During our recent research on the Lovense Hush, we also looked at the smartphone companion apps that allow one to remotely control the devices. This can be either directly over Bluetooth Low Energy or remotely using the online ‘Body Chat’ app. Hence, one can have remote control sessions with partners and others in other parts of the world.
BLE offers a relatively “local” (and by local, that’s up to several hundred meters with a high gain antenna) attack vector but obviously any applications on the internet itself are far more exposed to hacking attempts.
Security of the very intimate data used by smart adult toys will be of concern to many users. The manufacturer, Lovense, reassures users in their privacy statement:
“Absolutely no sensitive data (pictures, video, chat logs) pass through (or are held) on our servers”
and
“we encrypt the data before passing it along to your partner”
We found that this was not the case. It’s bad enough not using TLS, but totally unacceptable stating that the data is encrypted, then discovering that it isn’t.
Chat data not encrypted
During our research, we found that although video appears to be encrypted when using the Body Chat application, chat data is not and can be retrieved in plaintext by an attacker that is able to intercept traffic between you and Lovense’s servers – for example your employer, your ISP or your government. They could also, in principle, be stored and viewed by Lovense as they are sent to servers under their control.
Traffic is sent to im1.lovense.com.com (173.192.179.112) over Websockets:
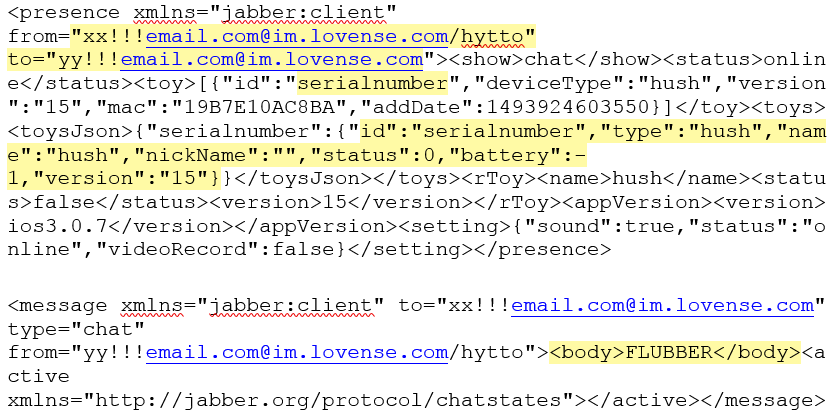
The chat application uses the Jabber protocol and sender & recipient email addresses, details of the toy in use (including serial number) and the contents of any text entered into chat. These are all readily viewable by anyone able to intercept your network traffic.
User advice
We recommend that you stop using Body Chat for personal, identifiable or sensitive communication as this vulnerability is still in the current version of the Body Chat app.
Use the Lovense Remote app instead, assuming it supports your particular device.
Disclosure timeline
As usual, we disclosed these findings privately to the vendor.
…and as usual, disclosure was yet another train wreck, see below:
6th May 2017 – Initial email to Lovense.
8th May 2017 – First response from Lovense indicating they are investigating.
29th May 2017 – Follow up to see if Lovense have been able to reproduce.
31st May 2017 – Lovense indicate a fix should be available in July.
21st July 2017 – Second follow up to check on progress, indicate public disclosure is likely mid-August.
22nd July 2017 – Lovense indicate that release has slipped to August and that Lovense Remote will eventually replace Body Chat.
18th October 2017 – Public disclosure














