So what’s latest with the Bitfi unhackable/hackable crpto currency wallet?
Bitfi release software version 89 over the weekend. Devices updated, so we had a look to see what had changed.
First, they’ve tried to stop the passphrase and seed from being cached in memory and therefore trivially recoverable. They’ve done this using SecureString, which isn’t likely to properly resolve the problem.
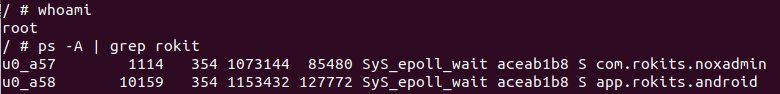
As previously, the two Bitfi/Rokits apps are running. No surprises from a process listing there
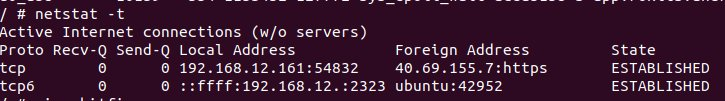
And a look at netstat shows it connecting to an interesting host
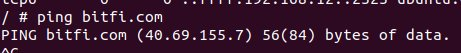
It’s Bitfi of course!
Hang on a minute: the device is working correctly, syncing with the dashboard and yet we are still able to man-in-the-middle the network traffic. That’s asking for BIG trouble Bitfi.
Quickly add our own certificate authority to the device, and we can now intercept all the SSL communications between the wallet and servers.
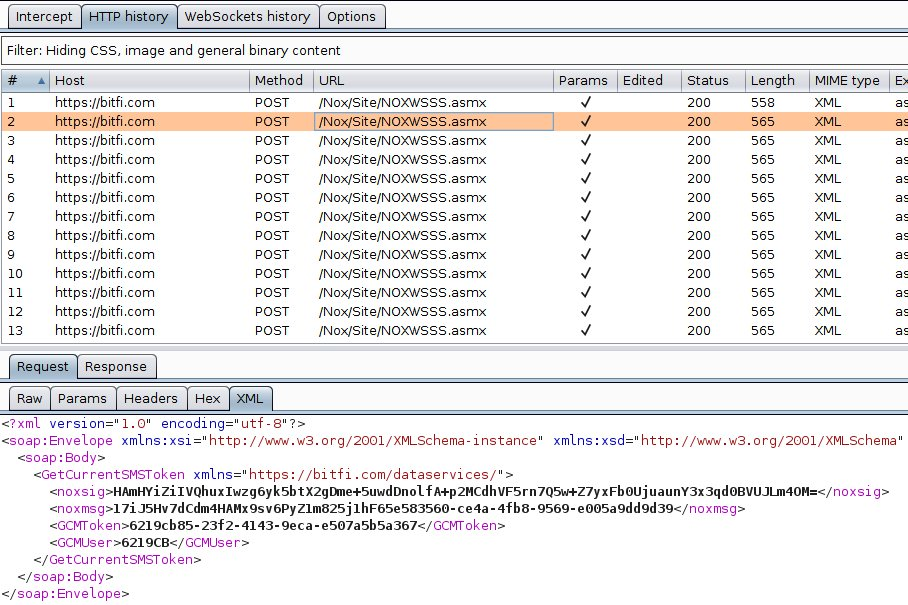
Surely it shouldn’t be possible to intercept data and tamper with transactions. Surely not?
Oh dear
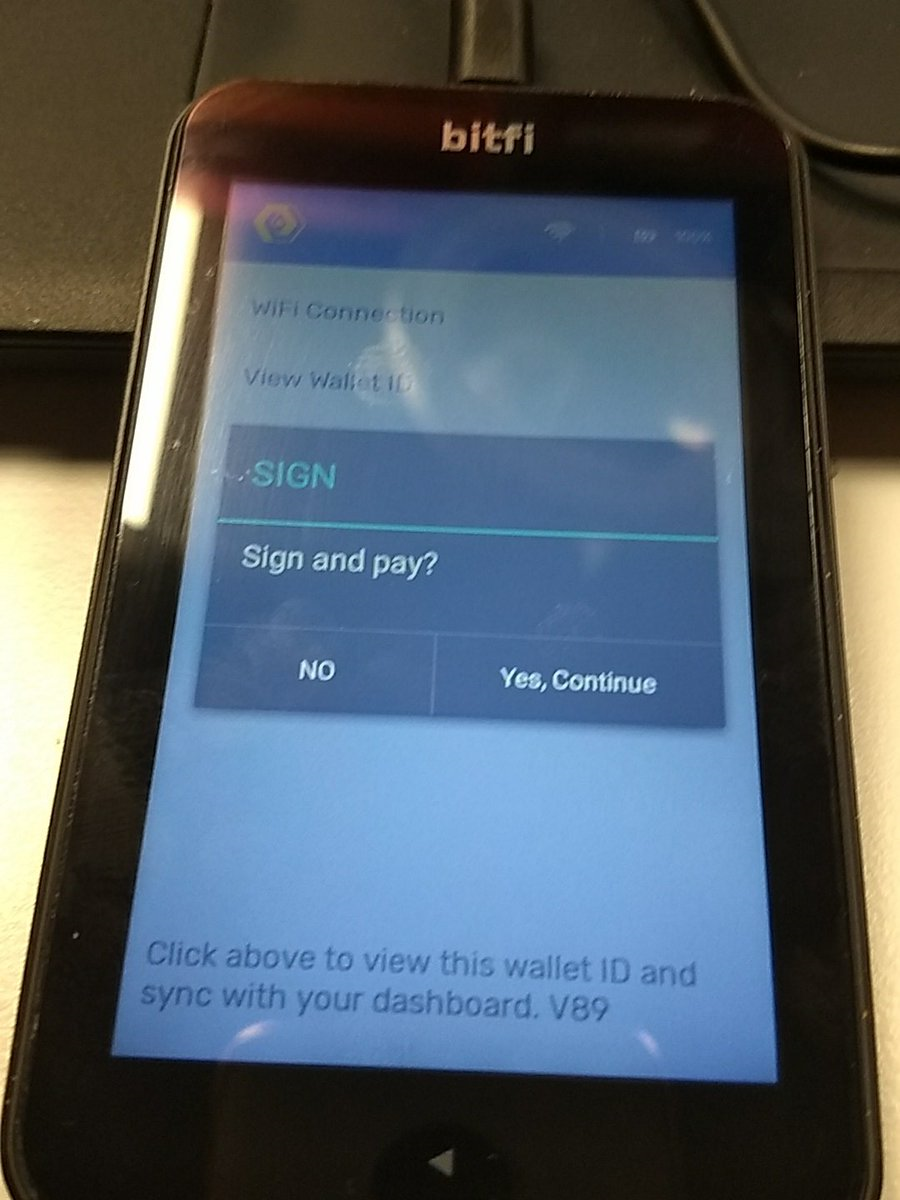
Anyone want to steal some ETH by MITM with a Bitfi?

Conclusion: Bitfi is supposed to offer extra security over and above a regular mobile app and your desktop/mobile device.
Some conventional mobile apps make it far harder to intercept traffic than this.














