I was recently on a test where the client’s API used a custom authentication scheme to add a SHA256 HMAC dynamically on each request, based on the URL, time, and message body.
My normal go-to for API testing is Postman (especially when your client is lovely enough to give you definitions you can import directly) connected to Burp as the proxy for later manipulation of requests. Now, you can write pre-request scripts in JavaScript directly in Postman, but it’s more useful to do this in Burp so you can leverage its Scanner and Intruder modules to make short work of finding input characters that break the API in interesting ways.
There are several other examples of doing this floating around, but in my case I had to handle URL encoding, body extraction and timestamps as well, so hopefully you’ll be able to adapt my (admittedly not very pretty) Python to suit your needs, even if it’s not a HMAC header you’re after, e.g. extracting a CSRF token.
1. Grab the Python code from our Github repo at https://github.com/pentestpartners/snippets/blob/master/hmac.py and save it to your local machine as hmac.py.
2. Edit it to add your HMAC secret, or modify to your needs
3. Go into Burp > Extender > Add Extension > Select Python from the dropdown, browse to the saved file, and complete the wizard.
4. You should see it loaded successfully:
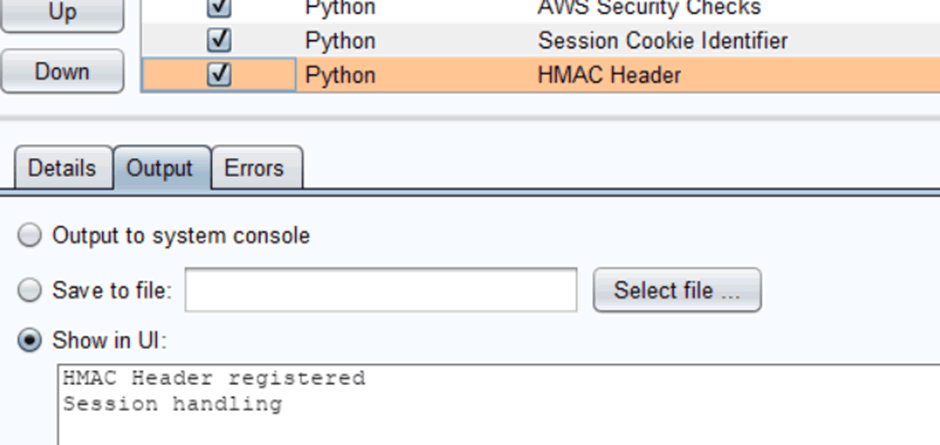
5. Go into Burp’s Project Options tab, then Sessions
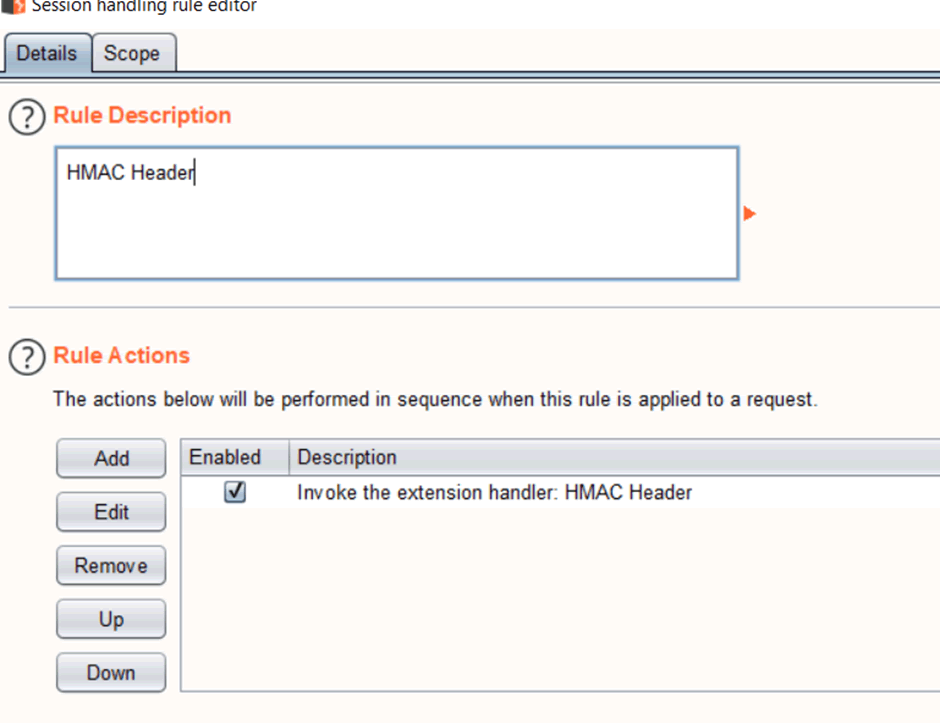
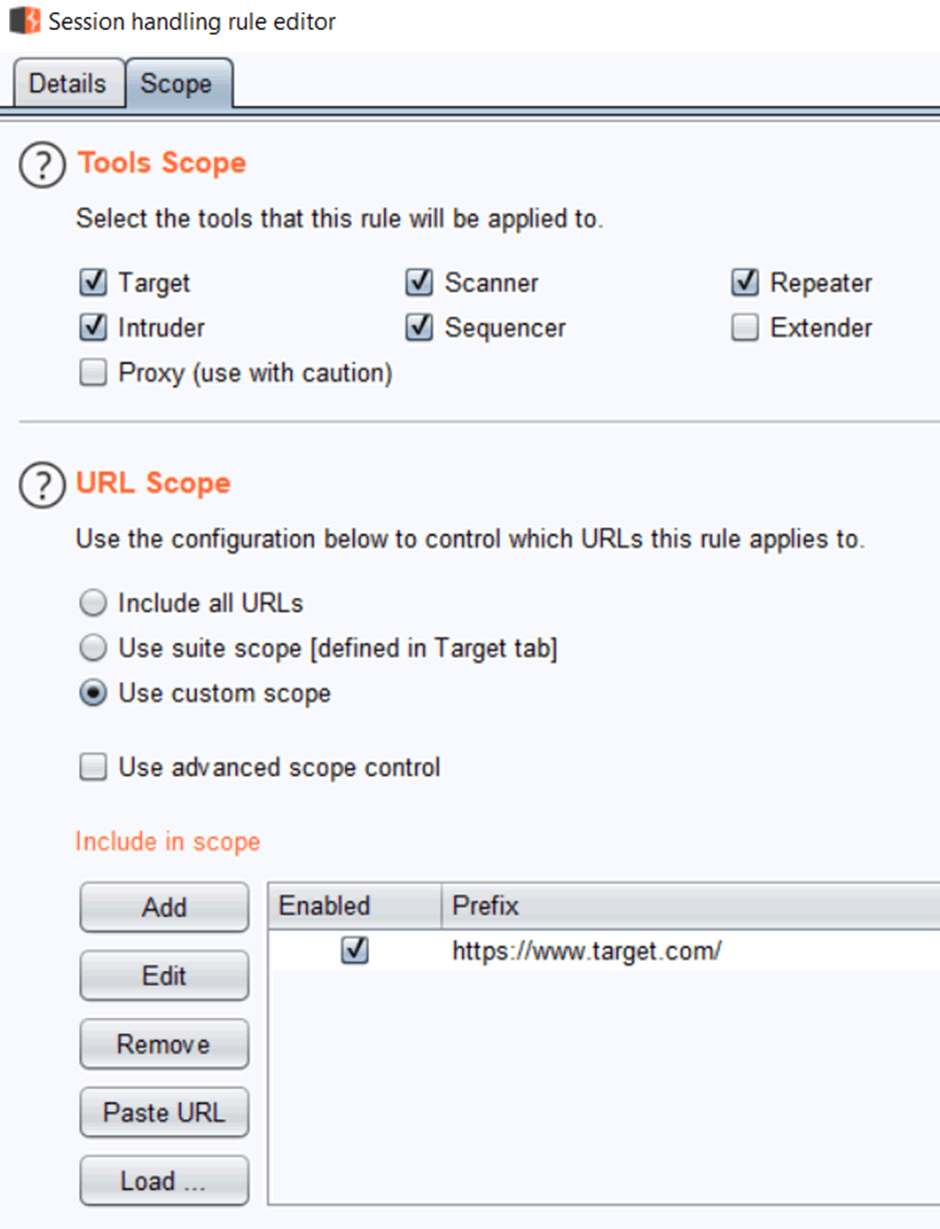
6. Click Add, call it HMAC Header, add a rule action to Invoke the extension handler “HMAC Header”. On the scope tab, add your target URLs and Burp modules:
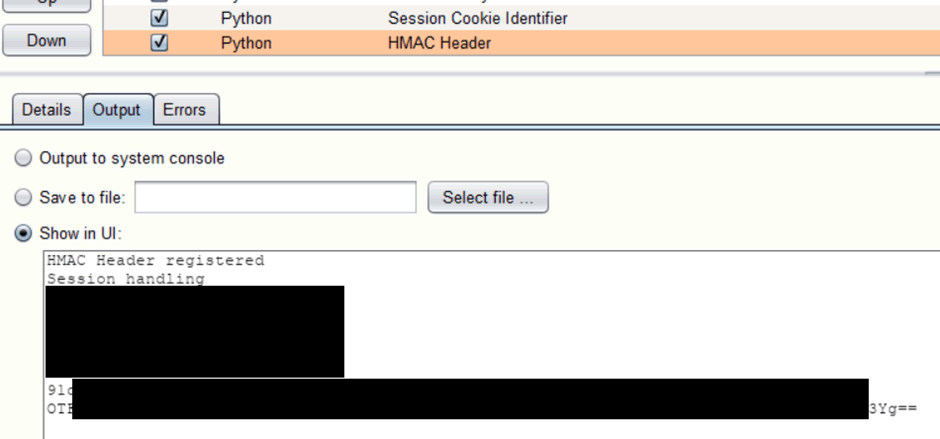
7. You should find the header automatically added (say in a Repeater request) and some output under the Extender tab confirming some of the computed values:
Conclusion
There is lots of flexibility when using Burp to craft bespoke session handling that make it easy to add custom authentication headers or extract and reuse things like CSRF tokens. Hopefully this example shows you that it’s relatively straightforward to use too, and need not hold you up on your next web app test with slightly unusual requirements.














