Yet again another company suffers a ‘hack’ that turns out to be nothing more than a credential stuffing attack. This time Boots have stopped customers using advantage card points to pay for products. This is after 600,000 Tesco accounts were compromised in the same way. No systems at Boots were compromised, the attackers just tried existing username and password combinations against their system in what’s called a credential stuffing attack. After gaining access to accounts the attackers then used the points to buy goods, presumably for onward sale. So how does credential stuffing work and how can I protect myself?
Credential Stuffing – how does that work?
This is a surprisingly easy attack and is commonly used to steal accounts such as Netflix, social media and shopping accounts. Essentially the attackers use automated tools to try multiple username and password combinations from other breaches on the website they want to attack. The developers of the tools are so brazen you can find videos of their tools being used on YouTube. Here is a video of a Netflix tool being demonstrated. Note how quickly valid accounts are obtained.
Once they have valid credentials they will either sell the valid ones or simply use the access themselves.
This is what happened at Boots, Tesco and countless others before. This will happen again unless you protect yourself, and companies do a better job of securing our account information.
So how can I protect myself?
The easiest way to protect yourself is to use different passwords everywhere, but remembering them can be really hard…
This is where password managers come in. These tools will allow you to store passwords securely and will generate random passwords for each site meaning credential stuffing attacks won’t work. There are loads available, you may even have one with your anti-virus package (you do have antivirus don’t you?!)
Examples of a few of the more well-known ones:
- KeePass
- LastPass
- Dashlane
- 1Password
- Roboform
- Keeper
You will need a strong master password for these, Get Safe Online (a brilliant resource, especially for parents worried about kids online activity) has some great advice on how to set one up.
Next set up two factor authentication, sometimes called two step verification, whilst not a silver bullet, this is very effective at stopping most attacks like this. This requires you to enter your password and a code from an app or a text message, meaning if an attacker has your password from a breach and tries a credential stuffing attack they will be unable to login without that code. If there is a choice go for the app as it is more secure, due to an attack called the SIM Swap attack.
There are many different ways to set it up depending on the site, https://twofactorauth.org/ will help you work out how to do it. Try to enable it in as many places as you can, but certainly your email account, your password manager, social media, shopping & finance services are key places to start.
What if I have already been breached?
I wrote an article on how to recover from a breach, this has some useful information, but as a minimum you will need to change your password on the site compromised and anywhere else you have used the same username/password combination. You should then enable two factor authentication if it is available.
What can Boots do better?
Interestingly when registering for a Boots account the minimum password requirements are pretty poor, which may explain why accounts become breached. Just 8 characters of any case are needed and no special characters are required. A simple password of boots123 or password12 would satisfy the requirements. Not good.
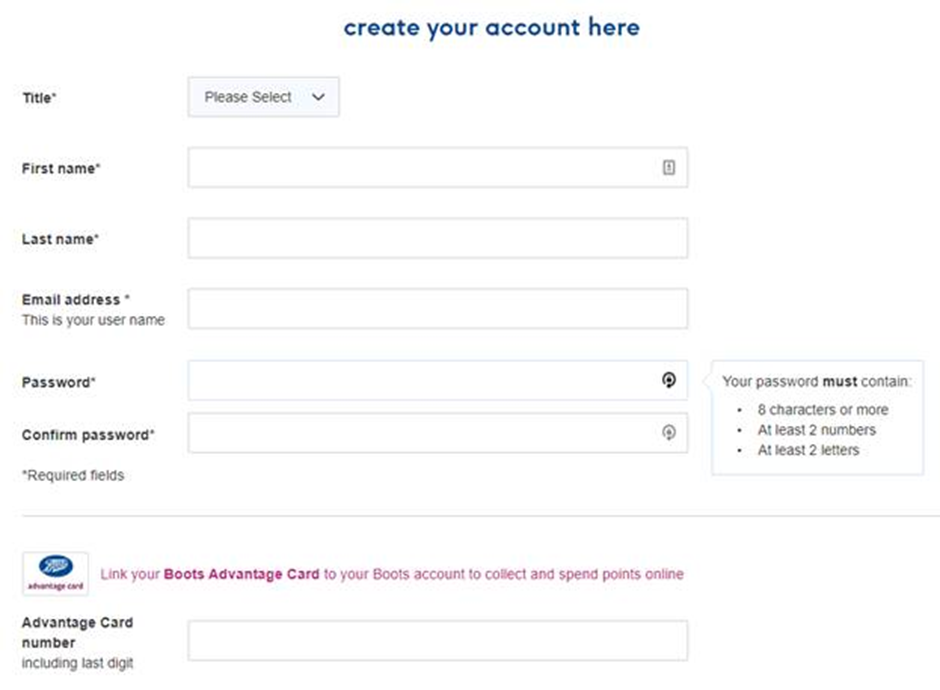
Boots also don’t seem to support two factor authentication, which when you consider the advantage card points have a direct financial value is pretty poor.
Although Tesco were also breached, they do it a bit better and also include a link to some good password advice. This does not mention using a password manager though. Tesco also does not support two factor authentication either.
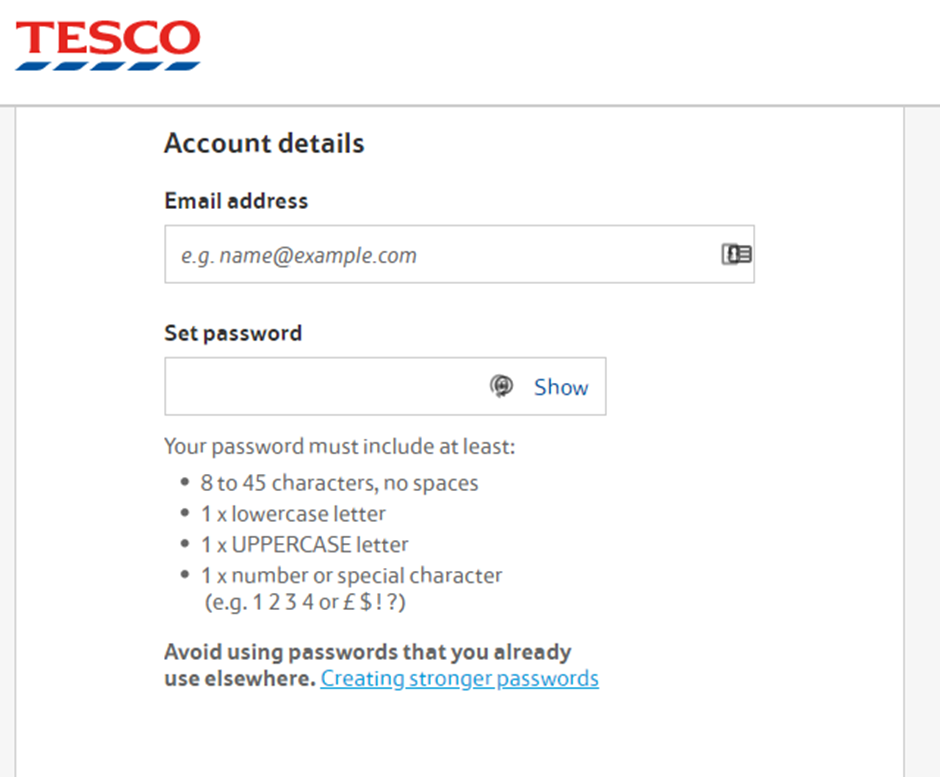
So come on Boots and Tesco (and everyone else), lets force users to use better passwords by firstly requiring better quality passwords, secondly, supporting and encouraging the use of password managers, thirdly, checking services like Troy Hunts Pwned Passwords for already breached passwords and preventing those from being used. This is easy to achieve with the API offered and allows for real time look up the entered password to validate it against known data breached passwords. Many companies have already implemented this as a simple and easy way to disallow poor passwords..
Any finally, implementing and mandating two factor authentication, especially where personal or financial data is held will greatly enhance your security offering.
Simple controls will prevent credential stuffing and help you avoid being the next statistic.














