
Right, you, with that rooted Android device. Stop now, put it down and step away from it. I’ve told you before not to root your personal devices, so don’t do it.
Don’t believe me? Right. I’ll have to demonstrate then. Don’t blame me if I deliberately accidentally upload all your nudie selfies to the Internets.
What’s that? You’ve put on a lock and disabled ADB. Well done, you’ve earned some brownie points for trying. It’s just a pity that, as you’re using a Rockchip device that won’t do anything to help you. Here’s a brand spanking new way that I can steal all that lovely data from you.
You see, when you plug your tablet in to charge when it is powered off the Rockchip firmware boots itself into a special charging mode of Android. The important thing here is that it uses the same system partition for this mode as for normal Android usage, and for some totally unknown reason it enables ADB.
Some of you may already be seeing where I’m going with this: if you’ve rooted your Rockchip based device, even if you have ADB switched off, or ADB authorisation enabled, then I can still get your data, by turning the tablet off, plugging it into a laptop and running ADB.
Let’s try this out. Just for a difference I’m not going to pick on the Hudl, instead I’m going to go with the winner for the most migraine inducing screen in a 7” tablet: the Medion Lifetab E7318, usually found gracing your Aldi stores on the odd occasion.
So first off, I rooted it by the usual method of adding a setuid “su” to the system partition and writing it back to the device. Then I set it up with a passcode and connected it to a fake AP. At no point did I enable the developer options, meaning that ADB is disabled in the normal boot to Android.
Look, no Developer Options Here!
It’s Locked!:
Just to prove that ADB is disabled, I attempted to use it whilst the tablet was booted, look ADB not Enabled:
![]()
The next step is to power down the tablet and just connect it to my laptop port. It goes through a quick boot sequence and then shows the charging battery. A few seconds later I hear the “beep” from my laptop that indicates that it sees a new USB device.
No surprise, there’s an ADB interface with a fake identification string. Then we get a shell and run our previously set up su executable – PWNED!:

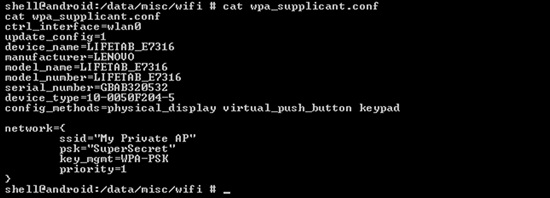
So there we are, because you rooted your Rockchip based tablet I can now access all your data if I can get hold of the physical device. To demonstrate this, here’s the wifi key:
And how about the PIN hash? Here it is:
![]()
So. How can I protect myself? Well, there is a serious design flaw in Rockchip’s chipset, which should be easy for them to fix; but, you can mitigate this quite easily, by not rooting your tablet and/or encrypting your data partition (if the build of Android supports this – unfortunately neither the Tesco Hudl nor the Medion Lifetab do).
It’s not all doom and gloom though. If you haven’t rooted your device, the mini-build of Android is quite ineffective. It only runs adbd as the shell user, and doesn’t spawn the rest of the Android eco-system so you can’t call the Android services.
This leaves very little space for information leakage as the Android permissions are normally quite good.













