Working in the finance team at PTP I’m constantly reminded just how little attention is paid to hacking and cyber crime in accounting and finance training and education.
When I was studying for my AAT qualification we did a whole module on finance fraud; our obligations, how to spot fraud, etc. but there was nothing on security or hacking.
FYI Jasmine Fiscal is not my real name 😉
However, pretty much from my first day here I was shown just how important my cyber vigilance and understanding are to the business. Why? Because people working in finance are the ideal target for hackers; we’re a direct conduit to the money.
To fill that cyber / finance knowledge gap I thought I’d share some things that will reduce the risk of you being exploited by hackers. These are some basic questions to ask yourself in your daily finance role:
- When you receive an invoice do you check the bank details?
- If it’s an invoice from someone you’ve not paid before; new supplier, the plumber that came to fix your boiler, do you search the web for contact details then phone to confirm the bank details?
- Do you know how to spot a dodgy email that, on the face of it, looks legitimate?
- Do you click on a link in an email, or open an attachment without stopping to think first?
Let me help you answer those questions.
Validating bank details
A simple task, that everyone in Finance or Accounting should get used to, is validating bank details.
If you’re going to be making a payment or regular payments it’s essential that you check the exact account name, sort and account code of every new payee. Trusting the info in an email without checking has led to countless losses for companies, and continues to be a problem.
Make it part of your client on-boarding process.
It only takes a phone call.
Email trust and domain checking
I’ve seen just how easy it is for a hacker (Ms X) to create an email address that looks incredibly similar to an email address you should recognise. For example; if I had a supplier called EcoGreen and their domain (the bit after the @ symbol) could be ‘ecogreen.co.uk’.
If I received an email from ‘finance@ec0green.co.uk’ I may not spot that the letter 0 has been replaced with the number zero.
If the content and details of that email didn’t cause suspicion I might act on the email, making it a successful hack by Ms X and she will now be receiving all the money I think I’m sending to Eco Green. Errors like this can go unnoticed for months.
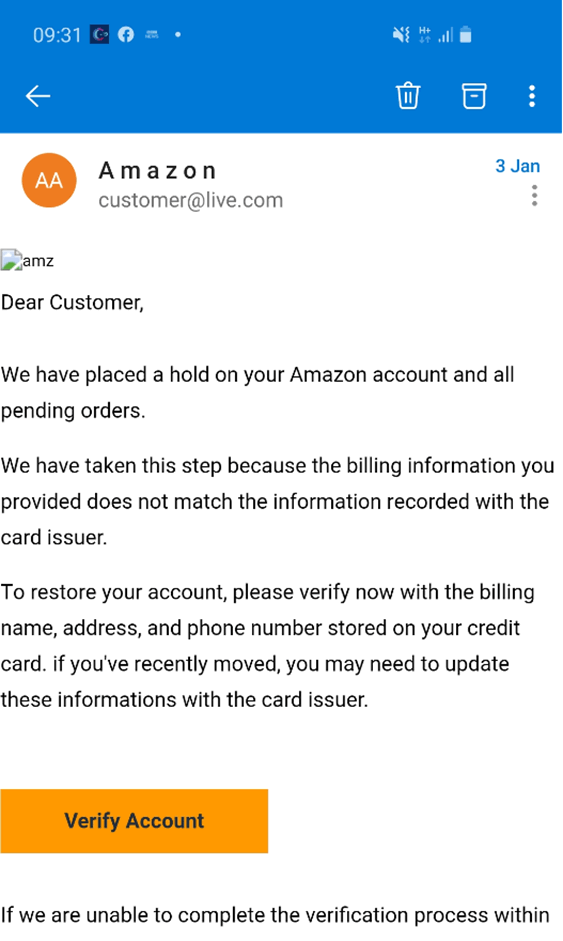
Instincts are definitely your friend. Often I’ll get an email that just looks odd. Maybe the language is not what I’d expect, the greeting isn’t the usual greeting, and what the email is saying or asking isn’t right or as you’d expect.
Sometimes an email that looks dodgy will actually be genuine BUT if your spidey senses do tingle then check it out before doing anything. If in doubt, get in touch with the contact by a trusted phone number, or do an internet search to find the details – DO NOT SIMPLY TRUST THE DETAILS IN THE EMAIL.
It’s always better to ask the question and be wrong than ignore it and be the cause of the company being hacked or held to ransom. Also, an email phish or hack will often threaten something; “if you don’t do that then this will happen!”. This is especially common in private or personal emails. They will try to frighten you to elicit a reaction before you can stop to think or look closely.
I am always suspicious if I receive a threatening email like that, if I ignore it then guess what . . . nothing happens.
How are emails spoofed?
How does Ms X get the information she needs in order to spoof an email like this? Mostly with by internet research. Looking at the company website can provide information, names and even email addresses. There’s also Facebook, Twitter, Linked In; these days it just takes one careless post by an employee and that’s all Ms X needs. For example, a Twitter post by an employee saying something like this:
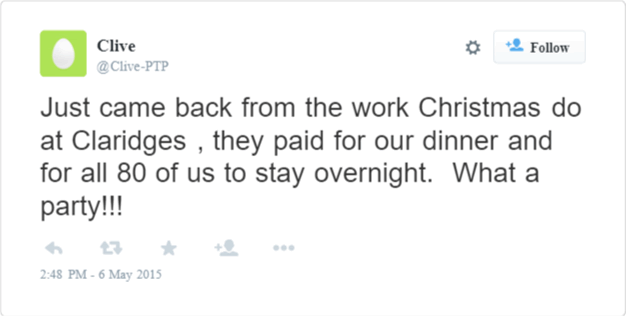
Now, with just 2 sentences Ms X has found out the size of the company, and the sort of bills the company will be expecting to receive and from whom. With a little more digging Ms X finds another employee on Linked In with the job title “Finance Assistant”.
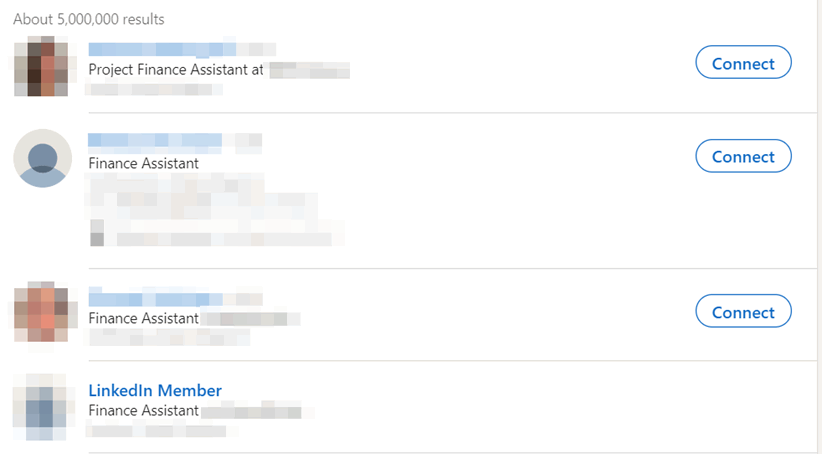
So all Ms X needs to do now is to create a domain that looks like the hotel’s domain, and who would question it?
There’s a phone call for you…
It’s not all IT though, you have the good old fashioned telephone. Ms X just has to call and ask for finance. She could pretend to be from HMRC, for example. If someone phoned you saying they were HMRC who wouldn’t be a rabbit in headlights? This happened to me a while back, the person had done their research and had enough information to sound plausible.
One thing that really should’ve made me suspicious is that he was offering help with a tax issue. Those that have had any dealings with HMRC will know that they NEVER offer help. Just because someone says they’re an authority figure doesn’t mean you can’t challenge them. We teach our children about Stranger Danger, this is not that different.
Potentially in that telephone call Ms X can find out the name or names of the finance team, directors, partners, email addresses, what finance software the company uses, and possibly much more that can be used in CEO fraud or Business Email Compromise.
CEO / invoice fraud
Here is another scenario; if you received an email that, on first glance, appeared to be from the CEO asking you to “just pay this invoice for me”, would you question it? Would you double check the email address it came from?
You receive an email supposedly from the CEO, Mr Smith:
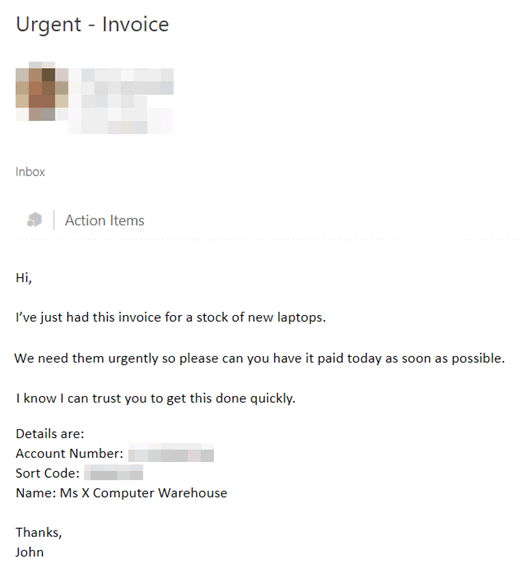
Why would you doubt an email like this? They’re at the top, it’s their business, so you go ahead and pay it.
This kind of fraud is on the rise, helped by the current isolation of workers. In normal circumstances you may ask the person next to you or shout over to the boss, but, with remote working you are less likely to want to bother someone with a call or email and as a result will pay it.
What can you do?
It’s on businesses to ensure that systems are put in place to protect from fraud, phishing etc, but it is also our responsibility as gatekeepers to be vigilant and question everything and everyone, no matter their seniority level.

We have a right to expect our employers to do everything in their power to protect us from fraudsters. We also have a responsibility to do everything in our power to protect our employers from fraudsters.

I think the key things for us in finance teams is (sadly) to have a suspicious mind. Thinking about the business you are in:
- Does your company have email security filters?
- Do you and your team have checks and safety procedures in place?
- Is there a culture of accountability?
If sharing my fails and the lessons I’ve learnt helps just one person out there then I’m happy. Remember;
- Stranger Danger
- EVERYONE is accountable
- Listen to your spidey senses
- Find contact details on the internet – not from the documents sent to you
- If you’re not sure then share your concerns or question it anyway.
Don’t be isolated, especially at the moment during the lockdowns. Use the company messaging software if there is one. If not, consider setting up a WhatsApp group or similar. If you do get caught out then share your experience so others can learn the lesson.














