As well as running the Hacking You Fat: The FitBit Aria workshop at DefCon 23’s IoT Village this year (more on that later) we also thought we’d take on their big fridge challenge:
“Can you own our #IoT #Samsung – RF28HMELBSR fridge ::] @_defcon_”.
As a team we’re doing more and more IoT research and hacking so this was a great opportunity to work on something we can’t get our hands on in the UK yet.
It was a full-on team effort over the course of a day, so I’ve gathered everyone’s notes here.

What’s the fridge?
In the summer of last year Samsung brought out their RF28HMELBSR smart fridge, the successor to the RF4289HARS from two year previous.
The fridge is part of Samsung’s line-up of Smart Home appliances which can be controlled via their Smart Home app.
Man in the middle attack
Whilst the fridge implements SSL, it FAILS to validate SSL certificates, thereby enabling man-in-the-middle attacks against most connections. This includes those made to Google’s servers to download Gmail calendar information for the on-screen display.
So, MITM the victim’s fridge from next door, or on the road outside and you can potentially steal their Google credentials.
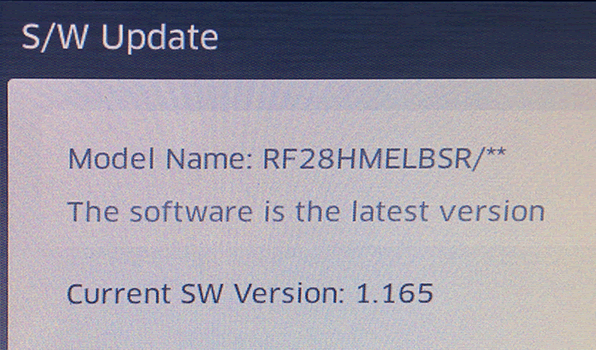
The notable exception to the rule above is when the terminal connects to the update server – we were able to isolate the URL https://www.samsungotn.net which is the same used by TVs, etc. We generated a set of certificates with the exact same contents as those on the real website (fake server cert + fake CA signing cert) in the hope that the validation was weak but it failed.
The terminal must have a copy of the CA and is making sure that the server’s cert is signed against that one. We can’t hack this without access to the file system where we could replace the CA it is validating against. Long story short we couldn’t intercept communications between the fridge terminal and the update server.
Google Calendar service
The fridge runs Google calendar, so you can set events and generally boss your family around from the fridge screen!
It’s a usable feature and one that hasn’t gone without its own share of API update bugs
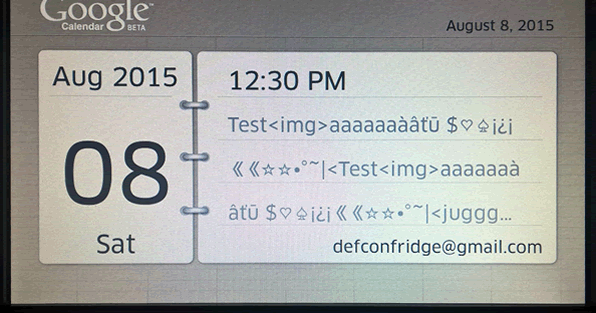
This should have been an excellent route to get content on to the fridge; attaching tags and more to calendar entries. However, as HTML and other mark-up is not interpreted we couldn’t get a foot hold there either.
Firmware attack
We also looked at the possibility of faking a firmware update to compromise the unit via malicious custom update. We found the URL scheme to download the file, but we still need to find out a number of parameters to complete the URL. These are not secret things, just difficult to guess, like a code name for the model of the device, likely a serial number, etc.
TCP services and certificate challenges
The fridge’s terminal has at least 2 listening services. One on port 4444 (SSL) and one on port 8888.
The service on port 4444 requires a client side certificate for most requests, though not all are validated against the client side cert. We suspect this is used by the mobile app and therefore the cert must be located in the mobile app code.
The mobile app
We pulled apart the mobile app and found what we believe is the certificate inside a keystore. We “believe” we did because it is has a name that suggests this. However, it is correctly passworded and we are yet to extract the password that opens the key store. We think we’ve found the password to the certificate in the client side code, but it’s obfuscated and we haven’t got round to reversing it, yet.
Conclusion
…and that’s how far we got.
We wanted to pull the terminal unit out of the fridge to get physical access to things like a USB port and serial or JTAG interfaces, but ran out time.
However, we still found some interesting bugs that definitely merit further investigation. The MITM alone is enough to expose a user’s Gmail creds.
The fridge STILL isn’t shipping in the UK, nor can we find any other Samsung smart fridges on the market here.














