TL;DR
- Building Management Systems (BMS) bring new risks to businesses that haven’t had previous experience of securing Operational Technology (OT)
- While there might not be direct financial gain from hacking BMS, these systems can be a soft target for attackers to pivot into your business operations. IoT offerings in this space can help manage risk within your networks, but can also provide unintended access to sensitive information
- Not every business runs a factory, has satellite sites, or monitors a fleet of vehicles, but most businesses need to keep some buildings safe, warm (or cold), secure, and running smoothly
- Businesses are increasingly turning to high tech solutions to make this happen
- BMS are widespread across many industry sectors
Why use a BMS?
BMS can achieve amazing things. Central management and monitoring of fire, physical security, and HVAC systems has been around for decades. Evolution in technology has enabled new areas of automation, monitoring and control for building managers. These include:
- Scheduling and management of conference rooms
- Real time monitoring of occupancy and personnel movement
- Real time inventory and management of warehouse operations at scale
- Site-wide Audio Visual and lighting systems
- Central management of fire and security systems
- Environmental monitoring and management, including air temperature and quality control
These capabilities present a huge increase in functionality and sheer volume of data compared with legacy building systems. Modern BMS deployments need a central point of control and monitoring. This usually takes the form of some central dashboard, either local or in the cloud, with views available for stakeholders across different parts of the business. It will often make sense to pull systems like CCTV, access control, and lighting into this central dashboard, rather than having their own dashboards.
What do BMS usually consist of?
To run a modern BMS we need to have direct monitoring and control of individual components. This is increasingly delivered by making all our components directly network-connected. Components may include:
- HVAC equipment, such as heat exchangers or thermostats
- Uninterruptable power supplies
- Fire alarm controllers
- Fire suppression systems (such as those used to deploy gas into datacentres)
- Access control systems, such as turnstiles
- Lighting controllers
- Site wide speaker systems
BMS often include a mix of IoT systems, building systems (that use legacy technologies), and newer, networked building systems, that often fall into the OT category. Historically OT is more likely to be in manufacturing environments than in business networks. They are often designed with reliable control and monitoring as a high priority.
Security controls either take a back seat or are simply absent.
Common BMS architectures
Many BMS are a mash-up of various systems which communicate to a central BMS server via various protocols and networks. Because of remote working and third parties needing access, BMS servers are increasingly internet facing or hosted in the cloud.
In a typical environment there may be Fire, Audio Visual and other services on site, which feed into a cloud dashboard via local BMS server(s). Occupancy monitoring and conferencing are IoT systems, which then pull data into the BMS dashboard via cloud integrations. Third parties and administrators may still have direct local access to manage devices via the network.
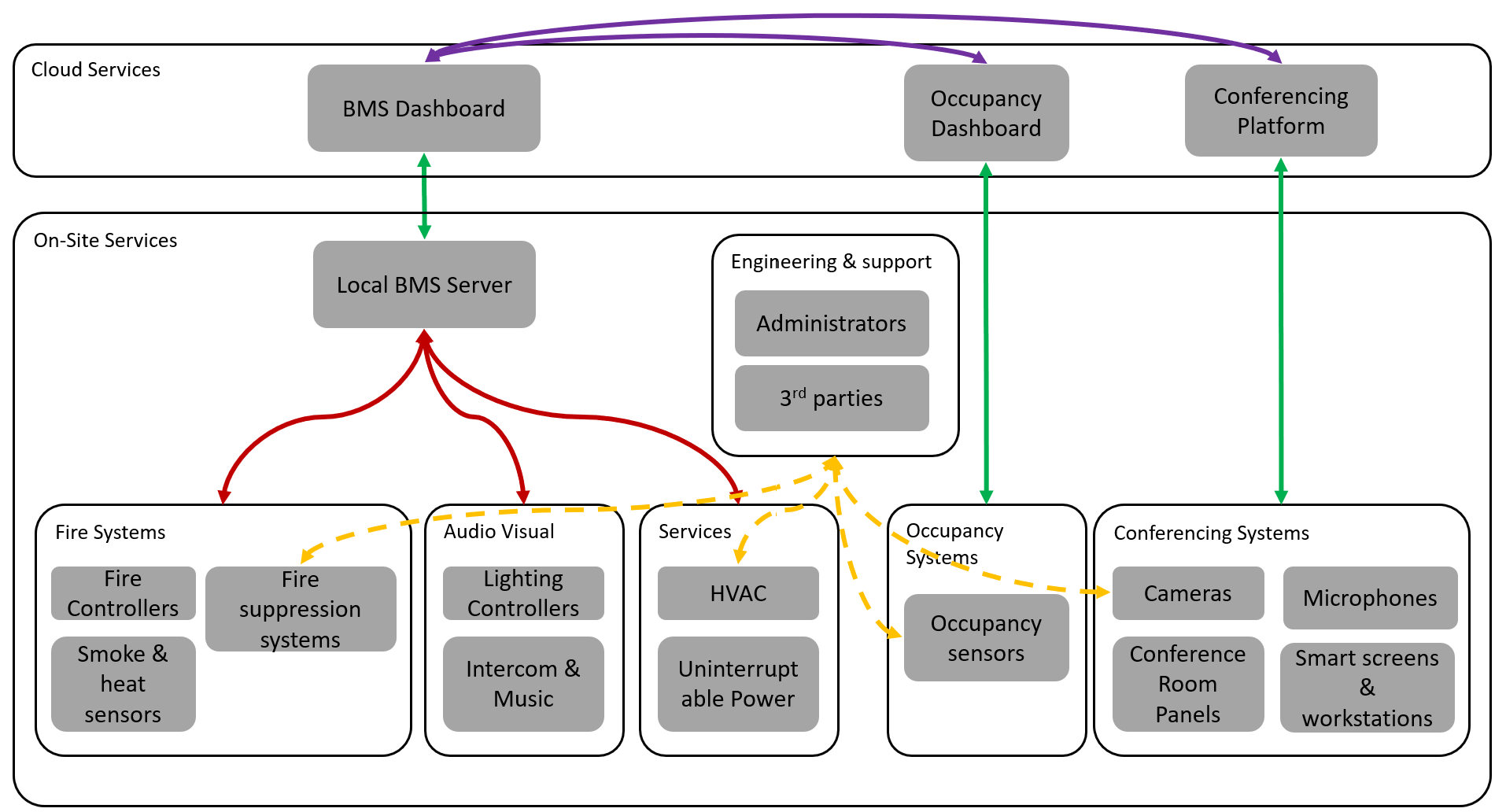
In this example, local BMS communications (red) use legacy protocols and provide open interfaces to control and monitor devices with little or no security by default.
Local BMS servers may then forward traffic to cloud dashboards via secure channels HTTPS, in the same way many IoT systems do (green). IoT components communicate with their clouds via HTTPS (green) and have bespoke cloud integrations (purple) to pull data into the BMS dashboard.
Admins and third parties still require administrative access to low level BMS devices, which can be via a variety of technologies and vary per device, but very often includes HTTP, remote desktop or text based management interfaces like SSH and Telnet.
So, release some hackers into your network and what happens?
BMS can be soft targets
If you were to point your vulnerability scanner of choice at your BMS devices (don’t, by the way!) you might be surprised at the lack of issues it raises. For this reason BMS networks may be accessible from corporate or even guest networks, when we see these devices, looking into them (carefully!) by hand can identify some interesting things.
Many devices, such as these HVAC heat exchangers expose web based Human Machine Interfaces (HMIs) with no authentication by design. Here’s a HVAC heat exchanger control interface without any credentials at all:
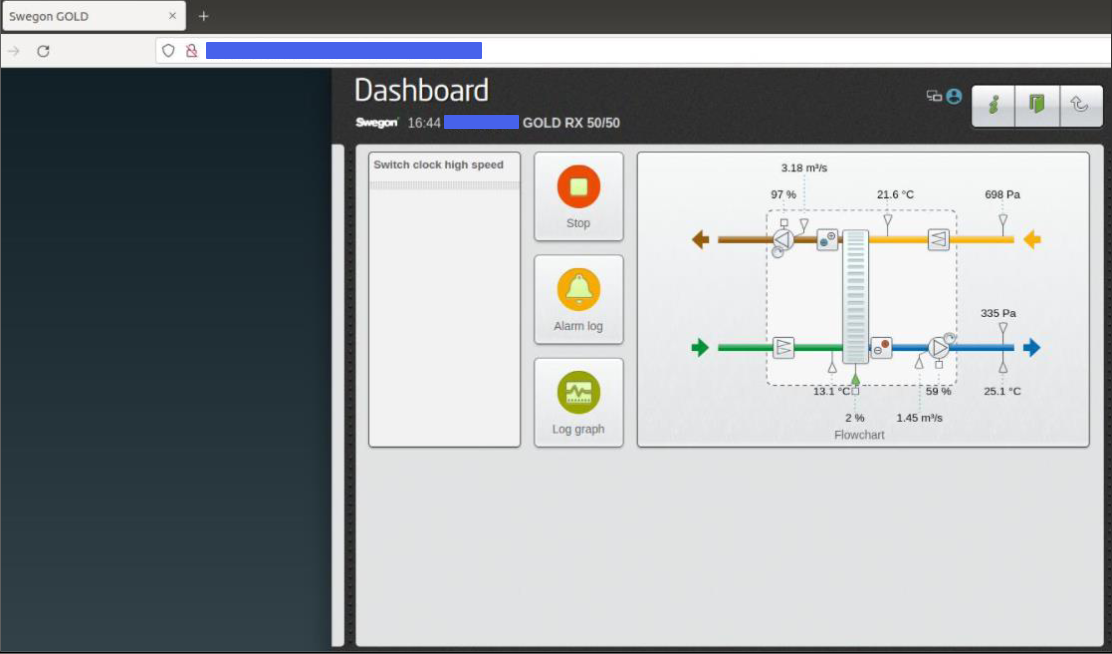
This allows anyone with access to the network to turn off the air con that’s keeping your datacentre up and running. This is very rarely identified by automated security tools unless a specific vulnerability exists in the product. These kind of open HMIs come down to product design decisions and rarely qualify as a vulnerability in their own right.
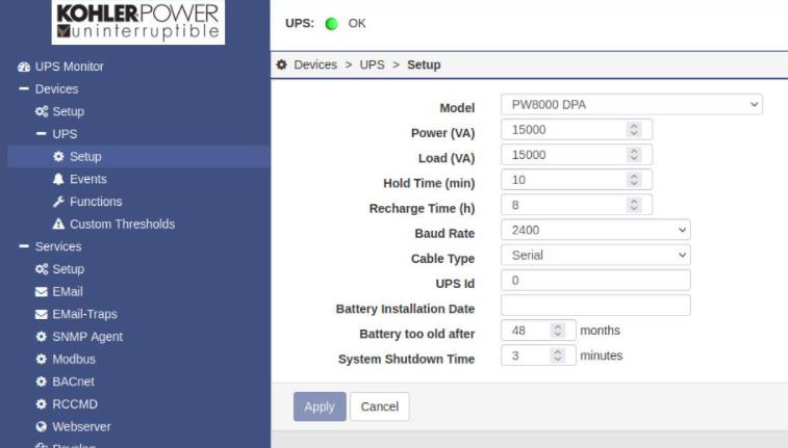
Where systems do support authentication (often over HTTP) BMS system integrators may leave systems with their default passwords. We often find admin/admin or passwords from equipment manuals that let us in to systems like datacentre power supplies.
This image shows admin access to datacentre UPS with default credentials:
What about IoT systems?
Conferencing
Businesses are also turning to cloud connected conferencing systems. They often tie-in to the conferencing solution and can join conference calls as an attendee with dedicated camera technology:

Unlike classic BMS systems, these devices offer minimal access from local networks. Instead they communicate to the internet over HTTPS and are managed via a vendor platform. This provides a means to organise and manage devices on a per-room basis, using a dashboard to allow additional devices to be provisioned to meeting rooms:
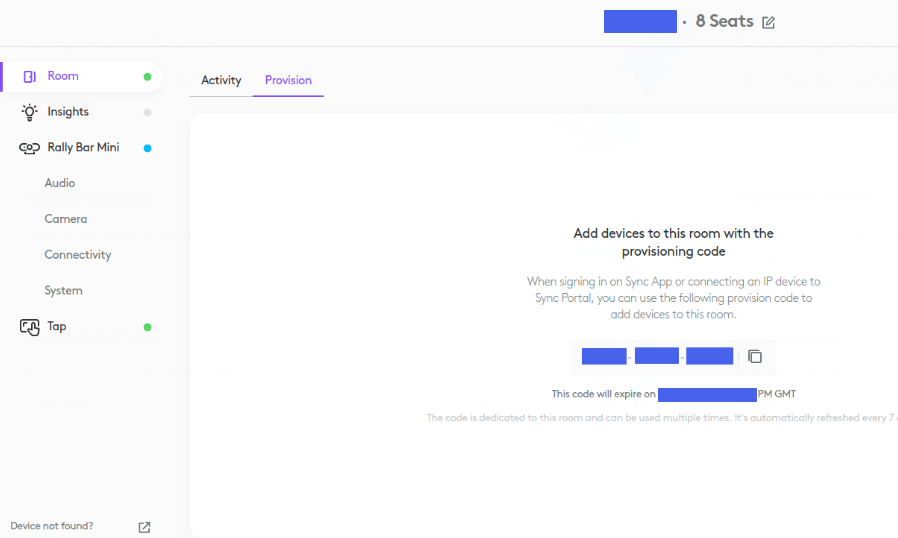
Users with dashboard access could remotely provision rogue devices to a room to join meetings. If they wanted to cause disruption they could disable conferencing devices across all sites. Walking around a site to re-pair devices is going to be time consuming, causing hours, maybe days of disruption.
Different vendors provide various levels of remote monitoring. For example the above Logitech systems don’t include remote camera viewing by design, but they do support remote room occupancy monitoring via local computer vision. It means you can provision your own display device and join meetings in a particular room.
Occupancy
In addition to the room booking and occupancy insights from the conferencing solution you can use site-wide occupancy sensors. These are IoT devices which monitor spaces using local computer vision, and report occupancy levels to a third party cloud-hosted service.
The data from this service is pulled from the third party cloud into our BMS dashboard server for use by the building management team. The problem is that third party systems are still out there and the administrators of these have interesting legacy abilities, including viewing monitored spaces via the IoT occupancy sensors.
This is a requirement to set up the sensor view field, but it allows third party admins access to video of your building spaces at any time:
These kind of sensors also provide a local web interface which allows similar live video and person tracking. Here’s a local admin interface exposed on occupancy sensors:
As with other systems installed by third parties, credentials are sometimes left as default. Because nobody uses these dashboards and interfaces, and as all the data is being centrally collected into our lovely BMS dashboard, they are often overlooked.
Tying it all together
All this BMS stuff wouldn’t be complete without a fancy dashboard to pull everything together, provided by the integrator or vendor. There are significant design challenges here as data needs to be collected from legacy systems, BMS systems, other cloud platforms and more.
This means that the dashboard is likely a fairly juicy target, containing secrets and keys that can be used to gain access to building systems from the internet. It could also be used to access third party systems such as conferencing management dashboards. This is particularly concerning as these third party dashboards are often configured once then ignored, because the focus is on the main BMS dashboard.
These systems can be vulnerable to common web security flaws, in one instance an open directory listing on a BMS dashboard provided access to third party API keys, backups of building occupancy and alarm data, hidden pages allowing for fire alarm test triggering and more.
Expect the unexpected
During a recent engagement I came across a surprising remote access solution sat dormant on the BMS network. A Raspberry Pi with an attached modem for cellular internet connectivity.

This was probably put in for remote management during the initial BMS installation. When a business builds a BMS over several years it isn’t unheard of that these kind of devices are left ownerless. If we’d not come across it during our testing there’s no knowing how long it would have sat there unnoticed.
Conclusion
While there are lots of ways to disrupt a business by hacking a BMS, it generally requires real-time access. There are also significant challenges to monetising an attack. There are better ways to do that, such as stealing information or ransomware. We also need to remind ourselves that threat actors aren’t always after financial gain. Malicious insiders and political or activist groups have their own motivations.
There is one unique financial motivation to hack a BMS though. The asset value of a building may involve it’s degree of occupancy. By tampering with data from occupancy sensors the building owner might be led to an incorrect valuation of its portfolio, potentially resulting in stock market moving corrections.
Advice
BMS owners
- Ask your vendors about the security controls in their products before buying
- Work with your vendors to inventory your BMS systems, particularly any high risk things like remote access solutions. Regularly check your inventory, using inspection and network based tools
- Ask your integrators and service providers to secure BMS environments, and how they can securely hand them over to you if you’re taking ownership of them
- Ensure that your BMS systems are only able to communicate with what they need to – probably just outbound to the internet. Keep your users off them
- Work with your vendors to inventory your BMS systems, particularly any high risk things like remote access solutions. Regularly check your inventory, both physically and using network based tools
BMS manufacturers
- Support authentication and secure authentication traffic
- Use technologies that protect BMS traffic and systems. In particular use encrypted and authenticated protocols
- Provide solutions that are secure by default for your customers. ESTI 103600 has some great guidance to help work towards products which are secure by design
BMS integrators
- Ensure your remote access solutions are agreed with your customers and that they are removed when no longer needed
- Select products and solutions that have security features built in
- Properly segregate BMS systems rom other systems and networks
- Configure BMS systems with robust, unique credentials and put processes in place to hand these over to customers














