What is Black Basta ransomware?
Black Basta is a threat group that provides ransomware-as-a-service (RaaS).
The service is maintained by dedicated developers and is a highly efficient and professionally run operation; there’s a TOR website that provides a victim login portal, a chat room, and a wall of company’s names who’s data has been leaked.
The group first surfaced in 2022, with intel suggesting that the group was buying up stolen credentials on various dark markets. Reports of attacks came soon after. They’re currently in second place, trailing only Lockbit in ransomware attacks globally, targeting a wide array of industries notably in Europe and the US.
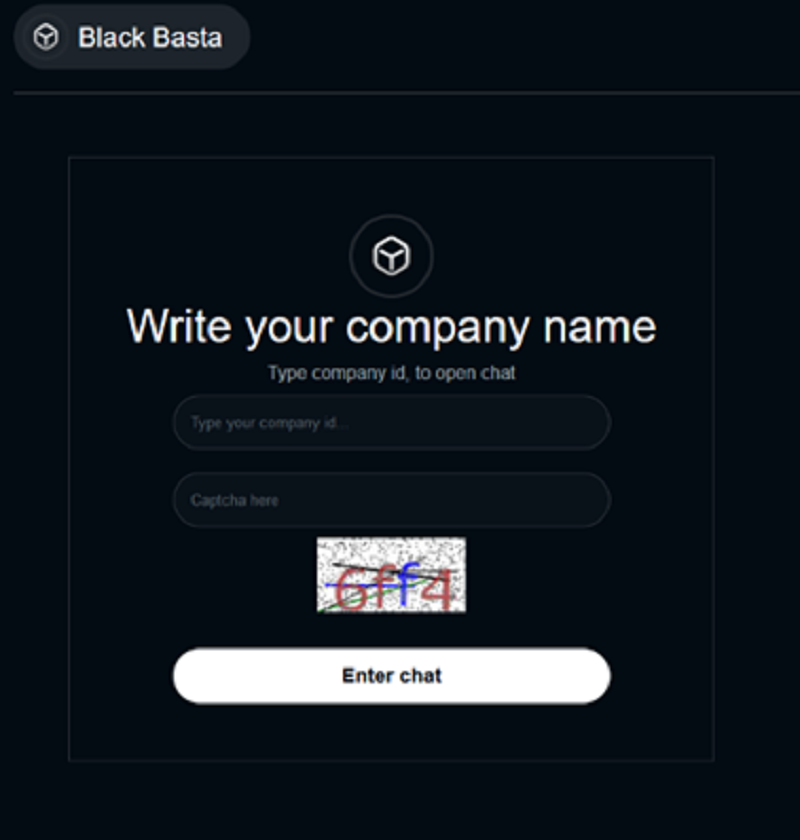
Victim chat / login portal:
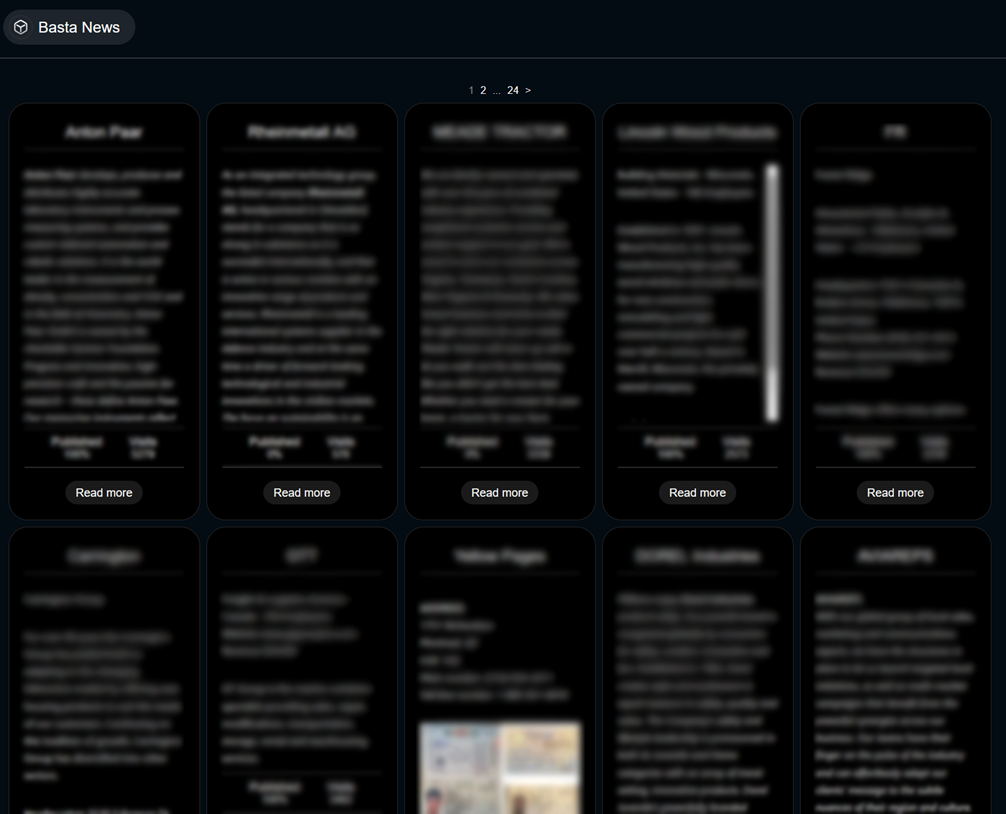
News board (obfuscated) publishing data leaks:
In addition to the usual year on year double-digit percentage increase in ransomware attacks, BlackBasta has had a huge uptick in attacks since October 2022 landing some high profile victims such as Marshall Amplification and Capita IT.
They are also infamous for their double-extortion methods, stealing data as well as encrypting it. This piles on the pressure for victims and provides another avenue in selling on the ill gotten information.
They’re believed to be a geographically Russian based group, and based on attack pattern analysis and observed tactics; they’re also likely an offshoot, or related to the Conti ransomware family.
The well-organised nature and high volume of attacks, combined with a distinct lack of affiliate recruitment on the usual DarkNet sites has given rise to the speculation that the group is state-sponsored.
Slick professionals
What takes a lot of people by surprise is the slick professionalism of these threat actors. They are labelled ransomware ‘gangs’ but that downplays how they operate. Black Basta is no different.
Swap the shady dark web site for a service desk and support portal, seized and stolen PII data for business deals in the hundreds of thousands of dollars, and the idea of a lone nerdy hacker in their bedroom for a hierarchical, structured company with various departments, promotion opportunities, and 3rd party outsourcing.
Chat logs for Black Basta now in the public domain show:
- Technical assistance being offered
- Cryptocurrency tutorials
- Friendly interactions with clients
There are even promises of forensic reports, detailing the vulnerabilities that have been used to gain access in the first instance.
These levels of service should act as a stark reminder of the sophistication involved.
How are they targeting victims?
This isn’t a spray and pray approach. Companies are selected and targeted.
Spear phishing emails are sent to valid accounts containing malicious payloads – most commonly Microsoft OneNote (.one) as attachments, but has also been seen using other Microsoft document file formats. Opening these files will often show a “CLICK HERE TO VIEW IN OFFICE 365” image (an attempt to confuse potential victims)..
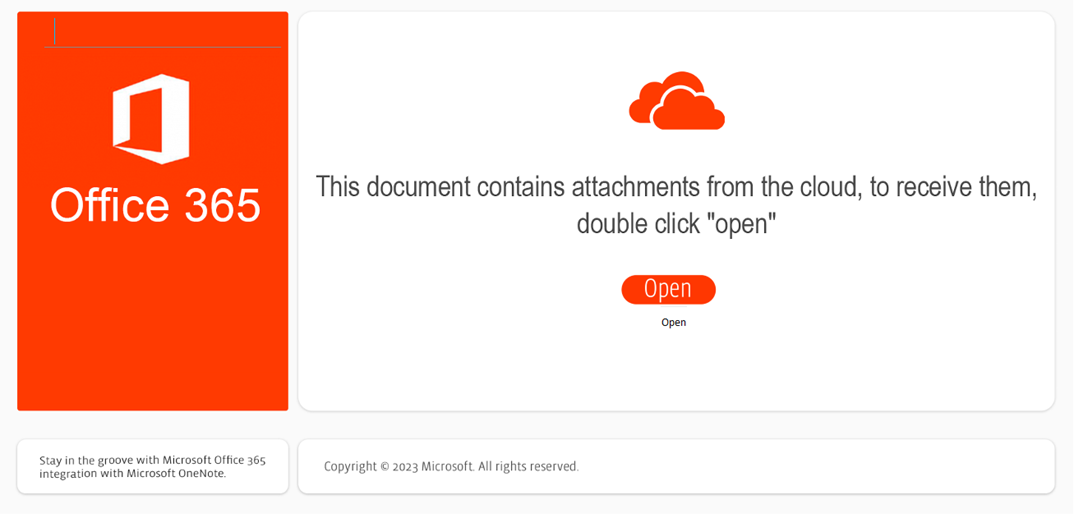
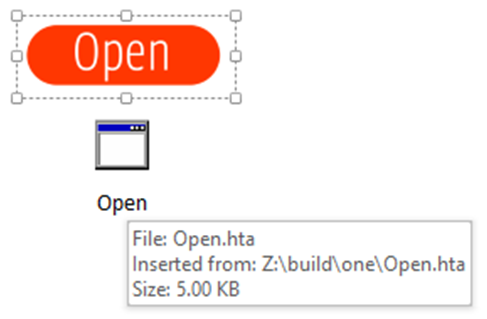
Lurking under the image is a file that will reach out to a malicious URL and download further malware
What do they do once they’re inside?
Black Basta uses PowerShell scripts to gather as much information as possible about the system or network it has landed on, it will pivot around and execute further executables using PSExec, RDP and / or WMI. It will also attempt to disable antivirus, use Mimikatz to further harvest credentials.
The critical flaw in Windows that is allowing the widespread and damaging attacks to take place is through vulnerabilities CVE-2021-1675 and CVE-2021-34527, or the “PrintNightmare” exploit. This occurs in the print spooler service, leading to privilege escalation and / or remote code execution. Black Basta harness this to deploy the Cobalt Strike beacon that allows a persistence mechanism and the ability to deploy further payloads.
Inevitably the end goal is encryption and exfiltration of data (through rclone, interestingly), and a cursory sweep of volume shadow copy deletion to inhibit recover even further.
Desktops are defaced with the group’s branding, and text documents are scattered in affected directories with instructions on what they want you to do next.
Recently a Linux variant of the malware was spotted in the wild, targeting EXSi hosts. This is not just for Windows environments! And as you can imagine, hitting a core Hypervisor can be absolutely devastating to an organisation.
Tactics, Techniques, and Procedures (TTPs)
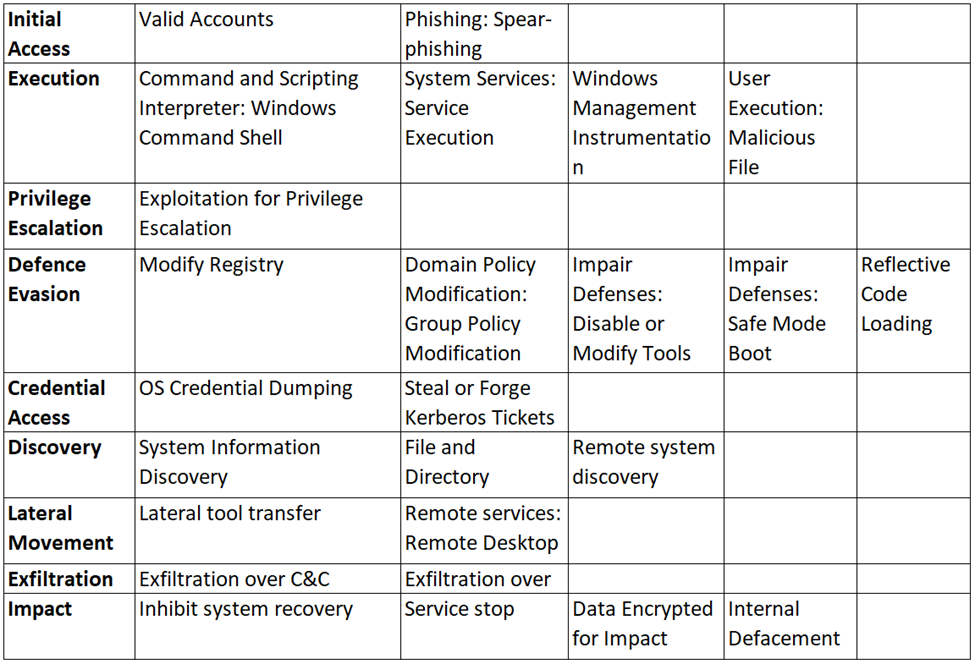
What can be done to mitigate?
The key point of infiltration here is user interaction. The use of OneNote files has caught people unawares. Combining that with references to Office 365, broadly named files and legitimate looking usernames can provide the right mix of confidence and mis-understanding to proceed.
Cyber Awareness training including educating colleagues to never open attachments without a complete understanding of what they pertain to, giving extra attention to external senders.
In addition, preventing such emails from ever reaching their destination is even more effective. Is it usual for third parties to email unexpected and unrequested files? If not, don’t let them in.
BlackBasta leverages WMI, PowerShell and the Remote Desktop Protocol. Prevent these from being executed on non-critical network endpoints and the ability to pivot around the network or even perform reconnaissance is severely hindered.
Patch patch patch! We have seen that Black Basta leverages the PrintNightmare exploits to gain a foothold on a victim network. It only takes a second to pivot to another methodology, so ensuring all operating system and applications (especially antivirus) are kept completely up to date.
Ransomware encryption can be mitigated with isolated and up-to-date backups which can be restored once the network is safe. Data theft is much harder to row back from. Consider implementing Intrusion Detection systems (IDS) or upgrade to Next-generation Firewalls (NGFW). These platforms will monitor traffic at a deeper level and in real time to detect and prevent the egress of unauthorised data from emerging threats.
Help. I’ve already been infected with Black Basta
Immediately disconnect the infected computers or laptops from all network connections.
In a very serious case where the ransomware has already taken hold on multiple hosts, consider whether turning off your Wi-Fi, disabling any core network connections (including switches), and disconnecting from the internet might be necessary. An ideal move here is to block all internet traffic, allowing key services through one-by-one. But the ability to do this can depend on your business and your systems administration setup.
Reset credentials including passwords (especially for administrator and other system accounts) – but verify that you are not locking yourself out of systems that are needed for recovery.
Monitor network traffic and run antivirus scans globally to see where else has been hit. Any log preservation is crucial at this point, so be sure to retain them as quickly as possible in a safe location.














