
I recently got an email pointing me to a set of Wi-Fi enabled scales. As the office lardy person, I probably ought to take it personally BUT as it’s something new to hack I ordered one.
Set up
The thing that struck me first is that there are no configuration controls on it and no easy way to set up your wireless SSID and PSK. Potentially it could take a binary pattern through pressing on the top of the scale, but that would be tedious to set up.
The included instructions weren’t helpful: go to a URL, download a Windows executable, or follow a wizard on the website. This still doesn’t help does it?
After a lot of faff trying to run the client in a VM, then discovering it needed to have a controlled wireless connection; then more faff trying to get my USB wireless card to play with Windows in a virtual machine (hint, it doesn’t work very well; with Linux it works straight off). I decided to follow the wizard on the website (passing it through Burp Suite on the way of course).
The first step is that it forces you to sign up for an account on their website, and it performs the so-last-decade trick of using HTTPS only for passing credentials. This is a bad thing, as it leaves your application open to session fixation and encryption downgrade attacks.
Following the use of a temporary email address (I don’t like giving out my real email addresses) and lying during registration. (Everybody should do this: there is no reason why you should ever hand out your real date of birth to private corporations).
Observations
The first thing I noticed was the bad regionalisation of the website; it passes a cookie “lcl” for language which states en_GB and then insists on using the word “Personalize” [sic].
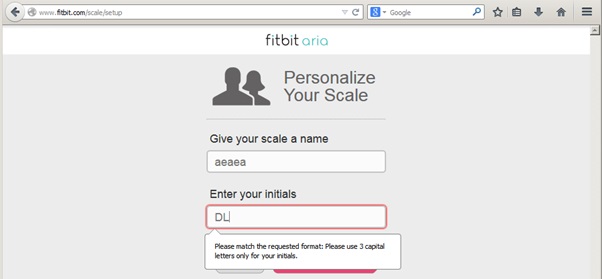
It also fails the use case where the user has more or less than three letters in their initials:
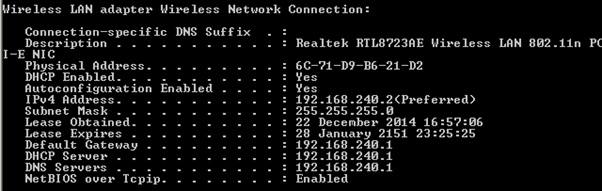
The second was we finally got to how to configure it: you place it in a special setup mode by causing a full on power reset, then it creates a simple wireless access point, called Aria and a reference number for the scale. Joining the network grants you the IP address 192.168.240.2 and points you to 192.168.240.1 (the scale):
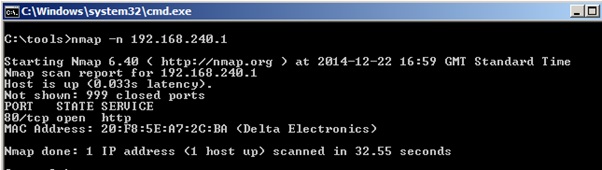
A quick port scan of shows only port 80/tcp is open:
Visiting this in a web browser just results in a 404. A bit of digging into the web wizard shows me that I need to get the path right, /scale/setup gives a valid response:
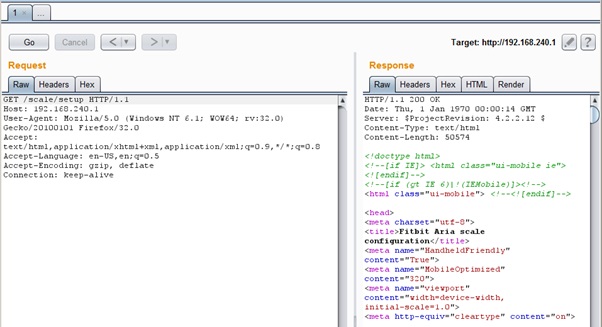
What’s interesting is how they manage the authentication technique: you go through the setup process and then are issued a cookie, called token, which is valid for the whole .fitbit.com domain:
Due to the domain policy of cookies this means that this cookie will be sent to any host with a host name that ends in .fitbit.com. The host name will come from DNS. Also note the lack of Secure and HttpOnly flags.
Now when the system connects to the scale, as the scale provides DNS too, it connects to http://1.scale.www.fitbit.com; this means that your browser passes the token cookie. Note that this is all performed through cleartext, as using HTTPS would complicate this sort of abuse of the same origin policy. This does leave a window for stealing the authentication token during setup of the scale.
Anyway; you can now get the picture – you set up the scale through its private wireless network, it takes your wireless data and then connects to the Fitbit servers by itself. It is now configured and you can use it to weigh yourself.
When you weigh yourself it will take the measurements and then enable its wi-fi interface and send it to the Fitbit servers. This makes it hard to analyse as wi-fi is only enabled while it performs a call back. All results can be viewed directly on the website.
So, let me reiterate:
- You configure a device to your home network with no management interfaces or controls
- The device dials back to its home base when it wants
- You have no visibility of what it sends to its home base
- Its firmware is not accessible
Network implant?
That is what I would call a network implant; it’s in the perfect place to map your network and, even better, it is invited in to your network, just for allowing Internet access to your weight.
I have no idea what it sends back to Fitbit, and I have no reason to believe it is malicious; but I certainly know it sends back more information than necessary, when I went into my profile and saw my home’s SSID staring at me (obviously redacted):

As most people use their router’s default SSID which is usually unique, it is possible to physically locate their properties through the use of services like wigle.net. This does lead me to the question of if the device sends your SSID, what else does it send? …and I’ll be covering that and more in my next post.














