What is NVIDIA SMI?

The NVIDIA System Management Interface (nvidia-smi) is a command line utility, based on top of the NVIDIA Management Library (NVML), intended to aid in the management and monitoring of NVIDIA GPU devices.
This utility allows administrators to query GPU device state and with the appropriate privileges, permits administrators to modify GPU device state.

It comes pre-bundled with all NVIDIA drivers and as a result, is probably installed on your machine if you’ve got an NVIDIA graphics card in your device.
What is DLL Hijacking?
Dynamic-link library (DLL) search order hijacking, often shortened to DLL hijacking, is a process of exploiting execution flow of an application via external DLLs. Essentially it is possible to force an application to load a malicious DLL by hijacking the search order used to load legitimate content.
If a vulnerable application is configured to run at a higher privilege level, then the malicious DLL that is loaded will also be executed at a higher level, thus achieving escalation of privilege. Often the application will behave no differently because malicious DLLs may also be configured to load the legitimate DLLs they were meant to replace or where a DLL doesn’t exist.
Finding The Issue
While playing around with SpecterOps’ automated DLL hijacking discovery, I found an NVIDIA DLL what was vulnerable to hijack.
The issue was found by leveraging Sysinternals Process Explorer, to search through running processes for all DLLs loaded and called by running applications. The following steps can be taken:
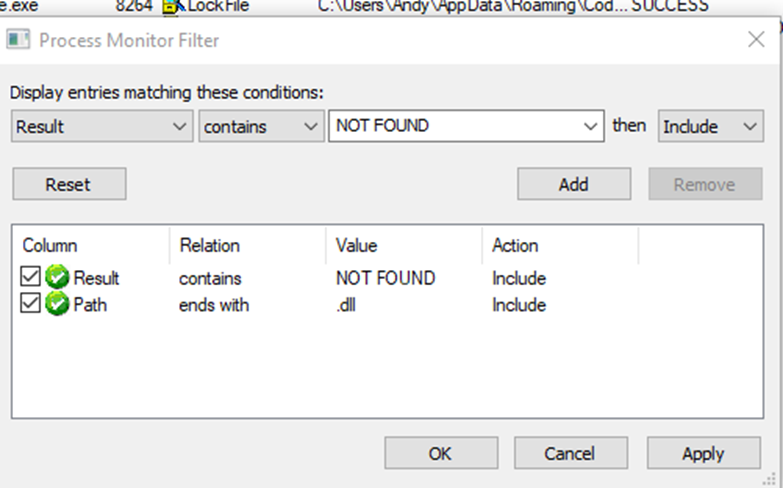
1) Open Process Monitor with the following filters, to identify potentially vulnerable applications and binaries.
- Result contains NOT FOUND
- Path ends with .dll
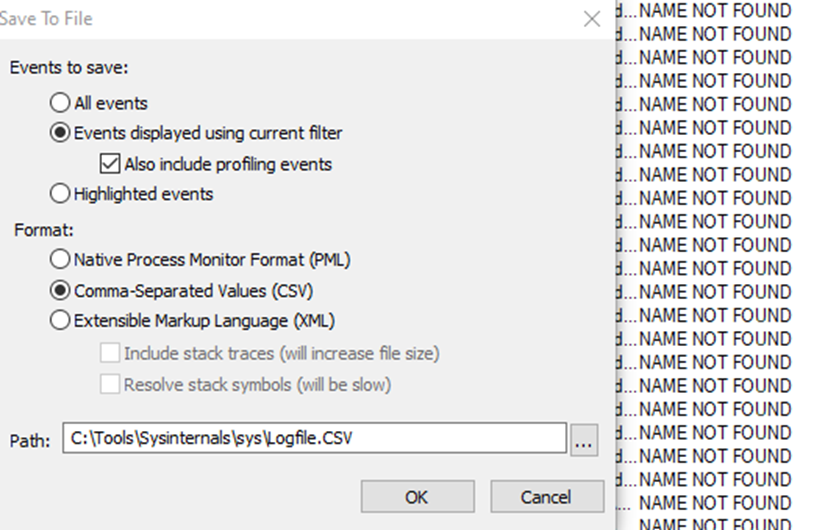
2) Export the running list to a CSV then leverage slyd0g‘s Get-PotentialDLLHijack script that can be found here.
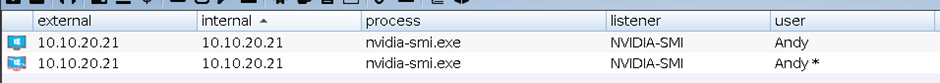
3) Following execution against the CSV it was found that nvidia-smi along with a few other binaries were vulnerable:
Get-PotentialDLLHijack -CSVPath .\ProcessList.CSV -MaliciousDLLPath .\maliciousDLL.dll -ProcessPath "C:\Program Files\NVIDIA Corporation\NVSMI\nvidia-smi.exe"
The process nvidia-smi.exe attempted to read the following DLL:
C:\Program Files\NVIDIA Corporation\NVSMI\MSASN1.dll
However as the DLL does not exist, we as the attacker can replace it with our own malicious one and hijack the path of execution so that the binary calls our DLL instead.
Copy-Item maliciousDLL.dll C:\Program Files\NVIDIA Corporation\NVSMI\MSASN1.dll
Then by stopping the nvidia-smi.exe process, we can then start it with our newly created malicious DLL. The contents of which can be anything, in the case of this proof of concept I have used cobalt strike shellcode to illustrate the execution of attacker-controlled code, this technique can be leveraged for persistence.
Fixing The Issue
NVIDIA have released a patch for the issue that can be found here. Apply this or alternatively uninstall nvidia-smi if not required.
Disclosure Timeline
- 2020-07-01 Discovered and reported finding to NVIDIA PSIRT
- 2020-07-02 NVIDIA confirmed the issue as valid and began investigating
- 2020-08-18 NVIDIA confirmed that the bug would be fixed in their next GPU Security Rollout update to be released on September 30th
- 2020-10-01 Findings published and NVIDIA issued a fix released in the bulletin, CVE-2020-5980














