This follows hot on the heels of my previous camera post All your video are belong to us. The Foscam webcam.
How to hack the TP Link TL-SC3230
…and send frames of its feed to a server of your choice.
We’ve just had a response from TP Link to say that this firmware will not be upgraded as the camera is out of support / end of life. Since I just bought it as new on Amazon with no indication that this is the case, I would probably recommend a little more background research than I’ve done before you purchase any new kit!
Because the TP Link device does not protect against Cross Site Request Forgery attacks, it is possible to create a web page which would start emailing all video frames to a server of the attacker’s choice.
The issue around CSRF arises because a web server can’t always tell the difference between a genuine request and one that is forged by another site using JavaScript.
Essentially the only difference is a few headers like Referer. The cookies for the site get sent automatically by the browser so you cannot just rely on a valid session cookie. (In this case, the camera uses Basic Auth, but that also gets sent automatically if you’ve asked for it to be remembered, so in some ways that’s even worse as there’s no session timeout.)
Anyway, because we think the TP-Link is likely to be on a home network, and we can read the computer’s own IP address on some browsers, we can spray the CSRF around the local network. In this PoC I’ve chosen to match on something like 192.168.1-10/24 and then send the attack to every address on whatever network we find.
I’ve provided the code to do this below; some of it is borrowed off random people on the Internet, so thanks very much for that to “mido” on stack overflow. (See http://stackoverflow.com/questions/391979/how-to-get-clients-ip-address-using-javascript-only)
This isn’t anything like production quality and was only hacked together to prove the point:
https://github.com/pentestpartners/bits-for-blog/blob/master/tplink.html
And here’s the two files that are invoked as IFRAMEs. As with the Foscam, one does configuration, the other does scheduling:
https://github.com/pentestpartners/bits-for-blog/blob/master/iframe-tplink.html
https://github.com/pentestpartners/bits-for-blog/blob/master/iframe-tplink2.html
If you visit the first file, hosted on a webserver, it fakes two POSTs to each IP address on the local network, which the camera can’t distinguish from genuine user-initiated commands.
A quick fix would be to check the Referer header is sensible before acting upon any POST requests.
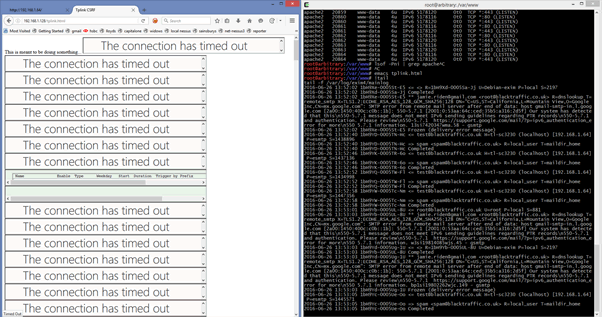
This is the screenshot showing the CSRF spray on the left, and the email starting to flow in on the right.
Our advice
Owners: As the bug isn’t being fixed you could consider replacing the camera. If you are sticking with it however you’ll need to be careful.
This is the manufacturers advice:
“…try to fix it by cleaning the cookies of the web browser and don’t check remember password.”
IoT vendors: These devices have a long lifespan, so think carefully about pulling support from product that is still being sold. You run the risk of damaging your brand.














