Introduction
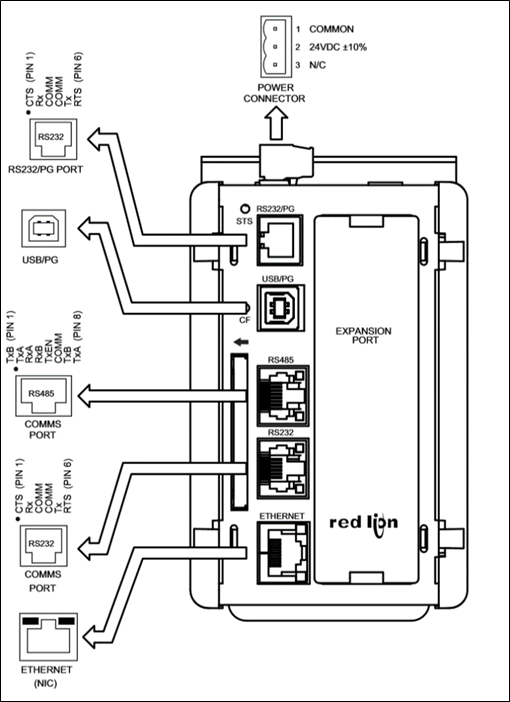
The Data Station Plus from Red Lion Controls was handed to me to analyse the attack surface.

The device is designed to connect to SCADA data acquisition devices over Modbus, Profibus, etc. by Serial or Ethernet connection. Data is collected and recorded to a local compact flash card and transferred to other systems by FTP, read through an OPC proxy or presented via a built in HMI web GUI.
Manufacturers Information
Support, product documentation and software downloads are available via the Red Lion web site:
Product page: https://www.redlion.net/product/protocol-converter-data-logger-virtual-hmiqvga
Documentation: https://www.redlion.net/support/documentation
Software URL: https://www.redlion.net/support/software-firmware
Security Overview
From a security point of view, in its default state, the device has little that would be considered an attack surface, with all the ports disabled. This provides more than adequate security, but little in the way of functionality. Here is a summary of the ports, services, and security settings available:
- Web – HTTP only, basic auth and IP restrictions
- FTP – No SSL/TLS, plain text auth, no IP restrictions
- TCP Programming – unrestricted
- OPC Proxy – IP restrictions
- Passthrough Serial – no restrictions, but ports never open
- No apparent firmware upgrade facility
- No apparent factory reset
Although not a device specific issue, large numbers of Red Lion devices are visible on Shodan, including the unrestricted programming interface. Operators need to be reminded to lock down these interfaces, surely a useful service that the vendor could offer?
Lab Setup
A desktop ‘lab’ was setup, comprising of a small pile of kit:
- 24v PSU
- Mikrotik Router
- Red Lion DSP
Configured as follows:
- Setup isolated local test LAN with DHCP server (Mikrotik RB450g)
- Install test Windows 7 dev VM from https://developer.microsoft.com/en-us/microsoft-edge/tools/vms/
- Setup Bridged VMNet on USB Ethernet adaptor
- Download Crimson 3.0 configuration software from Red Lion: https://www.redlion.net/crimson-30 – note that this has several significant vulnerabilities, so v3.1 release 3112.00 is recommended.
- Copy to VM and install
- Connected via USB and connected via VMware ‘Removable Devices’
- Mounts as USB disk
- Run Crimson 3.0
- Select File -> new -> Data Station Plus -> DSPSX (Model DSPSX000)
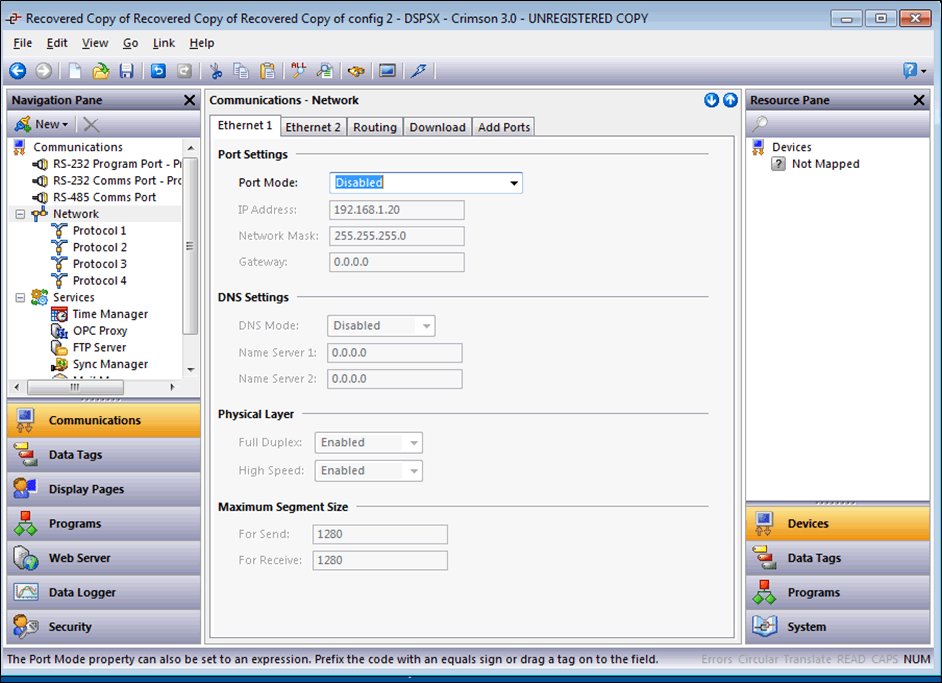
- Set Ethernet 1 to DHCP
- Check DHCP lease on router
- Test connectivity (ping)
Test and Investigation
Configuration and Programming
All configuration is carried out through the Red Lion Crimson 3.0 software, different versions of which appear to apply to different products rather the usual update or feature release numbering that is familiar.
In its default state the DSP has no Ethernet configured, therefore initial configuration was carried out via USB.
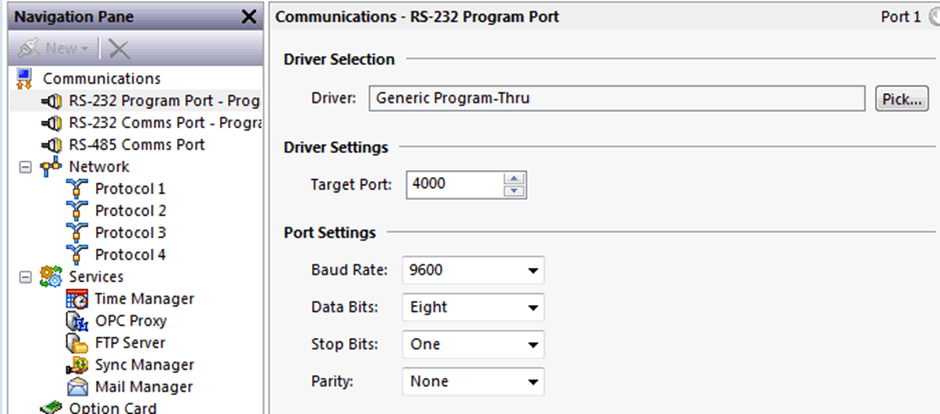
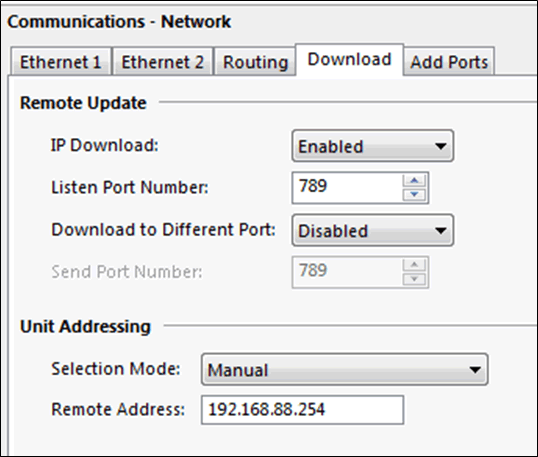
Communications – Network
Initial network configuration is via: ‘Communications – Network – Ethernet 1’, as shown above. As the configuration is sent to the device there is no feedback, so when a DHCP address is configured this must be identified by other means.
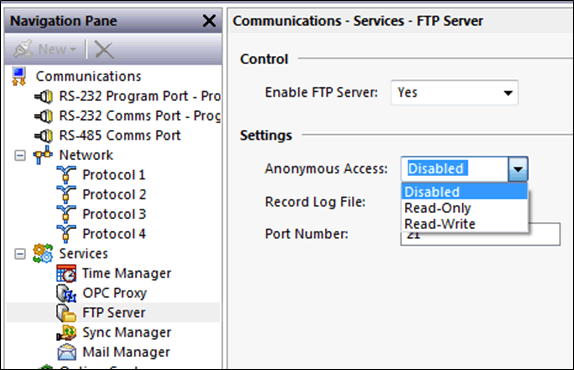
FTP Service
Configured under “Communications – Services – FTP Server”, default port: 21
Security:
- Anonymous access can be ‘Disabled’, ‘read-only’ or ‘read/write’
- The port does not respond to nmap or ftp connections when the service is disabled.
- TLS / SFTP is not supported
- User accounts configured via ‘security’
- No IP filter or whitelist
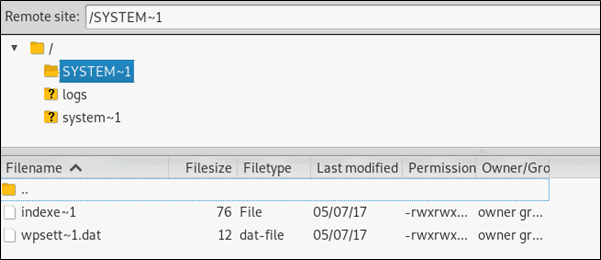
Footprint info from anonymous login:
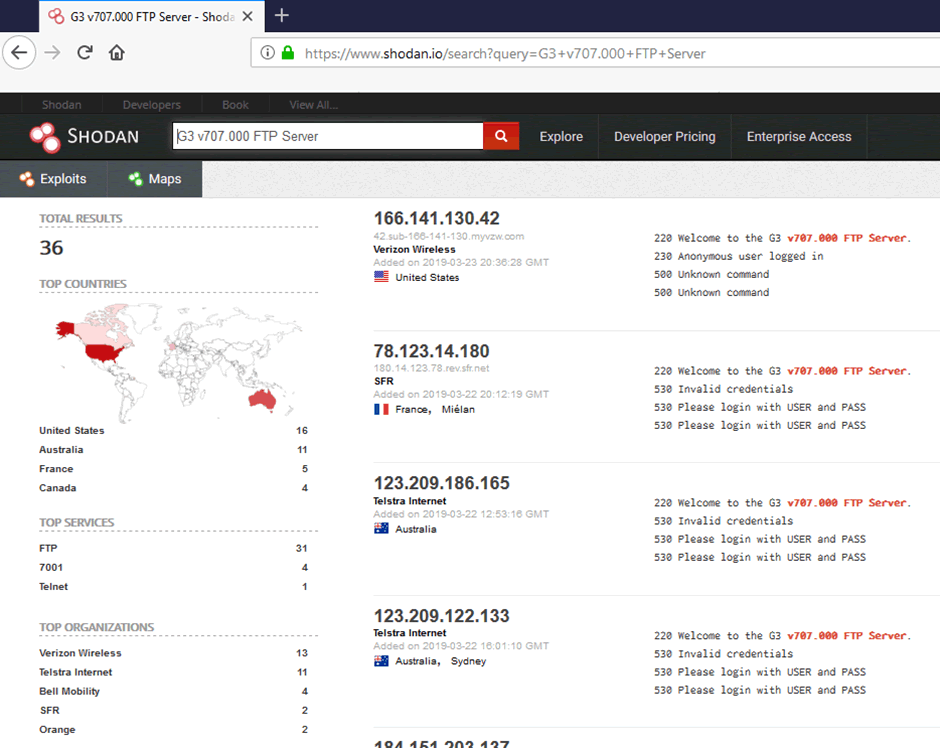
2019/03/25 20:57:43 >>> 220 Welcome to the G3 v707.000 FTP Server.
Anonymous Login
Anonymous login was enabled and tested:
- Files downloaded and examined for ‘interesting’ content, nothing noted.
- Nmap ftp scripts run without any results, ftp-anon!, brute, vsftpd, etc.
- Command line and filezilla anonymous tested OK.
- Directory traversal tested – unsuccessful.
- File read / write
Shodan search
Shodan search of the footprint reveals a number of open FTP servers:
Serial port
Evaluation of the serial ports was limited, both as a programming connection, raw passthrough and as a modbus master device. When time allows we will set it up with a real Modbus RTU slave for in-line monitoring.
Configuration:
Tested with both Prolific and Startech USB to serial convertors with serial lead made up as per: https://www.redlion.net/sites/default/files/media/CBLPROG0_2.pdf, wired both straight through and crossover (null modem).
Passthrough
Configured on ports 4000 & 4001.
No traffic or connection available on TCP or UDP ports.
Nmap scan:
Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-25 16:51 GMT Standard Time Nmap scan report for 192.168.88.254 Host is up (0.00083s latency). PORT STATE SERVICE VERSION 4000/tcp closed remoteanything 4001/tcp closed newoak MAC Address: 00:05:E4:02:33:6D (Red Lion Controls)
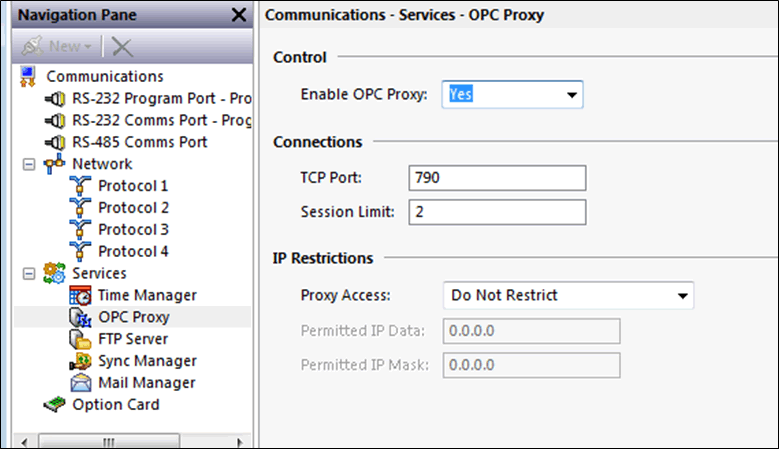
OPC Proxy Service
The OPC Proxy service can be configured on/off with access restrictions or read or read/write access.
A simple IP / Mask restriction is configurable
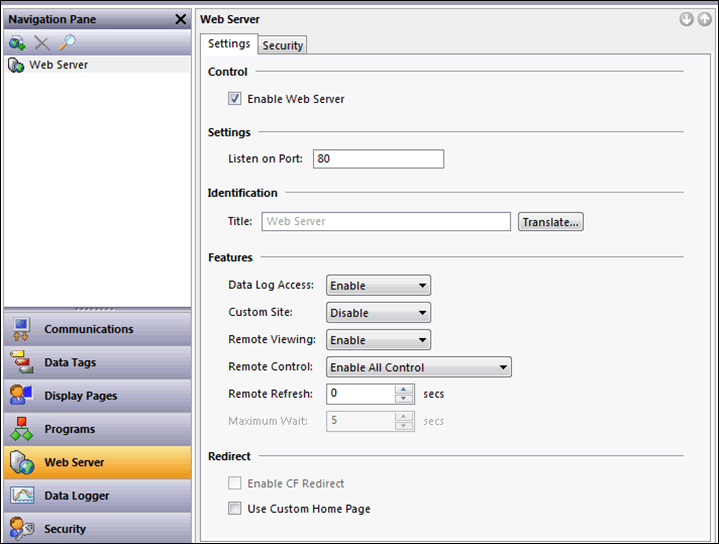
Web Server
The webserver is configured under its own section in the Crimson 3.0 software:
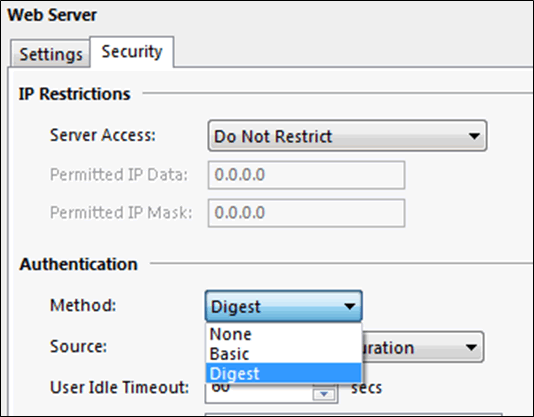
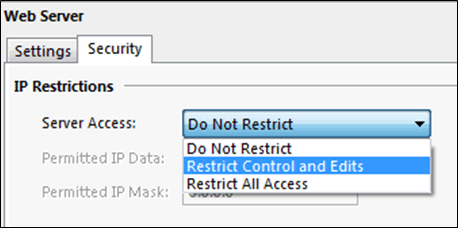
Web server security
The web server security settings include simple user authentication and IP restrictions. All communications are via plain text HTTP.
Display Pages
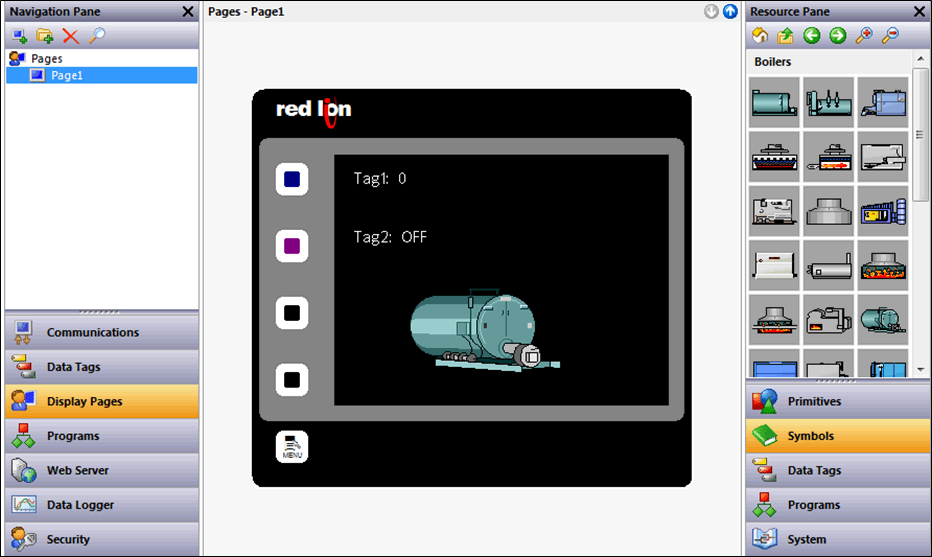
Web display pages can be built using a graphical library, active buttons and tag’s can be added along with simple access rules and programming language.
Remote control
Remote control through the HMI is achieved with a combination of simple, local JavaScript and a rapidly refreshed bitmap image of the rendered screen.
Button presses are achieved by adding the button ‘code’ as a variable to the image request, button “?0,80” refers to button 0, “?0,81”, etc.:
http://192.168.88.254/remote/display.bmp?1553550193026?0,80
Web Server Errors
It is fairly easy to generate a 404 error:
<html> <head> <meta http-equiv="content-language" content="en-us"> <meta http-equiv="content-type" content="text/html; charset=windows-1252"> <meta http-equiv="pragma" content="no-cache"> <title>Page Not Found</title> </head> <body> <p><font face=tahoma size=4 color=#FF0000><b>Page Not Found</b></font></p> <p><font face=tahoma size=1>Powered by <a href=http://www.redlion.net>Red Lion</a>.</font></p> </body> </html>
The widows-1252 charset, Tahoma font and the use of ‘.bmp’ format for images suggests some variety of embedded windows web server and OS. The nmap scans below suggest Linux.
Fuzzing of the url ‘http://192.168.88.254/remote/display.bmp?1553550193026?0,80’ was carried out using Burp Suite Intruder, both manual changes and brute force options, there were no apparent results.
TCP Programming
The device can be programmed through TCP port 789, this has to be enabled and is not open by default.
Communications are not encrypted, and no access control mechanisms are available:
Capturing the uploaded configuration using Wireshark suggests a proprietary format that revealed the use of cloud based “Cumulocity IoT” service, this is not evident in the configuration.
0000216F 16 00 74 00 65 00 6e 00 61 00 6e 00 74 00 2e 00 ..t.e.n. a.n.t... 0000217F 63 00 75 00 6d 00 75 00 6c 00 6f 00 63 00 69 00 c.u.m.u. l.o.c.i. 0000218F 74 00 79 00 2e 00 63 00 6f 00 6d 00 00 00 01 00 t.y...c. o.m..... 0000219F 00 00 05 00 4e 00 6f 00 64 00 65 00 00 00 00 10 ....N.o. d.e..... 000021AF 00 75 00 73 00 65 00 72 00 40 00 64 00 6f 00 6d .u.s.e.r [email protected] 000021BF 00 61 00 69 00 6e 00 2e 00 63 00 6f 00 6d 00 00 .a.i.n.. .c.o.m.. 000021CF 00 09 00 70 00 61 00 73 00 73 00 77 00 6f 00 72 ...p.a.s .s.w.o.r 000021DF 00 64 00 00 00 05 00 0c 00 12 34 01 00 50 00 1e .d...... ..4..P..
What appear to be default credentials were found to be invalid on the IoT portal. This was hosted by a third party so was out of scope.
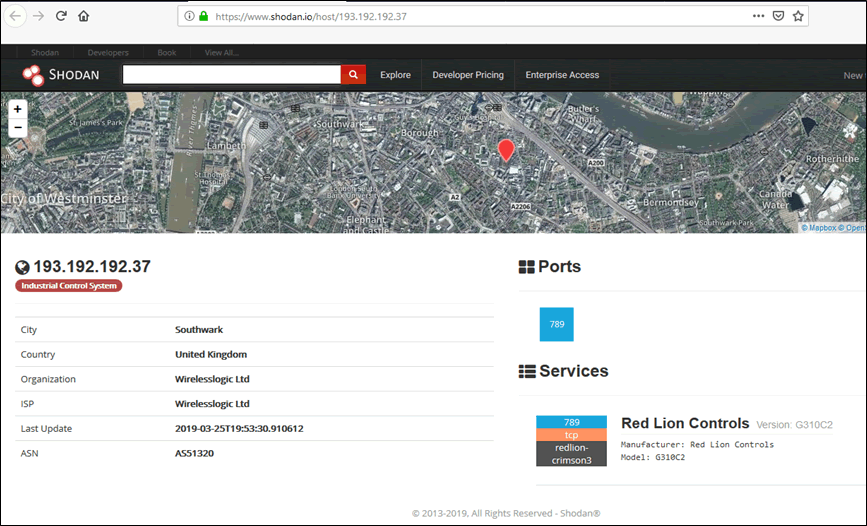
Shodan
A quick Shodan search of port 789 reveals that Red Lion Controls programming ports are open on the internet, one example found is shown below:
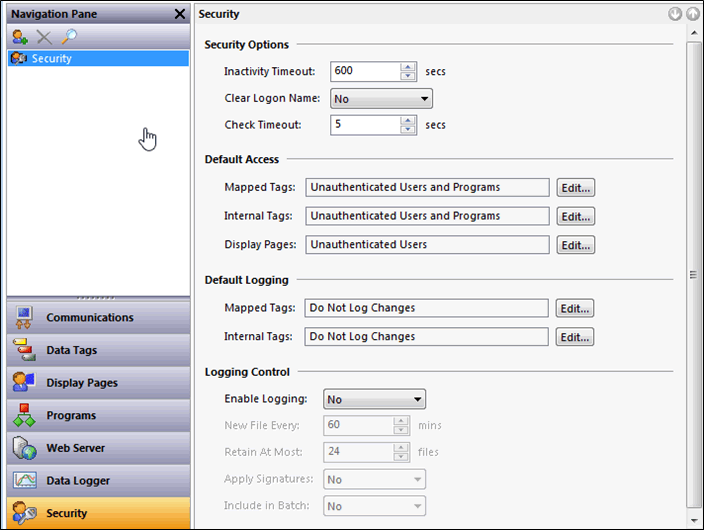
Security Configuration
The security section allows creation of users and configuration of access control to FTP and Web resources. There is no password policy enforcement and all passwords are passed over unencrypted or plain text communications.
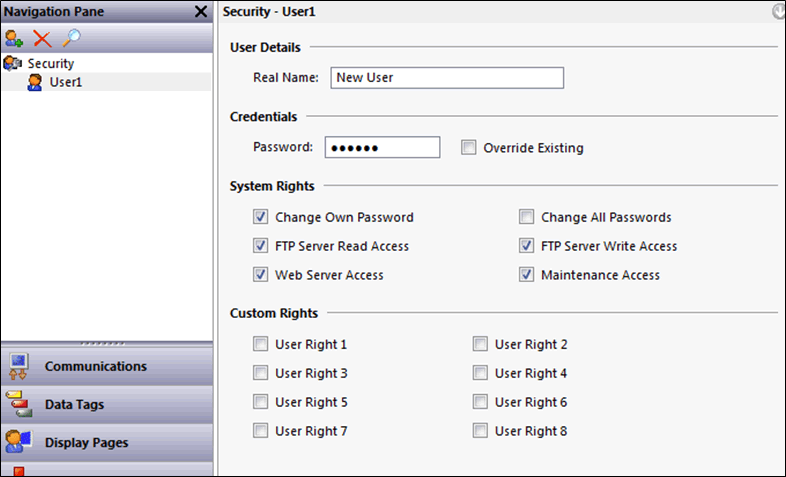
Scans
Nmap
TCP service scan, no UDP ports open:
PORT STATE SERVICE VERSION 21/tcp open ftp 80/tcp open http 789/tcp open unknown 790/tcp open unknown
Conclusion
So now that we’ve identified the attack surface and possible vectors, the next step will be to find some interesting vulnerabilities.
Red Lion Controls have had a few security vulnerabilities in the past, including one which we’re going through disclosure with them right now, on an unrelated ICS product.
Let’s see where this leads, watch out for a follow up blog.














