There have been many attempts at making key logging devices or software over the years, however, whilst a DIY solution is usually made from large Raspberry Pi devices or Arduino boards, the KeyLogger PRO offering from Maltronics has raised a few eyebrows with regards to the wealth of features available to users in a small device footprint.
This KeyLogger PRO device has interesting features, such as:
- Connecting to the device over WiFi (using WPA2)
- Viewing keystroke data over the air (via device WiFi)
- Sending keystroke data over SMTP in email reports
- Sending keystroke data over UDP to a server
Of particular interest, is the new UDP streaming option, as well as reporting via email.
The KeyLogger PRO is measured at approximately 1x1cm and shown in the image below is how it compares to a USB keyboard connector in a standard sized laptop:
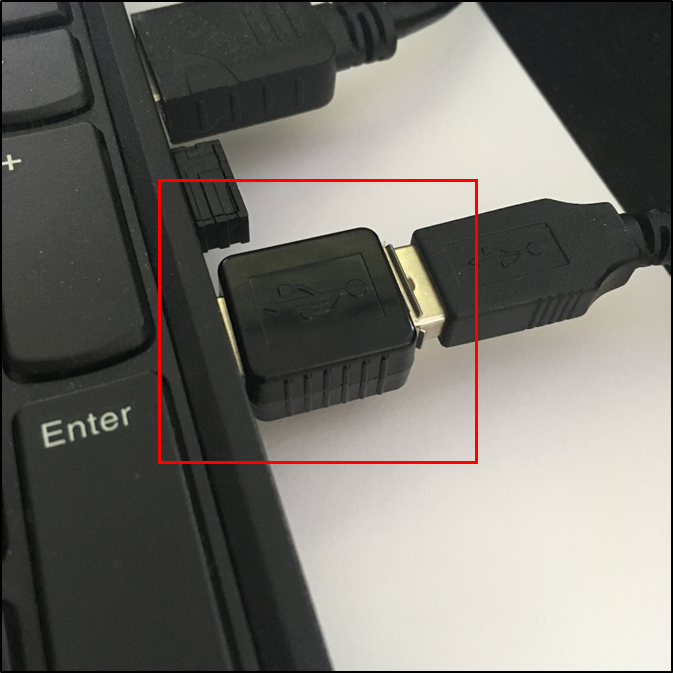
Figure 1 – The device has a very small footprint
It would be difficult for a user to spot the presence of this hardware on their computer, for example, if it was under a desk. The device could be hidden inside a keyboard, if needed, however, the company provide a smaller device for this. It is even more difficult to identify the device at the software level, however, this will be covered later.
KeyLogger PRO Web Application
The Device Settings
The KeyLogger PRO device comes with its own web portal management system that can be connected to via your mobile device or desktop browser. The device comes with firm instructions to set the access point security from the default open wireless SSID, and connecting to the device, allows access to the settings area:
- Device Access Point Settings
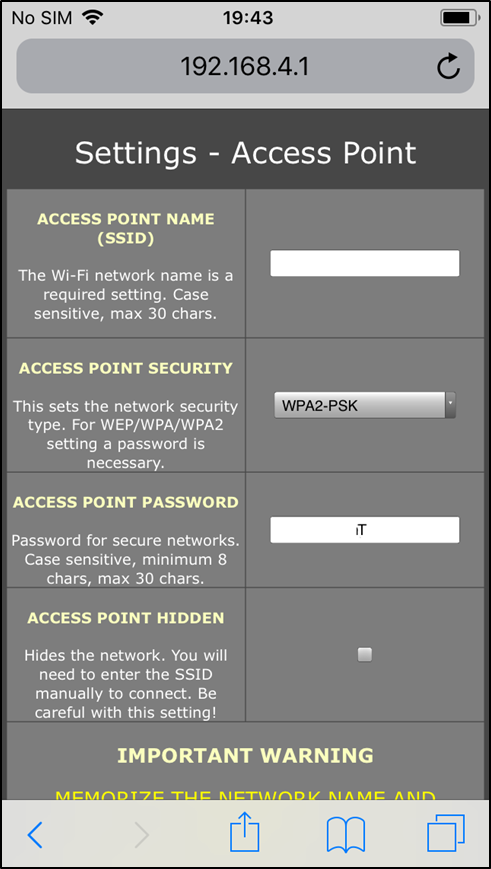
Figure 2 – This is where the device SSID and password are set
The above setting shows how to connect onto the device. The attacker could connect to the device SSID and browse to 192.168.4.1, to retrieve the settings pages where they can view saved keystroke data and change further settings.
- Key Logging Settings
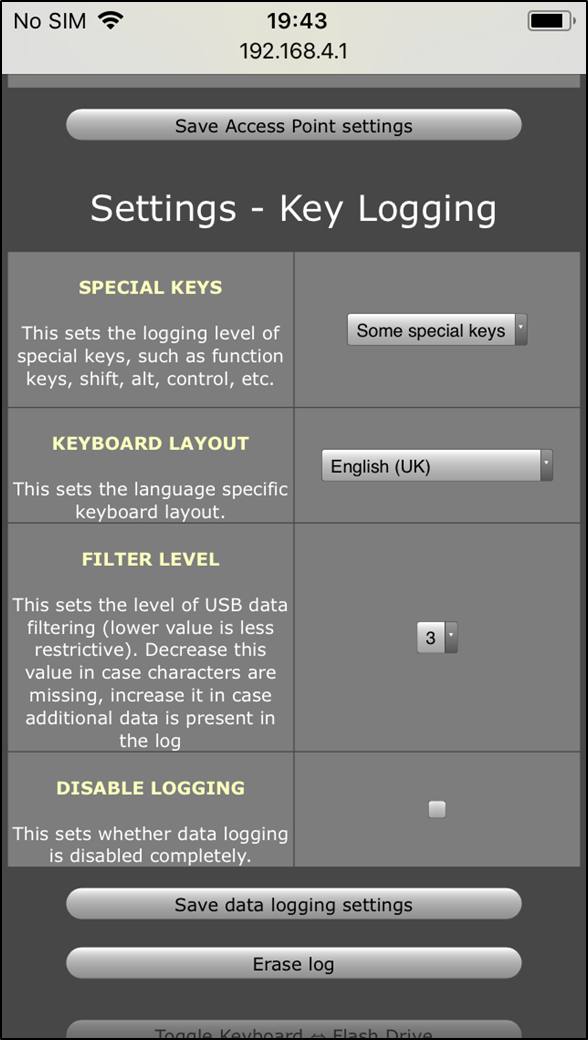
Figure 3 – Keylogging settings to determine input type
- Device Email Report settings and attack
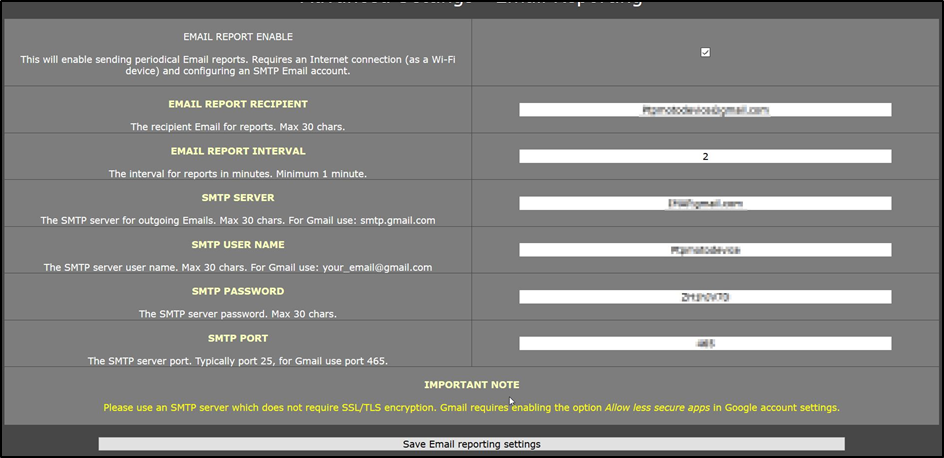
Figure 4 – Where the sending SMTP settings are configured
Attack Scenarios
Sending keystrokes over SMTP
Using the functionality provided by the device, an attacker can configure SMTP settings to send email reports of any logged data to their email account. The polling interval (set as 2 in the image above) means that the data log will be sent every two minutes. The only drawback to this is that as long as the device has an active Internet connection, it will send the log file every two minutes despite there being no new data. A less noisy approach would be to only send the file if there is new data from the last submission.
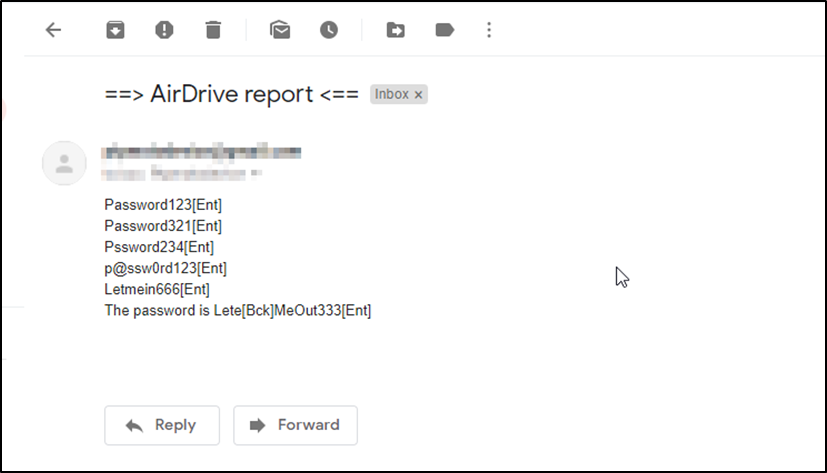
Once the victim enters any data via the compromised keyboard. An email will be received providing data as shown in the example below:
Figure 5 – Email report details with logged keystrokes
- Device UDP Stream Settings and attack
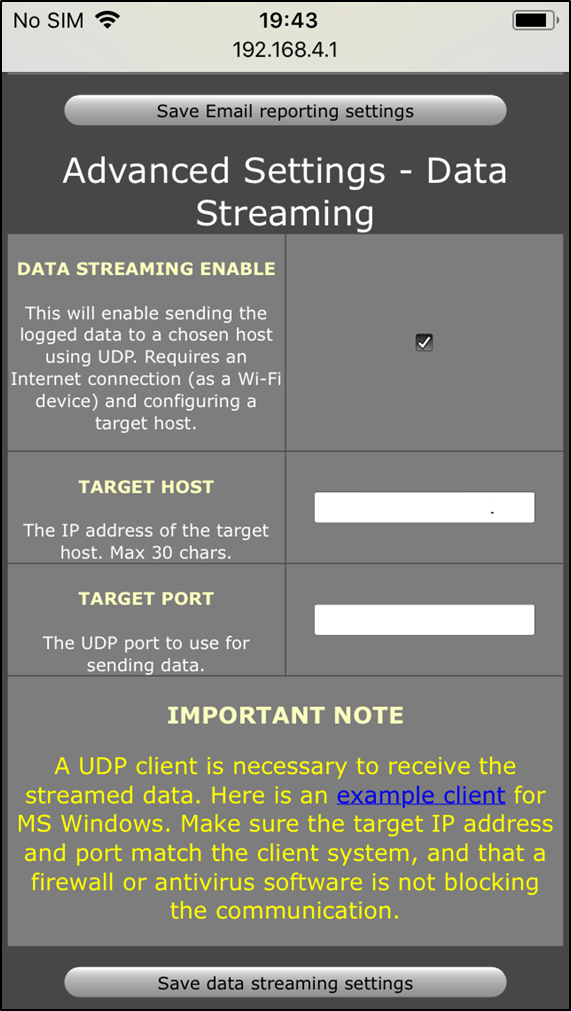
Figure 6 – Configure an internet facing UDP listening server
Sending keystrokes over UDP
An attacker can deploy an Internet facing Virtual Private Server (VPS) and set up a UDP listener in tcpdump to retrieve the key logger stream. When an unsuspecting user presses keys on the keyboard, the data is streamed in real time to a UDP listener, providing the following is in place:
- Internet connection (over WiFi) configured on the keylogging device
- A standard keyboard without complex drivers such as, Gaming keyboards
The device is not able to collect data from a separate number keypad either, however, a large amount of keystroke data can still be retrieved using this easily implantable device.
The following tcpdump command can be used to listen on the desired port configured on the device and display the data sent:
sudo tcpdump -l -n -i ens3 dst port 25998 and inbound -s0 -vvv -w keylog.pcap
The following screenshot demonstrates the plain text sent in the UDP stream. The keylog.pcap file was opened in Wireshark to view the raw data in the UDP packets:
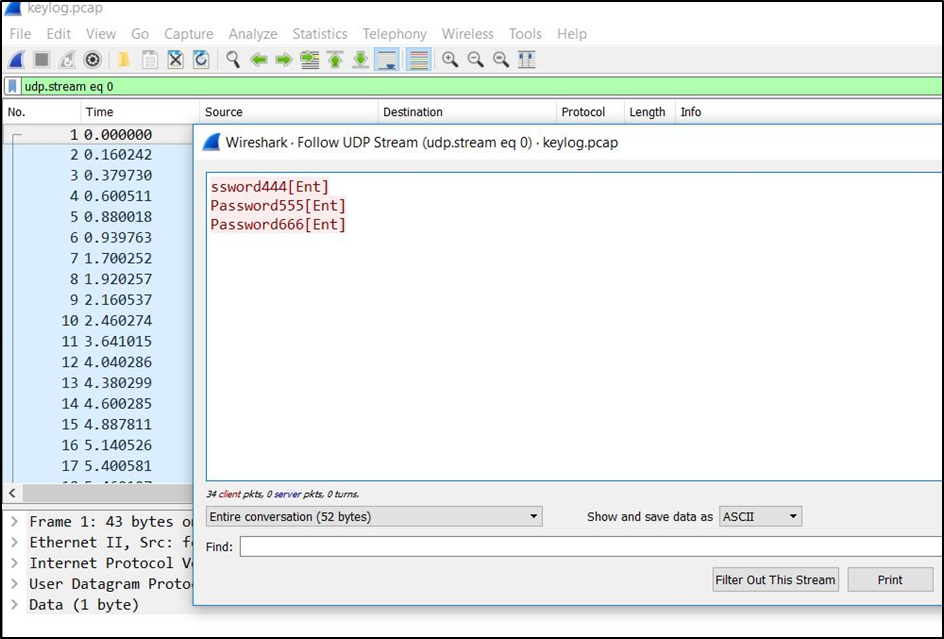
Figure 7 – Each character is sent in different UDP packets as it is sent by the device
Device Identification
Does this device show up internally?
Due to the device being hardware based, the following analysis was conducted to identify if the device shows up anywhere on a Windows 10 system.
Device Manager
Within Device Manager, the settings for the installed USB Composite Device are displayed. From the image below, there is limited information available:
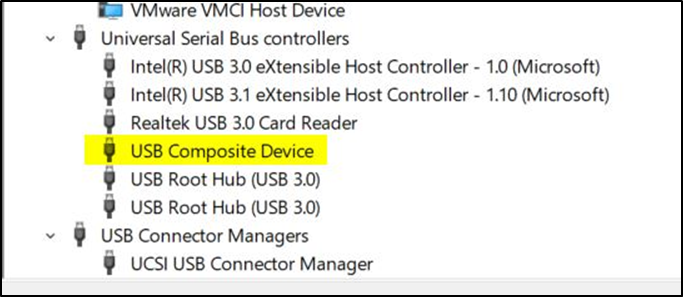
Figure 8 – No malicious devices identified
Further information can be viewed by right-clicking on the USB Composite Device.
The following information was displayed when the KeyLogger PRO was plugged in along with a standard USB keyboard:
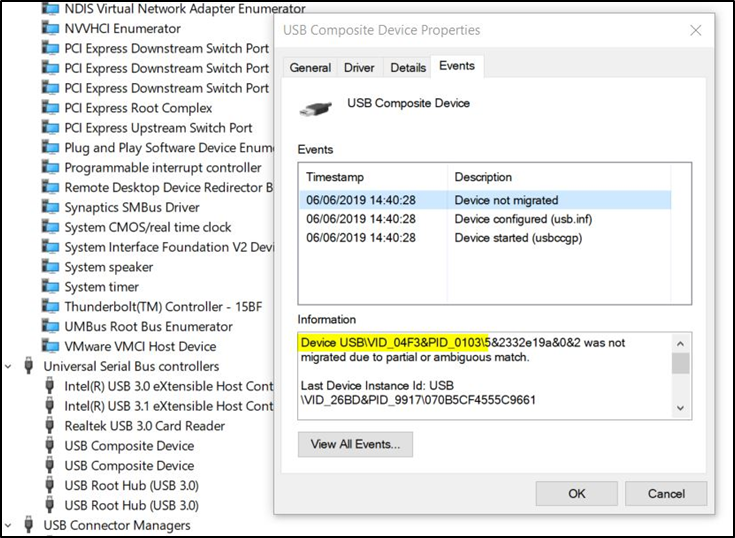
Figure 9 – VendorId is disclosed in Device Manager
According to the documentation on enumeration of composite devices:
The ‘Last Device Instance Id’ variable holds interesting data that could help identify a rogue device. The above site mentions that the following format could reveal further information about the device drivers:
USB/VID_IdVendor&PID_IdProduct
Looking up the VENDORID or ‘04F3’ from the Device Manager image above, reveals that the device could be any one of the USB drivers from the manufacturer ‘Elan Microelectronics Corp’. The list below demonstrates the range of drivers associated with this VendorID:
- Wired Mouse
- Wireless Mouse
- Wired Keyboard
- Wireless Keyboard
- Touchscreen
Interestingly, the KeyLogger PRO device does not appear in Device Manager when it is plugged in to a USB socket. Device Manager only registers the VendorID of the USB keyboard that is plugged into the key logger and not the key logger device itself.
This makes it very difficult for an IT professional to identify if USB activity that triggered an event could be a legitimate USB device being unplugged and reinserted, or a malicious attempt at placing a key logger on the network.
Further Investigation
Third-Party Software
The “Event Viewer” within Windows, offers no further information, as USB activity logs are disabled by default, however, after logging is enabled, it records every action with regards to USB devices, and it can be confusing to sift through. Some third-party security software may be an option for companies with larger budgets, however, free software can be used to log USB device activity, particularly plug and unplug events.
USBLogView
http://www.nirsoft.net/utils/usb_log_view.html
USBLogView can monitor USB devices as they are plugged into a computer or removed and also write these events to a log file and store them locally on the PC.
The software catches plug and unplug events and neatly displays them in a fashion that is understandable with key data on any device that was used, as shown in the image below:
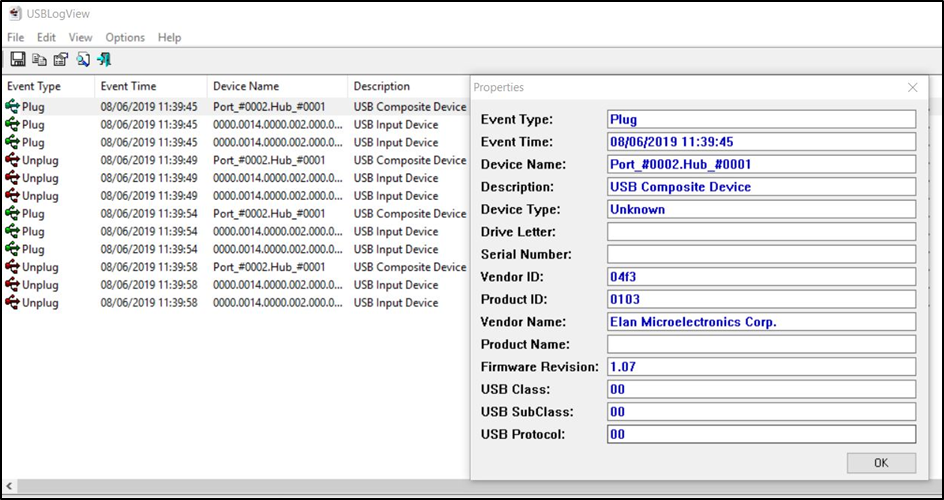
Figure 10 – Useful information from USB activity
The resulting log file can be viewed as a Comma Separated Values file in Excel:
Figure 11 – Clean log data from USB activity
Unfortunately, whilst this data is formatted in an understandable list, it still does not confirm the presence of a key logging device, however, it does provide data that can be used later in any forensic work.
Log File Changes
If the organisation has the use of SolarWinds, an alert can be set up to report on the changes to the size of a file or when it has been modified. In theory, an alert could be made on the USBLogView log file when a new entry is written, as a result of a plug or unplug event. This would alert a System Administrator to the possibility of USB devices being plugged in or unplugged.
Further complications occur when trying to identify the source of the USB activity from suspected issues with a log file increasing.
This issue could potentially be solved with each log file being named on a share as the hostname of the PC. Therefore, when any alert is raised, the notification is more useful to the IT professional.
Password Managers
If the organisation implemented a password manager solution, this would help to reduce the impact of stolen passwords, due to the auto-fill functionality in web pages, and the ability to copy and paste passwords from the software without typing.
The main flaw with this idea, is that if the main passcode for the password manager is compromised, it could potentially have a bigger impact if the user’s password database is accessed.
Will Antivirus provide appropriate protection?
Investigations into how EDR (Endpoint Detection and Response) solutions work, reveal that some of them are not looking in the correct place for this device. For example, traditional AV vendors check if a memory stick (removable storage device) is inserted. The AV solution scans the device for malicious software before the user is allowed to access the contents. Most corporate endpoint solutions, such as Symantec and Microsoft Anti Malware, operate this way.
Other “Anti-Key Logging” software claim to stop key loggers, however, on further reading into their claims, they only prevent software that runs on the disk from reading keystrokes as the software encrypts as you type, however, this is on the operating system level.
The unique advantage to a hardware device key logger is the ability to sniff data over the wire before it even reaches the operating system or touches the disk or memory.
To confirm this, the device key logger was run in a system loaded with some popular corporate EDR solutions.
| Vendor | Success Rate |
| Microsoft Windows Defender (Windows10) | Failed to Detect |
| ESET Endpoint Security | Failed to Detect |
| Morphisec Endpoint Threat Protection | Failed to Detect |
| Spy Shelter Silent 11.7 Anti-Key Logging | Failed to Detect |
In all the cases above, data that was input by the user was successfully exfiltrated to a receiving server or sent as a report over email.
The most surprising revelation was retrieving data from a computer with Anti-Key Logging software installed, which claims to encrypt each keystroke. The software is shown below, along with the text that was input to Notepad:
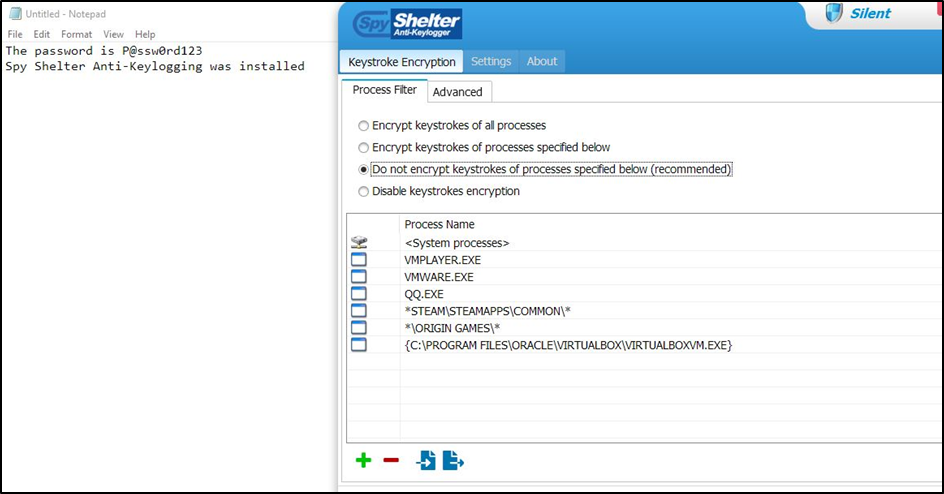
Figure 12 – Spy Shelter Anti-Key Logging software
The basic (free) account “prevents” key logging by encrypting keystrokes in processes. From the list in the image above, notepad.exe was not in the exclusion list.
An email report was received with clear text data as shown below:
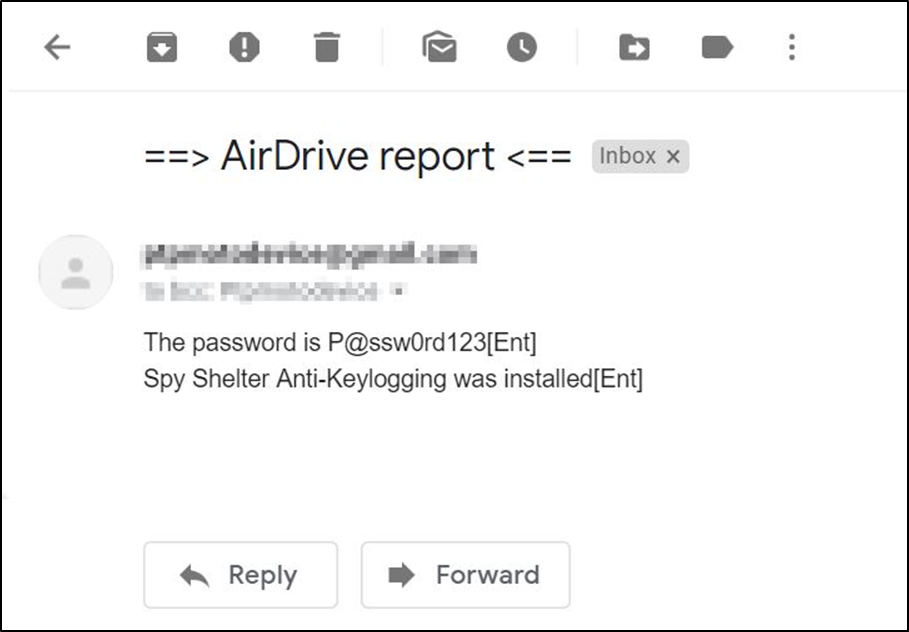
Figure 13 – Email report from PC with Spy Shelter installed
The KeyLogger PRO device is not picked up by the Spy Shelter software because the software is looking for key logging software and attributes of key logging software and not hardware devices.
Will a firewall stop the traffic?
The device comes equipped with the ability to configure your own wireless network to provide it with Internet access. If a wireless hotspot can be configured on a phone and the device is in range, it would be possible to exfiltrate data without it being detected.
Similarly, if the corporate infrastructure provides a guest WiFi network without proper filtering controls, this would be very favourable to an attacker.
The BIOS and Device Manager
An IT administrator can completely disable USB ports in the BIOS or the Windows Registry of the computer, however, if an external keyboard is required, this would need to remain enabled and the attack vector would still be valid.
USB ports can be disabled in the Device Manager, however, with every conceivable setting that allows a port to be disabled, the requirement of the user to conduct their work using a keyboard will override the case for security.
Conclusion
This is a particularly devious and potentially devastating attack vector for larger organisations with hot desking staff, or free flowing open plan offices. Not many staff will instantly detect this small device connected to a PC. It presents a strong attack vector for consultants conducting Red Team engagements due to the rich feature set, low physical footprint and almost invisible nature of the device from the operating system side.
How does an organisation protect against this?
The organisation could start to think about blocking access to the USB ports and, whilst that would certainly work in an environment where the majority of users use laptop computers with inbuilt keyboards, the same cannot be said for most office computers that are laptop docking stations or desktop PC-based with a wired keyboard and mouse.
Training and staff awareness session surrounding how to identify potentially malicious devices connected to a computer is a good start and would certainly require the user to have clear access to view the peripherals that are connected.
Locking the computer up in a cabinet under the desk is a common protection method that could work providing it is always kept locked. Something that is not always adhered to in a large busy office with many PC’s needing attention.
Many organisations block the use of USB, however, users still need to use input devices such as keyboards, and most organisations would not spend vast amounts of money on gaming keyboards with complex drivers or functionality.
Network alerts may be triggered if an attacker was using the corporate network to exfiltrate the data log, however, a mobile hotspot would allow an attacker to exfiltrate the data directly without challenge. The wireless range of the device is such that, an attacker can connect onto the device and download the log too, and leave the device connected. By the time the device is found, data submitted by the user could already have been compromised.
It has been demonstrated that the computer does not recognise the continued use of this device, or triggers special events when they are taken from one computer and placed in another. The only real mitigation would be to monitor USB device activity via logs, which requires an in-depth setup in a large office environment; which could prove to have an impact on resources to implement.














