We recently gave a talk at the fabulous SteelCon (video here), summarising the findings of our research project in to connected adult toys. Naming and shaming vendors isn’t particularly productive, but here’s a guide to the types of vulnerabilities we found.
Where the vulnerability is already in the public domain, we’ve named it.
Whilst one might be uncomfortable discussing research in this area, the consequences of security flaws can be significant; privacy invasion is unpleasant enough, but there may be potential for extortion over stolen images/video and more.
Besides, these are very similar security flaws to those we find in other areas of IoT. In many cases, the devices are just a layer of latex over a PCB/battery/motor.
Local attacks
I’m thinking of the device itself and the phone its used with.
We’ve seen temp files written to insecure areas of phone storage. Areas accessible by all apps and potentially also to removable media.
Mobile app permissions have often been excessive too; in one case we found a sex toy app had the permission to make calls. Why?
Gathering location data can be quite a sensitive matter in relation to adult toys. Does the vendor really need this? It’s reasonable to gather usage patterns for product improvement, but not if that can be attributed to an individual users location. We-Vibe made this mistake and others in their mobile app and paid a heavy price, yet the latest version of their We-Connect app (2.5.3) still collects approximate location.
RF attacks
By far the most common security issue we found with adult toys was to do with pairing:
The Lovense Nora used regular Bluetooth and had a static PIN of 0000. However, it was only in pairing mode for about a minute after powering on:
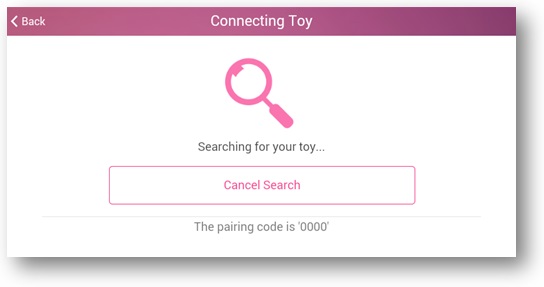
Compromising this would be difficult. The chance of locating a user over Bluetooth and timing the attack makes this unlikely. Wi-Fi is another matter, particularly if the toy operates in Access Point mode.
However, most of the newer toys we looked at used BLE. However, they invariably had no PIN or a static PIN (usually 1234) and were always available to pair with when powered on.
The only saving grace was that they only supported one connected device at a time, so if the user had connected their own phone to it, then no rogue devices could connect.
We found one toy that allowed for complete bypass of the pairing process – anyone could connect to the toy over BLE and take control.
What’s the worst case though? Someone takes over your sex toy. But all they can do is change its vibration. Annoying, but not really a security flaw.
The Bluetooth chip found in most devices was simply a serial adapter; we still have to investigate whether it’s possible to do anything to the firmware using this route.
Lack of sensors
As there are usually few if any sensors on the toy, compromise simply isn’t that serious.
…unless it has a camera inside it.
However, as adult toys evolve and become more functional, this will change. There are several manufacturers working on smart dolls with extensive optical, haptic and other sensors. Once these are out there, compromise of a device becomes much more serious.

The current range of interactive sex dolls en route to market underlines this concern with highly interactive, sensor-rich toys.
Remote attacks
This is where it gets interesting and a little scary. Local and RF attacks are generally one device at a time, so the worst case is that one user is compromised.
API attacks are likely to be possible against ALL users of the device. There is potential to intercept live video streams of users.
@alberto__segura published a fascinating analysis of the Lovense API.
To summarise briefly:
An XSS is present in various parameters of the BodyChat app. This allows device takeover if the account email address can be found
If the account email address is known, the users toy can be hijacked through a couple of different methods
And of course…. the API allows for account email address enumeration
In fairness, Lovense released a much more secure version of the app called ‘Lovense Wearables’ though oddly they haven’t pushed all users to it
There are plenty of other security flaws with the BodyChat app, though not all are disclosed.
Conclusion
The smart adult toy industry is a long way behind general IoT product security.
In most cases, the consequence is simply a hijack of device control, which isn’t particularly serious, however there are cases of compromise of much more personal information.
https://internetofdon.gs is a great resource for further research and coordinated disclosure. To quote Render, who runs the site; “Please stop laughing”.
That is a fair statement: only by taking these issues seriously and reporting them to the vendors involved do we have a chance of improving matters.
It’s worth considering that a very intimate invasion of privacy could in future be considered as sexual assault, or even rape. I spoke on a panel at RightsCon earlier in the year, joined by @astepanovich and @arthurrizer. Whilst my tack was about the technical security issues with adult toys, Amie and Arthur discussed the lack of appropriate laws to protect citizens in the event of electronic compromise of their data from adult toys. I was shocked to discover that one’s privacy could be invaded through compromise of a sex toy, yet (depending on the territory) the user would have little comeback through law.
Theft and/or extortion through very private photographs and video through other methods has already driven some victims to suicide.
A sobering thought. Let’s all help ensure this doesn’t happen through ‘smart’ adult toys.














