When a user forgets their password, they often have to involve IT support, and this incurs a significant cost for IT departments. In an attempt to reduce these costs, many organisations have implemented self-service type mechanisms to reset a user’s password based on previously provided memorable information.
So, what’s the problem?
An obvious place to run these password reset mechanisms is on the login screen. The problem is, most of them simply run a locked-down browser in the same context as the login process. They don’t usually authenticate the server, and sometimes don’t even use transport encryption.
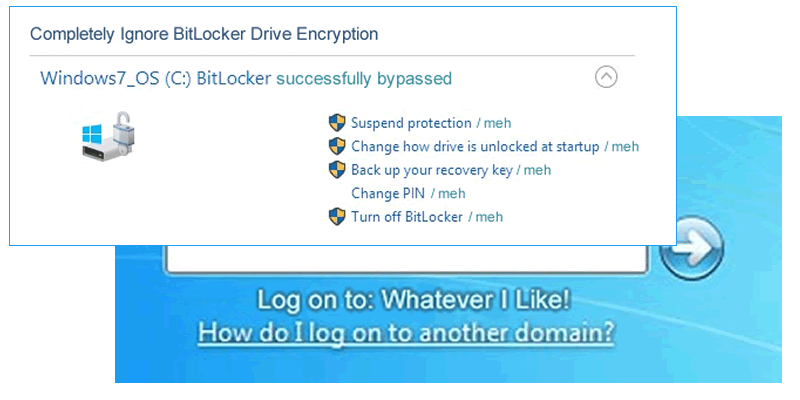
This will even work on an encrypted laptop, provided the organisation uses BitLocker without a boot-time PIN, the laptop encryption and local authentication mechanism can be totally bypassed. Hence the need for a boot-time PIN, but that’s for another blog…
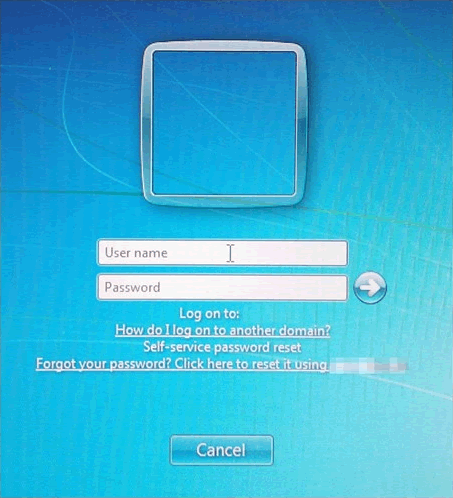
When a user clicks on the password reset link, the laptop will attempt to lookup the IP address of the password reset web server, and request the self-service reset page.
How the attack works
It would be possible to ARP spoof or otherwise MitM these requests, but in a stolen laptop scenario, an attacker could simply plug a network cable into their hacktop and set up a DHCP, DNS, and web server.
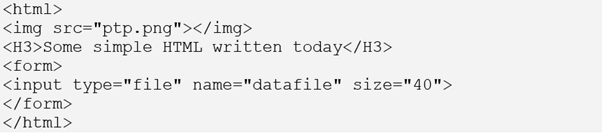
So with some simple HTML, we can return a simple web page back to the stolen laptop.
When the “Forgot your password…” link is clicked, the above HTML is returned instead and rendered in the locked-down browser:
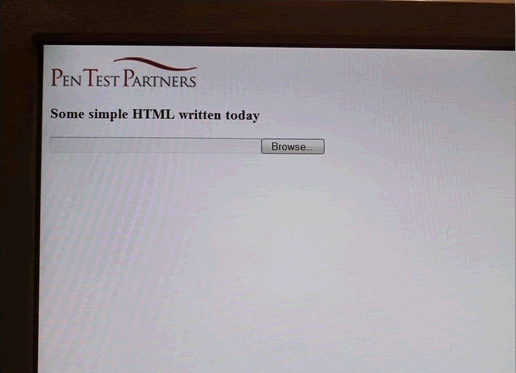
The Windows login process runs as NT Authority\System, so when the Browse button is clicked, it opens up a common file dialog box running as SYSTEM. At this point, an attacker has access to all the files stored on the device, and has bypassed the laptop’s BitLocker encryption.
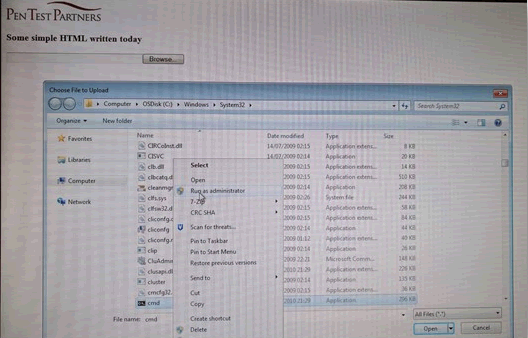
In order to bypass the authentication mechanism, the attacker can browse to Windows\System32 and run cmd.exe. When cmd.exe runs, it’s possible to simply make a new local administrator user, use it to log in as normal, and bypass the windows authentication mechanism.
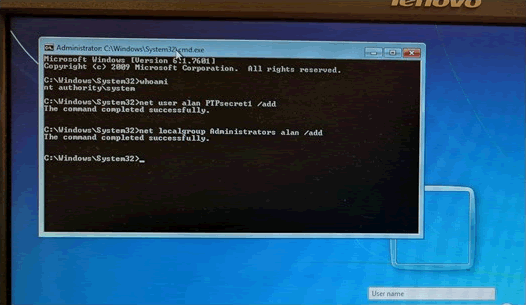
If the stolen laptop was part of a domain, it may be possible to recover cached credentials and even connect to corporate infrastructure.
Advice
- Use boot-time enhanced BitLocker PINs
- Get your forgotten password mechanisms tested
When testing the forgotten password mechanism, the locked-down browser should check the SSL certificate of the reset password page, and not load if there is a certificate mismatch.