Personally I’m terrible at finding my way around in the car. Six years ago I used to scribble instructions down having read them from a map book or the Internet and still fail to follow them fully or miss a step. So, after one annoying day trying to navigate my way around Leeds’s inner ring road, where I ended up parking a mile from site because, although I could see where I wanted to go, I couldn’t work out how to get there; I bit the bullet and bought one of them new fangled Sat Nav devices.
Because I’m a sad geek I bought an expensive one that had Bluetooth and could connect to my phone and read out my text messages and even, according to the adverts, act as a hands free unit. The last one was an embellishment, unless you count shouting at your windscreen at the top of your voice whilst trying to steer your vehicle down the A43 and not crash it.
Anyway, move on a bit and the original Sat Nav was getting creaky; it’s amazing how much the road system can change in 5 years and it’s also amazing at how much I’d have to expand my mortgage by to update the maps on the device. So, the missus bought me a brand new one of a different type, just to annoy me as the interface was different.
Finally, just now I’ve bought a car with a built in satellite navigation facility. Whilst I was messing around with my new (second-hand) car, I noticed that the sat nav installed had the previous owner’s history on it. This got me thinking; just what do we leak.
So, here’s a quick investigation into what you can scrape for them.
The Oldest One: TomTom GO 530
This was deliberately meant to be a fancy sat nav, with Bluetooth and mobile phone (pre-smartphone) connectivity and a radio transmitter (to play mp3 files). The TomTom system is based on a very cut down version of Linux.
I had configured this for a bit of security, so it was configured with:
- My home address configured as home location
- A PIN code which was required to use the device
- Three favourite locations
- Only one app was installed (a terminal) which didn’t work after the last firmware update
So, for the first time in about two years, I put some power into the device and attached it to my laptop with a standard mini-USB cable.
The immediate problem that I noticed was that the device works in two modes: docked and undocked. It appears to require a full power down to switch to docked mode. Fortunately there’s a reset button which perfectly fits my SIM removal tool (seriously, get one of those; they’re really useful, or the end of a paperclip)!
So, in undocked mode the first thing it does is ask me for a password. In docked mode the first thing it does is…. nothing. I just get the internal file system:

Security fail at start: I can just read the files and ignore the lock (Apparently the latest firmware update for this version of TomTom does require a passcode before allowing access via USB). What can we find from here?
Contacts looks interesting:
Opening up the files gives me exactly what you’d expect to find in them. Of particular interest is contacts which reveals a load of phones numbers from the deep dark ages of 2008, for people I probably have no contact with any more!
Then we get onto the interesting files in the root directory. CurrentLocation.dat which contains the longitude and latitude of the last location when the device could see satellites, a quick mangle around and posting into Google maps showed it to be the house I used to live in. Strangely I’m not going to screen shot that; so I’ve faked this:
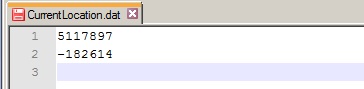
We can divide the co-ordinates by 100, to get 51.17897,-1.82614 and put this into Google maps to get the location:
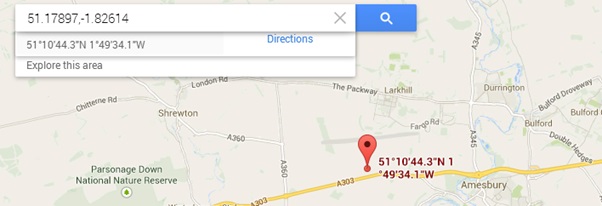
Stalking commenced!
The ttgo.bif file contains all the local settings, including the home location, interestingly enough this actually includes the street name and makes a guess at the number and it is pretty accurate:
![]()
The most interesting file is in the current map directory, in my case United_Kingdom_and_Republic_of_Ireland. Here we find a file called MapSettings.cfg, which holds the longitude, latitude and a text representation of our favourites and history. For example if we look at the below entry in a hex editor:
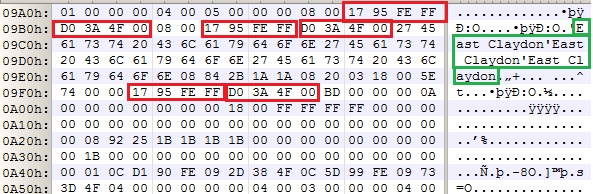
The format for the cfg file is unknown; but some basic analysis allows us to work out some of the information by site, those highlighted in red and GPS co-ordinates, multiplied by 100 to make them an integer and stored as a 32 bit signed integer. The ones above turn in to: 51.92400, -0.92905. We can then put this into Google maps and it comes out as the centre of the Buckinghamshire village of East Claydon, not too far away from our office:
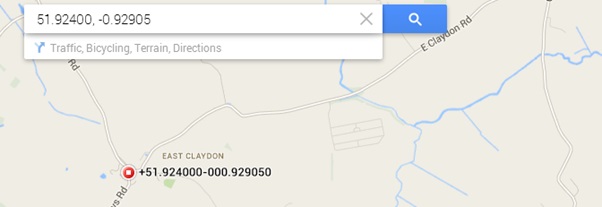
The green highlighted text confirms this. In other entries the other GPS references vary to a range. This could allow us to potentially reverse engineer the file format and track where someone has been.
Unfortunately I don’t have time to do that. Fortunately somebody else has partially done this, or at least allows the extraction of name and GPS co-ordinates and has put this in a program: PoiEdit.
We can simply load the file into PoiEdit and it will dump all 64 of the locations I had in my favourites/I had navigated to:
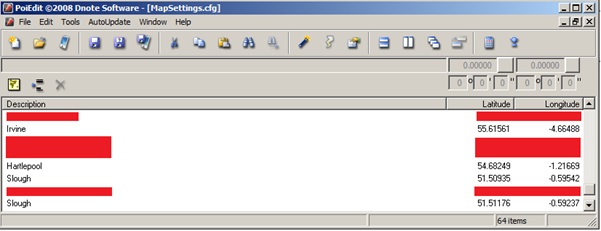
(Slough twice? I must really love that place).
Garmin Nuvi
This was a present from the missus as she’d been stuck in the car with me far too much with me swearing because my previous sat nav was guiding me down a road that no longer existed.
Unlike the previous one I hadn’t put in my home address, or a PIN code. I had just let it stand with default settings (including the not very good default dashboard).
It was about 6 months later when messing around I discovered that you could set an option to show where you’d already been, and lo and behold it showed a dotted line on roads I’d already driven on. It should be fair to note that you can disable this facility and wipe user data.
So let’s have a look at what it does. My first difficulty was to get it to connect to my laptop; for some reason only the mini USB cable that came with it would work. After a few false alarms with trying to get the official drivers and software working (control via web browser you say, that makes me uncomfortable). I found the hidden developer screen: if you go to the volume screen and hold down the right corner for about 10 seconds then you get a hidden menu.
This menu allowed me to change the USB connection type and finally I could read the contents of the device.
Because the device was simpler than my previous one, or I hadn’t used it in the same way; there was less that was interesting in it. The only thing I could find was the location store in the GPX directory.
Here we have a selection of GPX (GPS XML) files which are current and a directory called archive which had older logs:
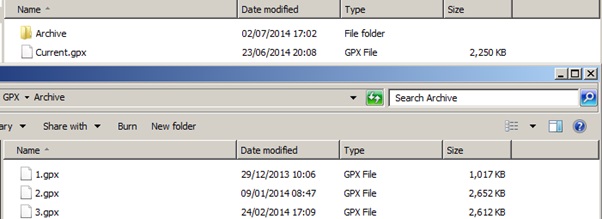
Because of the size they look as if they could hold the exact routes that I had travelled over the period that I used the sat nav.
There aren’t many offline GPX readers (there are a load of online ones, but I’m not uploading these files to an unknown webserver), but Google Earth is a good displayer. Unfortunately it only allows routes made in a format called KML. Time for a convertor: GPSBabel.
Once converted I could load the whole load of files into Google Earth and we can see a track for my travelling (when the sat nav’s been switched on) for most of a year. Note the data included time information, potentially revealing my car’s speed at the time:
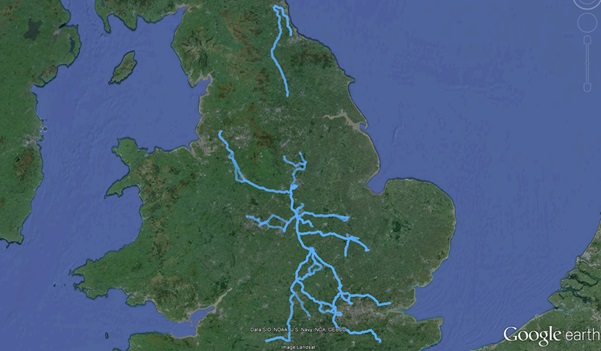
(I certainly get around don’t I!)
Ford Navigation
The hardware for this is built into the card, but for updates it uses an SD card plugged in above the navigation screen. Examining this card reveals nothing. Further digging around shows that people much cleverer than me have looked into this already and there’s not really much I can do without taking my car apart.
That’s not happening.
Tips
What can we do to minimise impact if the device is stolen:
- Examine what your sat nav tells about you; at the least it can reveal which destinations you’ve visited, at the worst it can show where you were, at what time and what speed you were doing.
- Get to know the security options for the version of sat nav you’re using and use them.
- Occasionally wipe the sat nav of all collected data.
- Think about travelling without the sat nav being active, or only activate it near the end of your journey.
- Wipe your sat nav before you give it away or dispose of it.













