Grandstream are a provider of IP video and voice services, as well as Wi-Fi and other related services and equipment. Their products are sold in over 150 countries and they have offices around the globe.
We were having a look at their GWN.Cloud management platform, used for remote device and wireless network management.
It connects around 5 million devices in total. That’s a LOT of devices in businesses all around the world.
Hosted in AWS it uses “Bank-grade TLS encryption from end-to-end”, so it MUST be secure, right?
Stealing a few million Wi-Fi PSKs
https://www.gwn.cloud/login is a free service with straightforward username/password authentication. No MFA, but hey.
After creating our own accounts for our own equipment, I noticed an issue with one of the API requests:
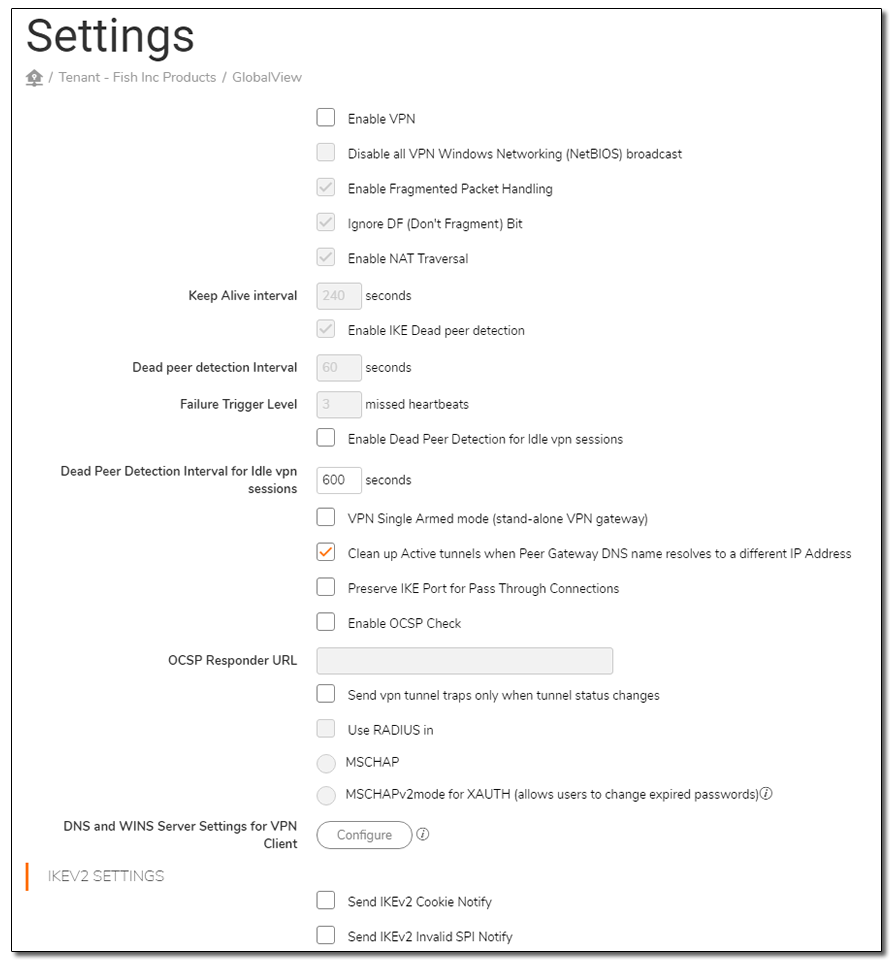
The endpoint that would edit a user had an IDOR when giving access to a network.
It did not check that the user authorising the other user was authorised to do so.
POST /app/user/save HTTP/1.1
Host: www.gwn.cloud
Connection: close
Content-Length: 72
Accept: application/json, text/plain, */*
Origin: https://www.gwn.cloud
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/74.0.3729.157 Safari/537.36
Content-Type: application/json;charset=UTF-8
Referer: https://www.gwn.cloud/account/users
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: SESSION=7672dd7d-58a7-47f2-8bbc-3534108e4987
{"email":"[email protected]",
"roleId":2,"
networkIds":[
16089
],
Highlighted is the networkIds JSON parameter which is an incremental ID that can be enumerated. Adding ANY number would give you access to the network where you could:
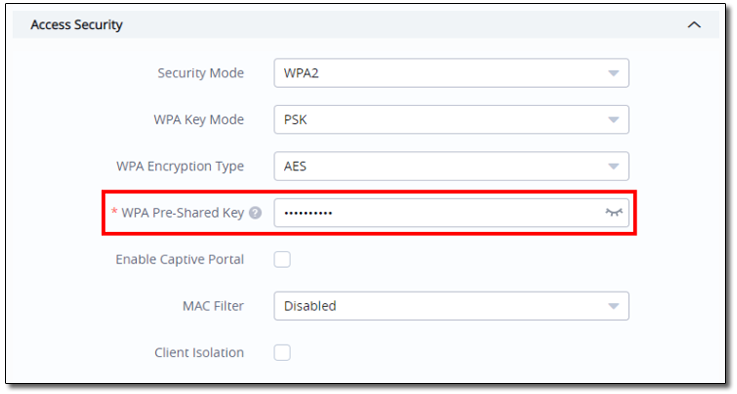
- View and change Wi-Fi password
- Turn all devices off
- Get access points info
- Get WIFI clients information (computer or phone name)
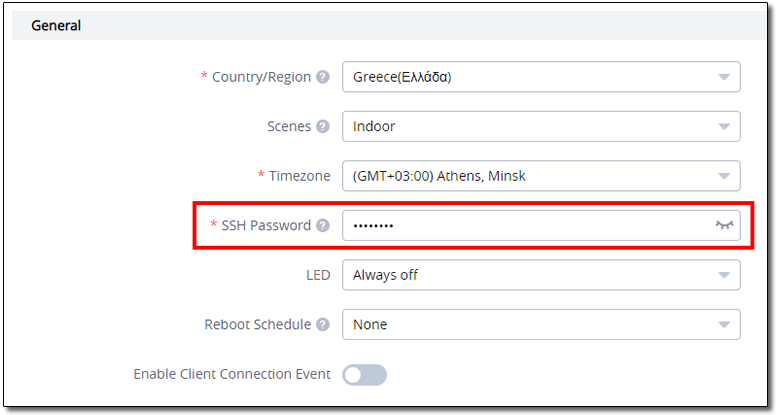
- Get SSH password of the devices
- Get System log
- Enable URL access log (all the URLs clients have visited).
As the network id numbers are sequential we estimated that ~10k users were vulnerable.
It’s also scary that you could retrieve SSH and WPA password in cleartext. They are easily revealed here:
Disclosure
We reported the issue to Grandstream support, in the absence of a vulnerability reporting contact. In fairness, they were really good at receiving it and responding.
A shame about the trivial IDOR in their cloud service, but great that they responded so promptly.
We have no idea if the service had been compromised using this vulnerability previously.
7th August 2020: Reported bug via their helpdesk
7th August 2020: The bug was confirmed to exist
17th August 2020: I was notified that a patch was issued and confirmed that the issue was resolved
Conclusion
Insecure Direct Object References are hugely common in APIs. We still aren’t sure why IDOR/BOLA isn’t number 1 in the OWASP Top Ten, but it’s critical to authorise ALL requests properly.
Common areas that request authorisation is overlooked include:
- Authorising a change to the email address to which password reset emails are sent
- Authorising adding of a user to a group
- Authorising modification of a user’s permissions
Any one of the above totally compromise user accounts and/or the wider system
If you don’t check that the requestor is the correct user, then your authorisation is shot to pieces: any authenticated user can make the request














