Following last month’s post about what OpSec is and how it can benefit your company I wanted go a step further, and look at some of the ways you can super charge your searches to find interesting data about your company.
Basic search parameters
As I mentioned last month, one of the most useful tools you have is a plain old search engine. There are many, but in my experience, Google does seem to have the largest index and the widest documented search operators available.
The key operators that I find most useful are:
| “search term” | Using quotes says “find me things that match this” |
| OR (or |) | Provide matches to either term |
| AND (or &) | Provide matches to both items |
| -word | Do not include results that contain this word |
| site: | Show results from this site only |
| filetype: | Include results that have a particular file type (e.g. pdf) |
| intext: | Search only in the web page body |
| before:YYYY-MM-DD | Only provide matches before the date specified |
| after:YYYY-MM-DD | Only provide matches after the date specified |
These can all be combined to make really powerful searches.
The site parameter
It’s important to filter your results to your target and one of the quickest ways to search websites is to use Google. site:microsoft.com will show only results from Microsoft.com
You can easily find subdomains with site:domain -www
An example using site:Microsoft.com -www reveals some other domains and some content on them. Whilst searching a domain as large as Microsoft with this technique is unlikely to be of value given there are over 76 million results, smaller domains can yield much better results.
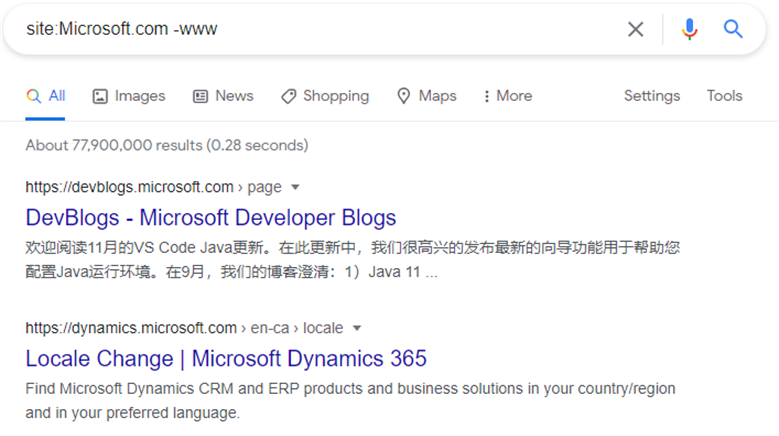
One thing to note is you can take this levels lower, so if you wanted to find all pages on the subdomain code.microsoft.com just search: site:code.microsoft.com. You can also search subdomains and specific sub pages on that domain for example site:code.microsoft.com/updates.
Then super charge this with a keyword site:code.microsoft.com/updates “2020” will provide all posts about code updates mentioning they keyword “2020”, a much more manageable 26 results.
Again combining operators can reveal sensitive documents site:microsoft.com filetype:pdf
So again, using Microsoft as an example reveals:
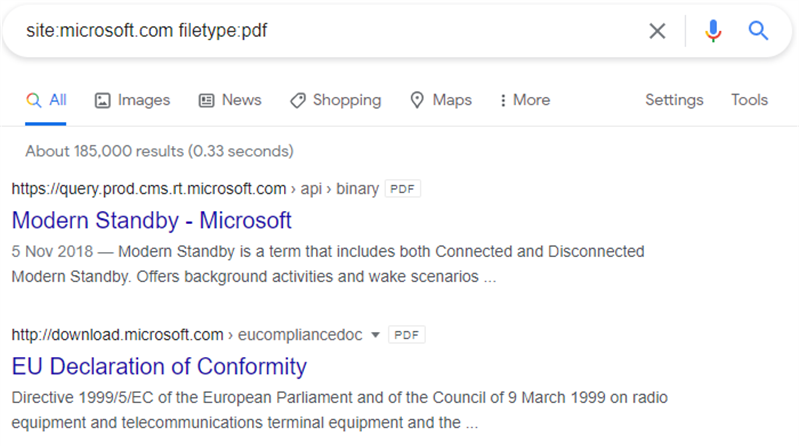
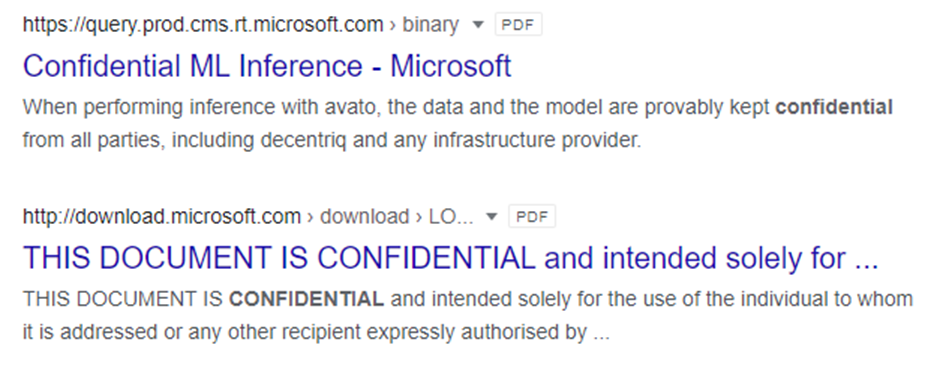
I’ve used this in the past to find confidentially and internal use only marked documents by appending specific terms in quotes. E.g. site:microsoft.com filetype:pdf “confidential”
Using AND/OR to discover in use technologies
When researching victims attackers need to know what technology you use. If an attacker can deduce what technologies your company uses they can tailor attacks to target that technology or your users of that technology.
Using “companyname” AND site:slideshare.net will show you slideshare.net sites where the search team is found. Google will show you broadly similar results without the AND, but AND works well to clarify your desired results. In addition to AND, OR is very powerful to allow you to search multiple technologies at once. In place of OR you can also use the | symbol.
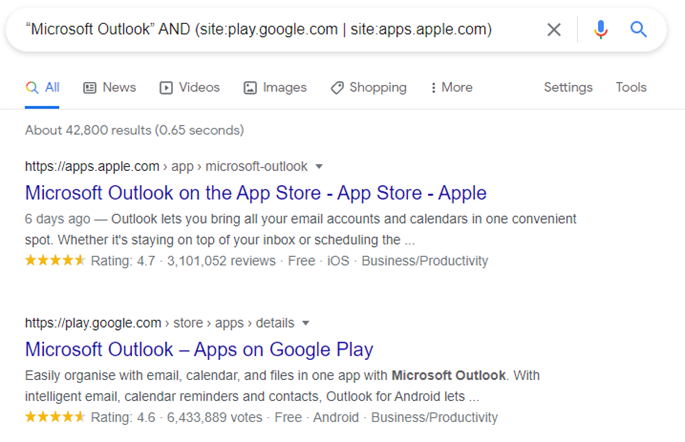
Using “searchterm” AND (site:play.google.com | site:apps.apple.com) will show you results for your search term on both Apple and Google’s mobile app stores.
An example “Microsoft Outlook” AND (site:play.google.com | site:apps.apple.com) will show all entries on the two mobile app stores for Microsoft Outlook. This would include all worldwide store flavours.
I’ve used this in the past to find public Trello boards that reveal internal systems, GitHub can reveal either API end points if using the domain as a search term or company profiles if using the company name.
Emoji searching
A little known fact is that you can even search using emoji on Google. Why is this relevant you ask? How often do you see this?
Contact Us
Pen Test Partners LLP
☎ 0203 095 0500
So how do you search for the phone number? You could try some complex regex, but then realise Google doesn’t really support that, you could type “tel’ (which is often worth trying along with “mobile” and “cell” regardless), but you often you will get false positives. The emoji works well so how do you search for that?
Use https://www.alt-codes.net/ to help find specific emoji you want to search on. Just click them and copy/paste in the Google Search.
So your search term could look like this
“search term” (☎|☏|✆|📞|📱|℡)
Another way is to use LinkedIn with a site specific search.
site:linkedin.com/in “search term” (☎|☏|✆|📞|📱|℡)
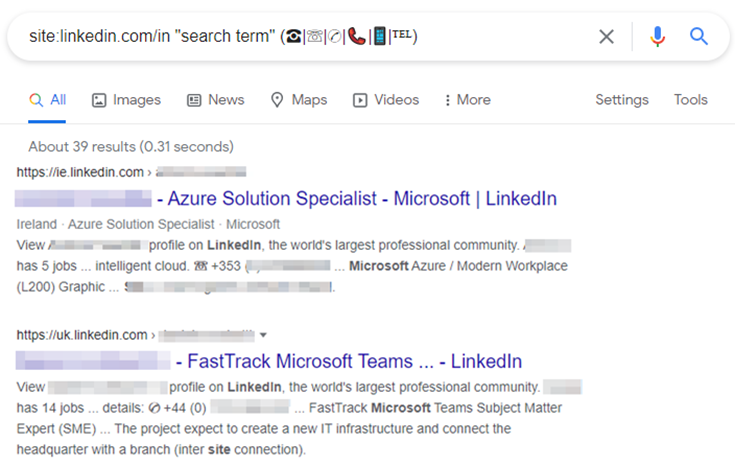
The above revealing Microsoft staff who use emoji to share contact information.
Interestingly, this can often reveal potentially suspicious pages hosted on other sites. In this case Microsoft.com user forum pages:
site:Microsoft.com intext:(☎|☏|✆|📞|📱|℡)
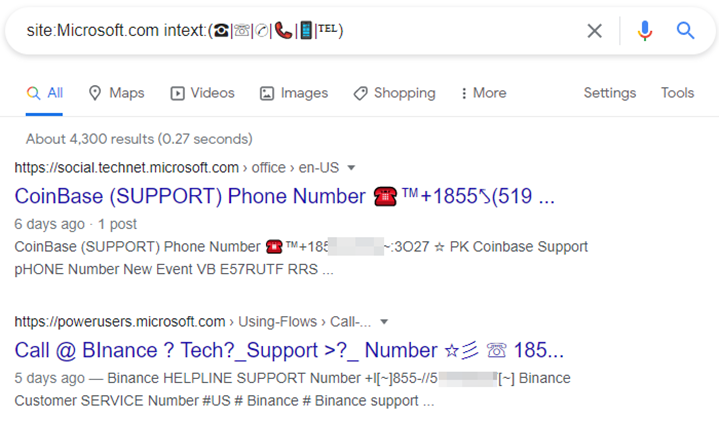
It should be noted that Binance do not have a support number advertised on their website and Coinbase EXPLICITLY say on their website they do not offer live phone based support:
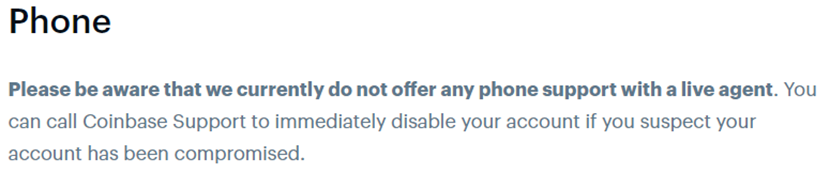
Therefore, you can assume these are services acting as potential vishing services with a view to attackers hoping searches for provider support numbers will call up and divulge details. The numbers on the pages use non-standard character sets and capital O in place of 0, including using internationalised character sets to try to confuse automated systems using regex.
Note: I’ve obscured some details to avoid driving calls to the numbers.
Whilst this may not be directly relevant to your OpSec (depending on the site and search terms), it can be interesting and shows how attackers attempt to abuse trusted sources to appear more legitimate.
In summary
Good Google search operators are crucial to helping you find key items of information that you may be leaking. They can not only reveal subdomains, but content on them can be rapidly searched with choice operators.
I have only scratched the surface with the above, there are many other resources showing how you can find things such as unprotected logon fields, vulnerable services, email addresses, data leaks and many many more items of concern. Building complex Google Dorks will really help illuminate those areas allowing you to close them off before they are abused.
A thorough assessment of your OpSec will help you to understand what services you are presenting to the internet, but more importantly what you are leaking.
Read more about OpSec in Red Teaming here.
If you’d like any help, do reach out, I’d happily give you some pointers: @_tonygee_.














