
One of the flaws with our attack against the iKettle is finding a victim with one to hack. If the kettle is unconfigured, then you might find one through searching the wigle.net database of war drives for the SSID iKettle as detailed in my post here. But that’s fairly lame, as all you can do is boil their kettle.
Whilst reading the manufacturers Twitter feed, it struck me that one can use social networks to find victims with configured iKettles in their houses, ripe to steal their WPA PSKs, compromise their router and DNS, then steal everything they do online.
Here’s how it works
Twitter users tweet about their kettle to @wifikettle – they would, wouldn’t they!
@wifikettle then retweets and/or replies to them, so you only have to search through one Twitter account.
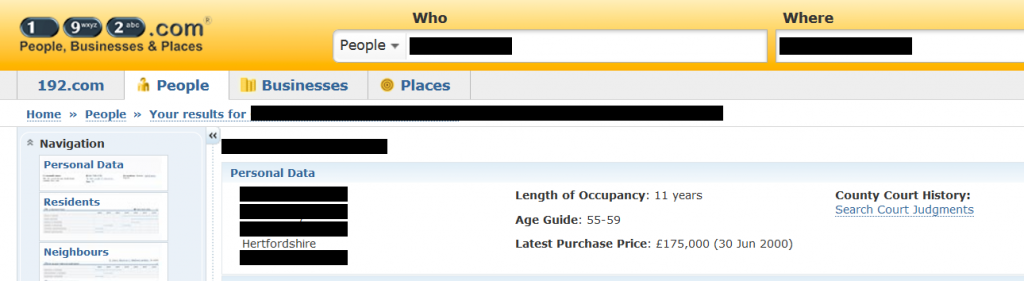
Identify your victim’s account and research using simple open-source intelligence techniques. Simply reading the last few tweets of the user below showed that they lived in a town in Hertfordshire near the M11.
Moments later we had their home address through a search of www.192.com.
The same applies to Facebook:
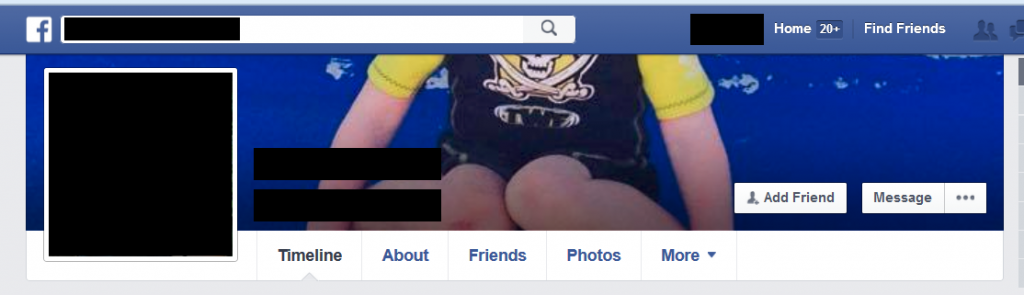
So now we have all we need to find our victim’s house and steal their identity and more.
It would be trivial to map our findings using Google Maps KML, but it seems unfair on the users to publish that.
Breaking the iKettle PIN
You may remember from our Infosecurity Europe demo that the Android-configured kettle is much less secure than the iPhone-configured version. The default kettle telnet PIN is changed from the default of 000000 when setting it up using iOS.
We got round to brute forcing the 6-digit PIN with Hydra last week:
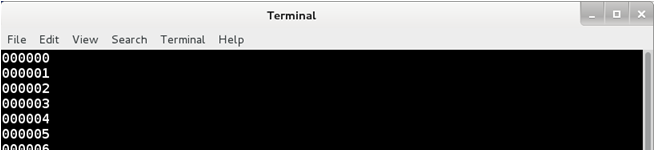
It sustained 34 attempts per second, indicating that a PIN crack should take an average of 4 hours.
Identifying iKettles with default PINs
Another couple of steps with social networks and one can easily identify who set it up with iOS (more secure) and who set it up with Android and is very vulnerable.
- Users seeking tech support often tweet @wifikettle looking for help. Gripes include the mobile O/S they’re using.
- They’re particularly active on Facebook. Read through the posts to the iKettle FB page, lots of useful target information there too, several identifying that they’re Android users.
Conclusion
If you use a Wi-Fi kettle, keep an eye out for updated software, but in the meantime change your PIN. We’ve written a how-to here.














