TL;DR
- Shellbags are Windows registry artifacts that log user interactions with folders even after those folders are deleted.
- They contain timestamps and metadata that help reconstruct user activity timelines.
- These artifacts can be viewed manually in RegEdit or more easily analysed with tools like Shellbags Explorer.
Introduction
Shellbags are a valuable forensic artifact, providing analysts with information about user interactions with folders in Windows. These registry keys record metadata such as folder paths, view settings and timestamps. These artifacts offer insight into what folders a user has accessed, Shellbags persist even if folders are deleted, making them an important artifact for Digital Forensic Incident Response (DFIR) investigations. In this blog post I will detail the significance of Shellbags and their relevance to forensic and incident response analysts.
What are Shellbags?
When you browse a folder in Windows and change the window’s settings, such as altering the size of the folder, changing the window contents view (e.g. by changing to list or extra-large icon view) the information is remembered by Windows for the next time you open the file explorer. Windows must store these preferences somewhere —that somewhere is known as Shellbags.
Where are they located?
Shellbags can be found in the user specific section of the registry, indexed by the user’s SID, with an alias in HKEY_CURRENT_USER for the current user:
User-Specific Shellbags
- HKEY_USERS\<*SID*>\Software\Microsoft\Windows\Shell\BagMRU
- HKEY_USERS\<*SID*>\Software\Microsoft\Windows\Shell\Bags
Current User Shellbags
- HKEY_CURRENT_USER\Software\Microsoft\Windows\Shell\BagMRU
- HKEY_CURRENT_USER\Software\Microsoft\Windows\Shell\Bags
Supporting Files
Shellbag data is also found inside user registry hive files:
- NTUSER.DAT: Located at C:\Users\<Username>\NTUSER.DAT
- USRCLASS.DAT: Located at C:\Users\<Username>\AppData\Local\Microsoft\Windows
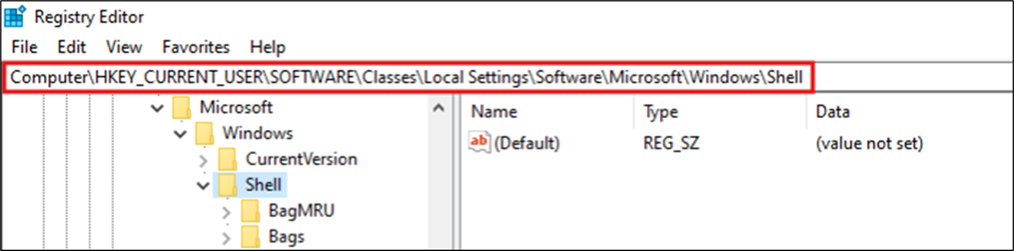
Figure 1: Shellbags Location
Relevance to DFIR Analysts
There are two folders of note inside the Shells folder, these include:
- BagMRU – Maintains hierarchical structure of folder paths.
- Bags – Stores information about each folder, including view settings and timestamps.
Shellbags are a useful tool for forensic investigators and incident responders, because the data stored is persistent, even if the folders have been deleted.
They include clear timestamps that show when a folder was opened or changed. When matched with other basic forensic evidence, this information can be very helpful for DFIR analysts trying to understand what happened on a system.
Analysis of Shellbags: Tools and Techniques
Shellbags artifacts can be analysed manually in a tool like Registry Editor, however, Shellbags Explorer, developed by Eric Zimmerman, makes analysis of these registry keys much easier.
Figure 2: ShellBags Explorer
Using Shellbags Explorer, we can either load an active registry or an offline hive. For the purpose of this analysis, I will load the active registry, but in a real-world investigative scenario, offline hives are more commonly used.
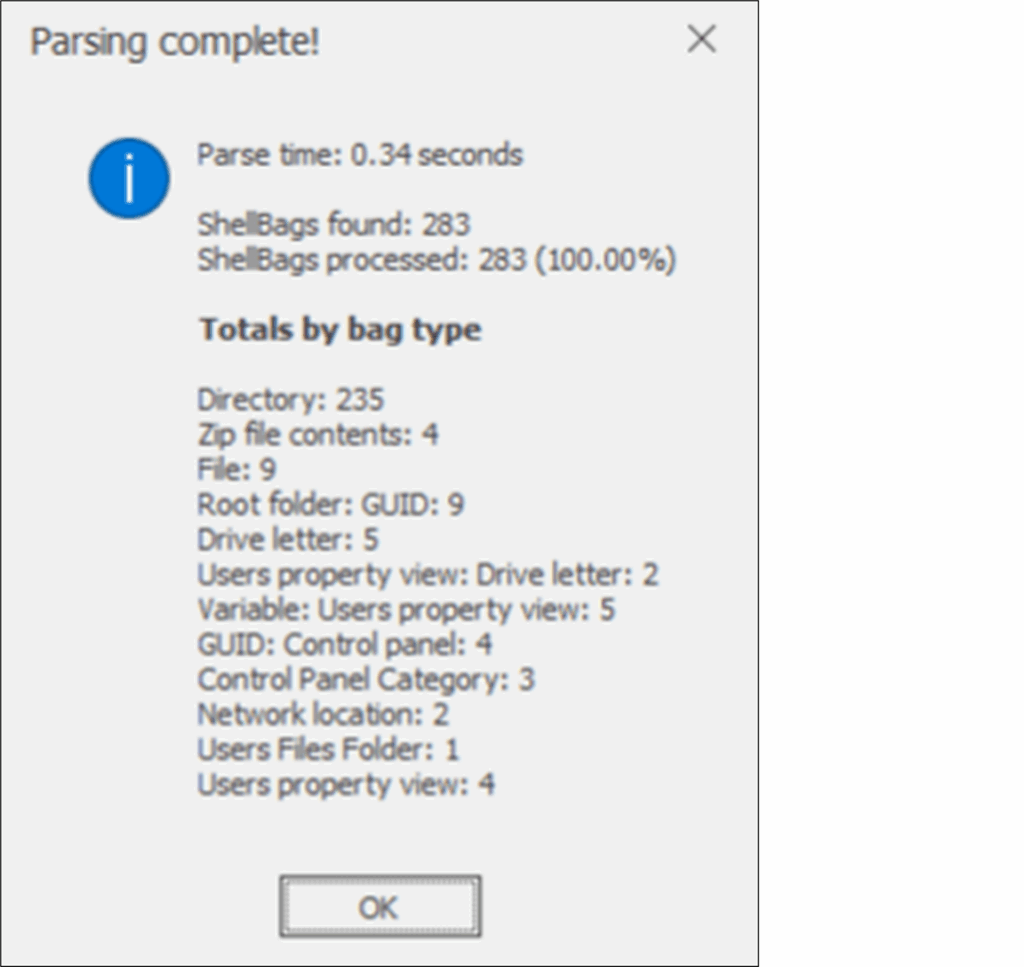
Figure 3: Parsing Summary
Once loaded, we are presented with the above window, which details the amount of Shellbags that were found, broken down into bag types.
For testing purposes, I have created and deleted the following folders:
C:\Users\joseph.williams\Documents\Secret Folder\Don’t look in here\Go away\You won’t find anything\Stop opening me\GO BACK\Secret.zip
However, as mentioned earlier – although the folders, sub-folders and zips have been deleted; reference to them still exists in the Shellbags artifact, meaning that the users attempt to hide evidence that they had accessed these folders is unfortunately for them, futile.
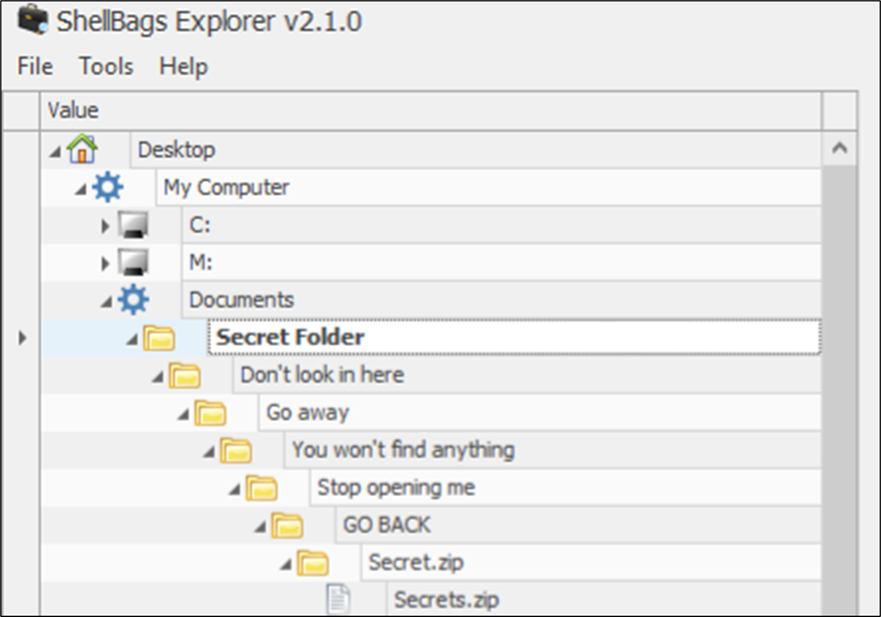
Figure 4: Shellbag Evidence
The above snippet shows that although the folders have since been deleted, their original location and names are still present thanks to Shellbags. We can dig a little deeper into these folders below:
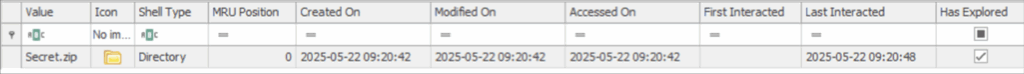
Figure 5: Shellbag Evidence
Above, we can see the name of the folder the user has accessed, the icon associated to it, the shell type (i.e. directory) as well as the created, accessed, modified and last interacted times. We can also confirm that the user has explored this folder.
Looking further into the folder, we can see that the user has traversed through the full directory, eventually gaining access to ‘Secret.zip’.
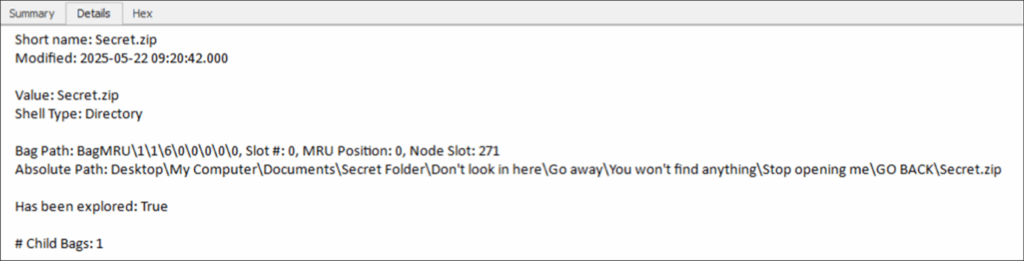
Figure 6: Shellbag Details

Figure 7: Bag Path
Breaking the bag path down
The bag path in a Shellbag entry shows the hierarchical structure of folders the user has interacted with. Each number in the path corresponds to a subkey in the BagMRU registry tree, which points to a specific folder or directory.
- BagMRU is the root key that holds the hierarchical metadata for the folder interactions
- Corresponding numbers – in this case \1\1\6\0\0\0\0\0 shows the sequence of subkeys under the BagMRU key. The trailing 00 00 00 00 groups are null terminators, marking the end of the path.
- MRU Position: A value of 0 usually means this was the most recently accessed folder within its parent. The MRUListEx value orders items like a linked list, showing the sequence of access.
- Node Slot: 271: Refers to a specific location in the Bags registry key where additional folder settings are stored e.g. timestamps and view modes.
These fields allow investigators not just to pinpoint what folder was opened, but also to reconstruct the path taken to that folder. This enables analysts to build a trail of user navigation; reconstructing how a user moved through Windows Explorer.
The NodeSlot integer links a BagMRU subkey to its corresponding view settings. If the NodeSlot key exists and contains a Shell or ComDlg subkey, it is likely that the folder was visually rendered in Explorer.
Looking under the hood
While GUI tools like Zimmerman’s are great, Shellbags themselves are stored as binary structures within registry hives. These binary blobs follow the ITEMIDLIST format, which contains metadata about folder interactions. Here is an example of a BagMRU entry:
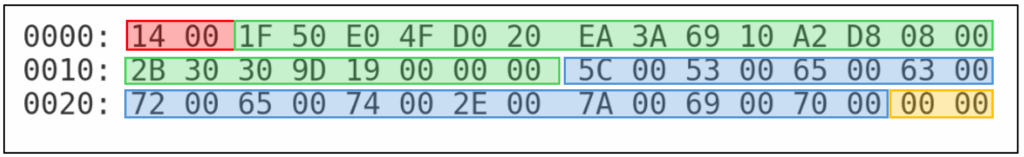
Figure 9: Hex Breakdown
Breaking this down:
“14 00” – The size of the ITEMID entry (20 bytes)
“1F 50 E0 4F D0 20 EA 3A 69 10 A2 D8 08 00 2B 30 30 9D 19 00 00 00 “- Shell item header (identifies a folder object)
“5C 00 53 00 65 00 63 00 72 00 65 00 74 00 2E 00 7A 00 69 00 70 00” – UTF-16 string representing of \Secret.zip.
“00 00”- Null terminator.
Below is a snippet from CyberChef showing the decoded UTF-16 string representing Secret.zip.
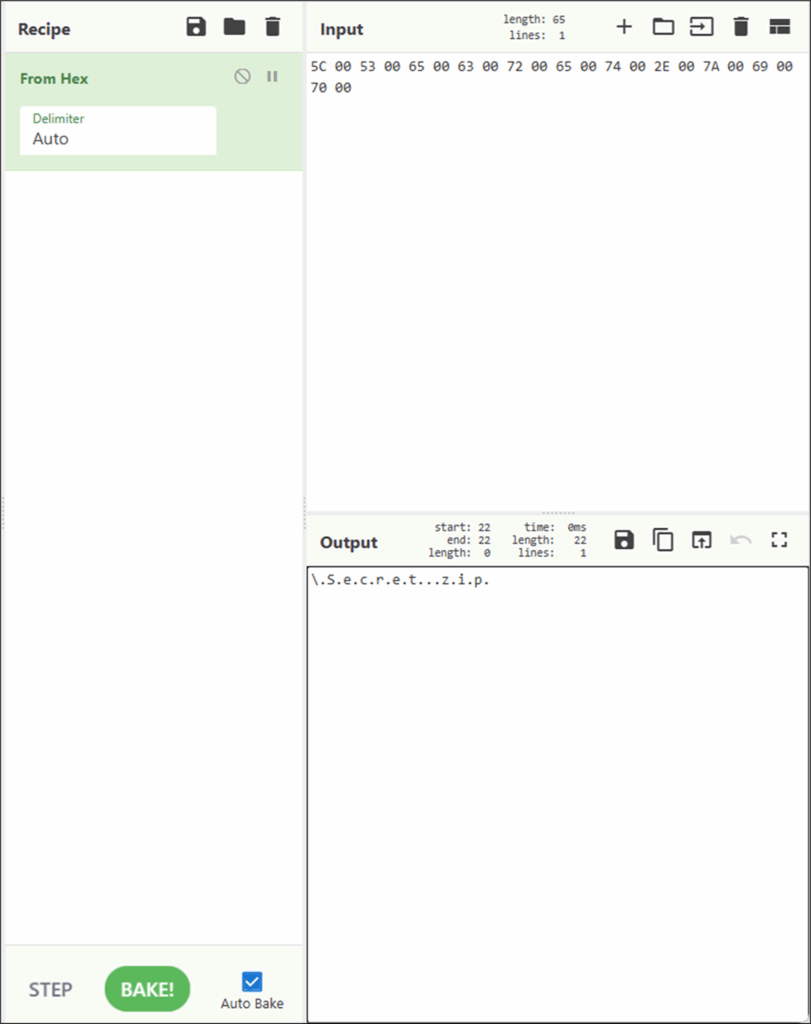
Figure 10: Decoded Hex
From this, even though the folder and ZIP were deleted, we can still confirm that the user browsed into a folder containing Secret.zip.
Where else are they?
It’s not just folders you have created on your local machine, what if someone connects an external device to their machine and browsers folders stored on that external device, or if someone accesses folders in a network location?
Well, accessing folders on your Windows device, wherever that might be will create shellbag entries. Let’s say I am looking to exfiltrate some sensitive files via SMB share using Windows Explorer;
In that case, Shellbags will log the folder traversal, although it is worth noting that most attacker driven SMB exfiltration is carried out with command line tools like robocopy or scripts, which bypass Explorer and leave no Shellbag trail, meaning it is especially important to recognise when Shellbags exist and that their absence may be just as revealing.
Let’s say files have been stored in a folder named ‘Very Sensitive Files’, that is now deleted – can we still evidence that a user has accessed that specific folder?
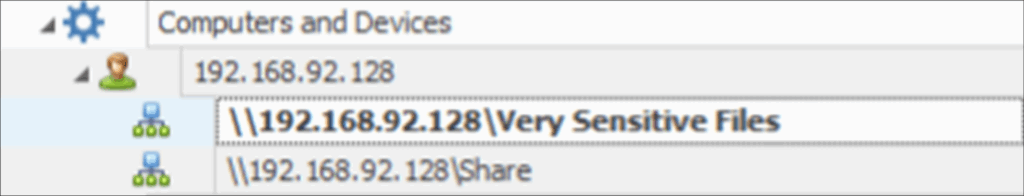
Figure 11: Network Drive Shellbags
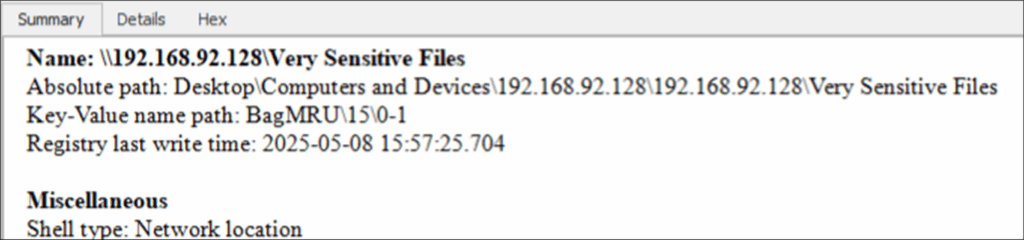
Figure 12: Further Information
Moving on from Shellbags discovered from a network location, what about an external device that has been connected, or a drive location that once contained data but is no longer existent?
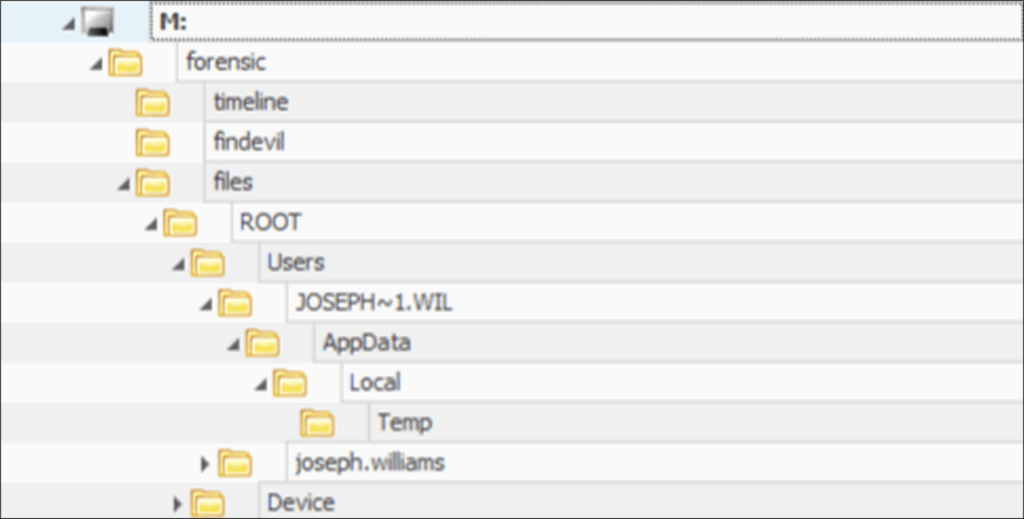
Figure 13: MemProcFS Drive Shellbags
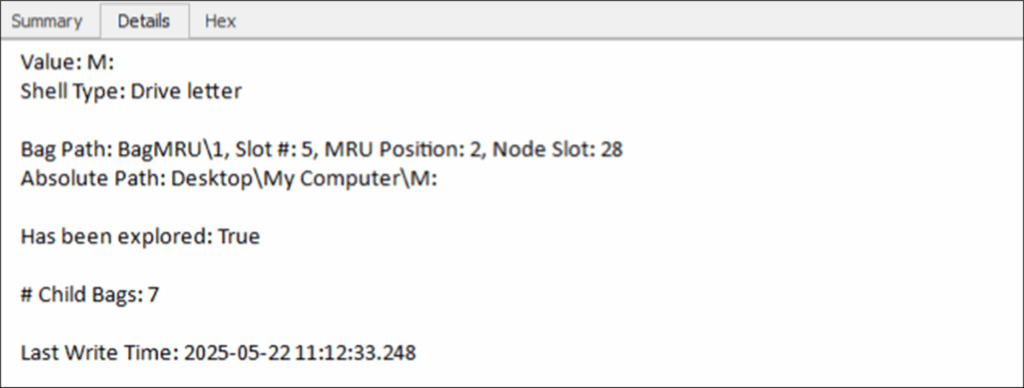
Figure 14: Drive Traversed
When performing memory forensics, MemProcFS is a useful tool that allows an analyst to mount a memory image and simply traverse through the image as if it was a connected device. Now, in relation to Shellbags – this memory image was mounted via MemProcFS and has since been disconnected – but Shellbags allows us to see exactly what folders were interacted with and when.
Limitations of Shellbags
Although useful, there are limitations to Shellbags, mainly that they only record folder level interactions and not specific file accesses. These artifacts can also be lost if a user profile is deleted as it sits within the user registry hives. Like many other forensic artifacts, Shellbags should be paired with other artifacts to build a comprehensive timeline of user activity.
It is also worth noting that Shellbags are only updated when a user views folders or zip archives through Windows Explorer, or through an open/save dialog.
If a user traverses through the folders using the command line or through PowerShell, those Shellbags will never appear, because those tools bypass the explorer shell, meaning they don’t trigger Shellbag updates.
Figure 15: PowerShell Navigation
As well as this, browsing the file system through a web browser, will prevent Shellbags from being generated; the image below shows how I can navigate to my downloads folder, through a web browser, without ever generating any Shellbag entries.
Figure 16: Browser File System Traversal
Correlation with other artefacts
Shellbags rarely tell the whole story on their own. To build a comprehensive timeline, you will want to correlate what you see here with other Windows artifacts. For example, the $MFT and USN Journal can confirm not just the existence of those folders, but when they were created or deleted.
Forensic artefacts like Prefetch can help you tie the browsing of a folder directly to the execution of files inside it, turning folder access into evidence of program use. If you suspect data left via an SMB share, SRUM artifacts can show you network volume that may strengthen your case for exfiltration. Jump Lists and RecentDocs can add another layer, demonstrating that the user didn’t just look inside a folder but also interacted with its contents.
Conclusion
Shellbags remain one of the DFIR analyst’s favourite artifacts, they’re subtle, persistent and often overlooked by attackers trying to cover their tracks. They can help depict a user’s journey through local drives, external drives and network shares, as well as zip folder access. However, as with any forensic artifact, they are not perfect and should be corroborated with other artifacts to join the dots. Shellbags should be treated as one small piece of a very large puzzle.
Tools Used:
- ShellBag Explorer
- CyberChef
- RegEdit














