As a pentester, one of the most disappointing sights is see on a test is extensive local admin password reuse. I know others get excited as it means easy pwnage of the network, but for me, it makes my job too straightforward. I want more of a challenge, particularly as resolving the local admin password issue isn’t difficult.
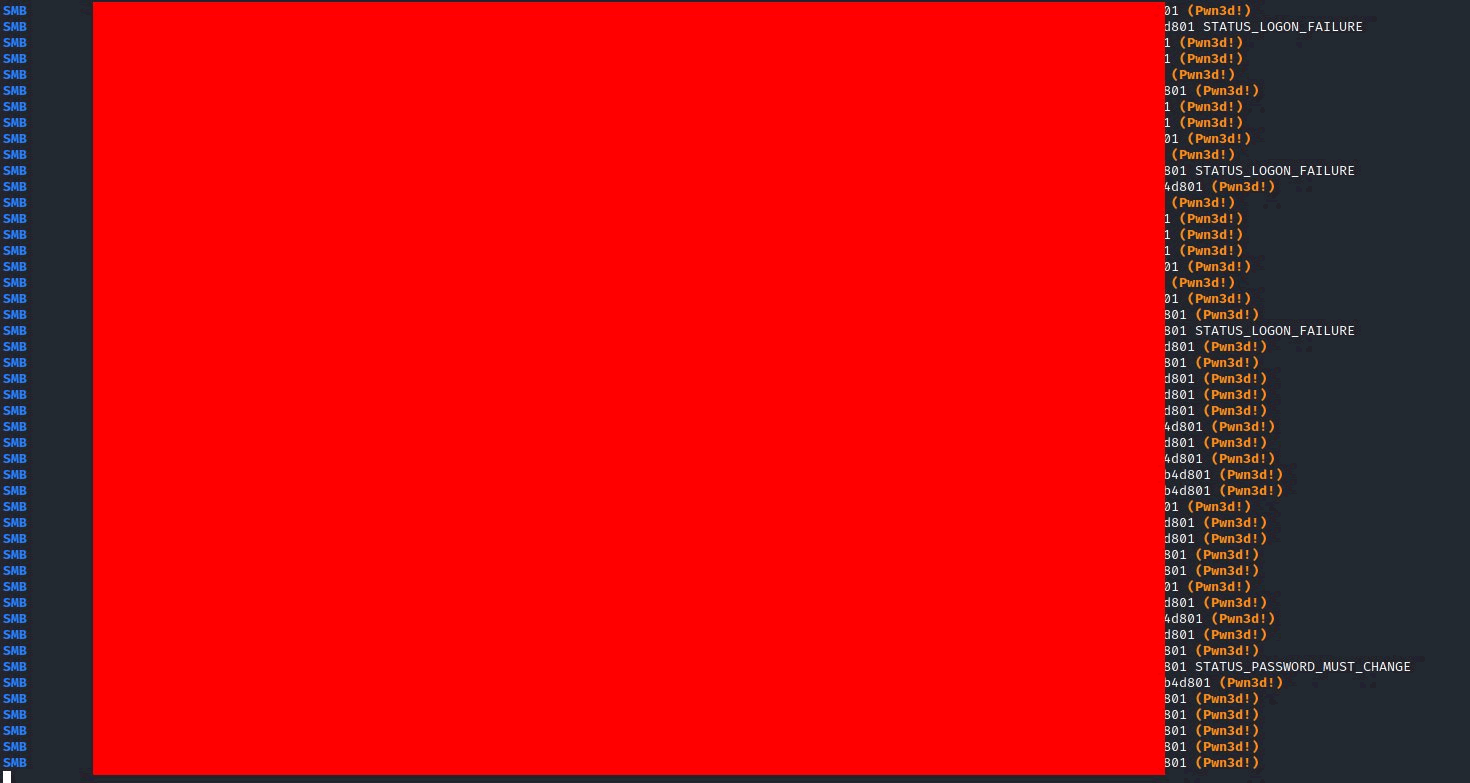
What does that screenshot mean? It shows that the majority of systems on a network re-use the same Administrator password. Allowing the captured hash to be sprayed around the network, effectively gaining Administrator privileges on all workstations.
So what can be done with that? Well LSA or SAM entries can be extracted, which are likely to contain more hashes for Domain Admins/Enterprise Admins. New users can be put onto the machines, and provided Administrator access. All without cracking the password.
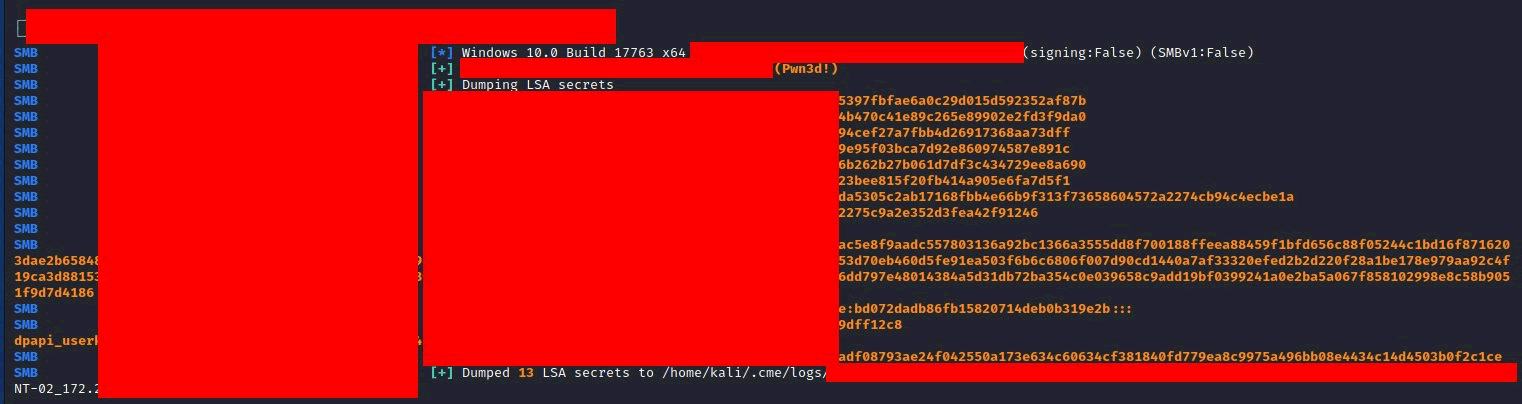
Why does this sadden me? Well there are easy fixes for this. I fully understand the ease of reusing the same password, rock up to a machine, login and fix the users issues. It’s quick, it’s easy. But this network would be completely owned by an attacker or ransomware.
You say easy fix? Yes! Microsoft provide a free tool called Local Administrator Password Solution (LAPS). Any machine connected to the domain get’s a unique, strong, randomly generated password that can change on a daily basis! That’s great, but how do I get access to it?
This is do-able via the domain controller. A new field in the computers properties is created, with the LAPS password. There are also MS provided software that can be used. It’s dead easy, may take another ~2 minutes per job, but does a heap to protect the network!
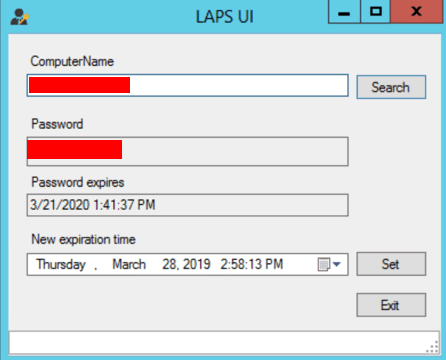
It can be rolled out via Group Policy and once it’s in, it just does its thing. You don’t have to worry or maintain it. There are a bunch of blogs on how to do it. If you are re-using your Administrator passwords, please take the time to look into this and get it rolled out!
Here’s Microsoft’s LAPS resource to get you started https://www.microsoft.com/en-us/download/details.aspx?id=46899
There is plenty of advice and help out there as well.