storage systems were almost brand new. They had been upgraded in 2019, not long before the pandemic hit and the planes were retired. This was a first for us – access to current IFE, so representative of planes flying today.
Also, sat on the rack next to the SSD with the O/S for the CMT was something we weren’t expecting – a 3G serial-IP router.

Our next project will be to look at this router in more depth. The firmware would suggest that it hasn’t been updated for a few years. Serial-IP devices have had a long history of security issues.
Our guess is that it was either downloading data from the AISD to ground systems on landing, possibly involving Gatelink, or could instead be used for uploading media content. We’ll blog about this once we’ve made progress.
We don’t think that it has anything to do with in-flight internet access, as it would be useless above a few thousand feet. Those systems typically use downward facing LTE / 4G or satcoms. We found the satcom terminal LRU (Line-Replaceable Unit) in the overhead space in the passenger cabin, so that’s a project for another day.

The media LRUs were really quite interesting.
Tearing them down revealed a fascinating combination of old and new.
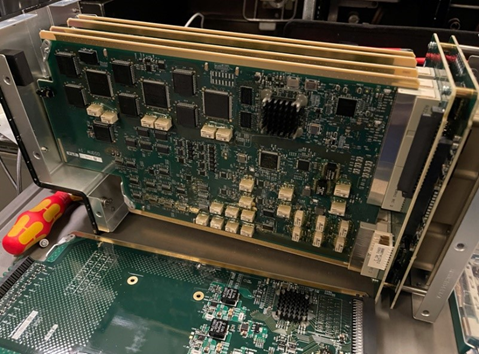
The storage media on board the LRUs was also a surprise. A CF card in one case:

We pulled an image from the CMT SSD and started looking at unallocated (slack) space. Things got weird when we recovered some photos:
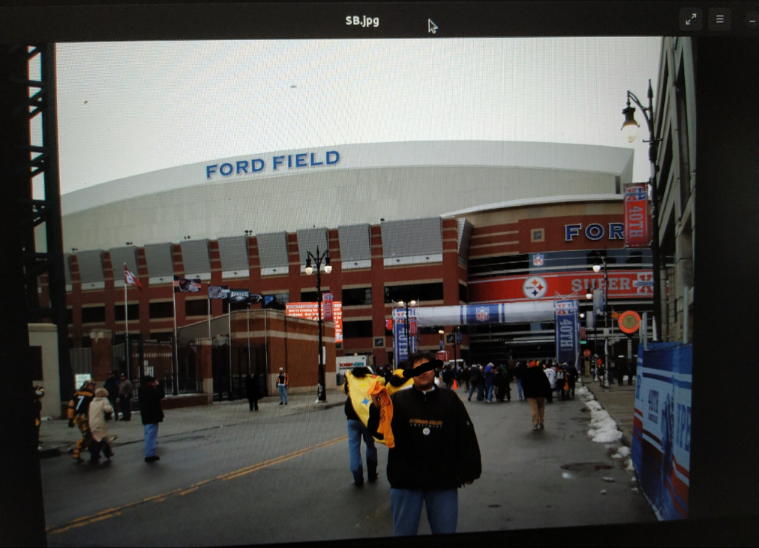
We think that the CF card installed in the IFE LRU had previously been used by one of the IFE engineers in their own digital camera. This is worrying on a number of levels, but also fascinating.
Anyway, we have a stack of new research to get done on the various images and devices we now have. Watch this space!
Party time
After we had put the LRUs and CMT back together, it was time to party in the Economy section, which had been converted to a dance floor:

Ready for transfers at midnight:

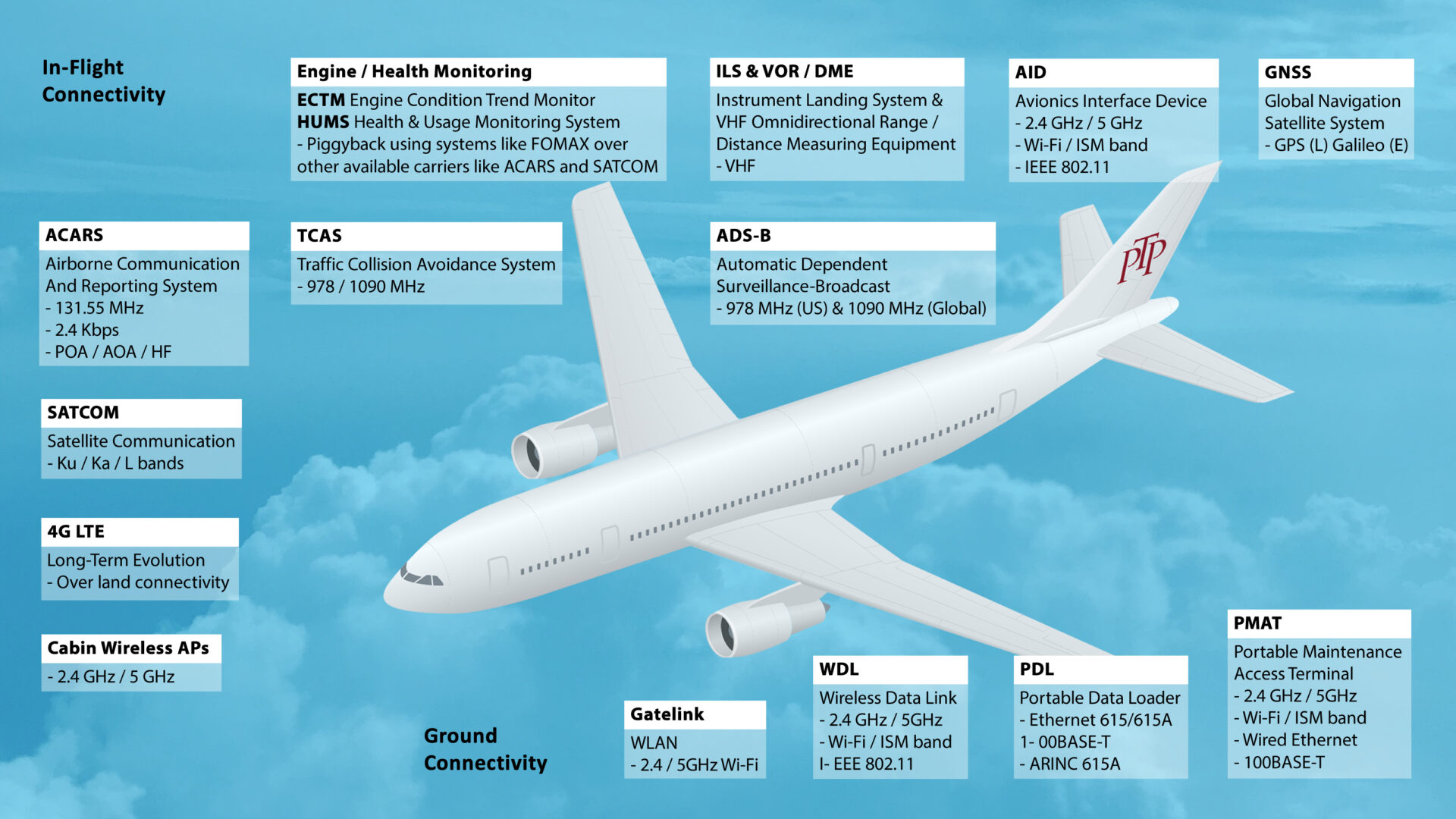
Airplane connectivity explained