Following our live hacking demos at Infosecurity Europe, here’s more detail of the car hack.
We aren’t going with full disclosure for another week or so, to ensure that all owners have had a chance to disable the Wi-Fi on their cars. However, here’s everything we showed at the Show and more:
After Man-in-the-middling the app-to-car connection, we started sniffing traffic. The connection isn’t that stable – it will only support one command being sent every 15-20 seconds or so. If one tries sending more traffic (e.g. fuzzing, like we tried straight away!) then the connection becomes quite unstable.
Looking at the traffic, it became clearer why this was. For some odd reason, the car sends its entire status to the app; the app sends it back again, with any changes. Viewing the hexdump of a single conversation extended to 6 pages of data. For every request (e.g. lights on). Seriously!
This is it sending the alphabet to the car. We aren’t certain why this is part of the message although it looks like it is just cycling through the variables it’s downloading:
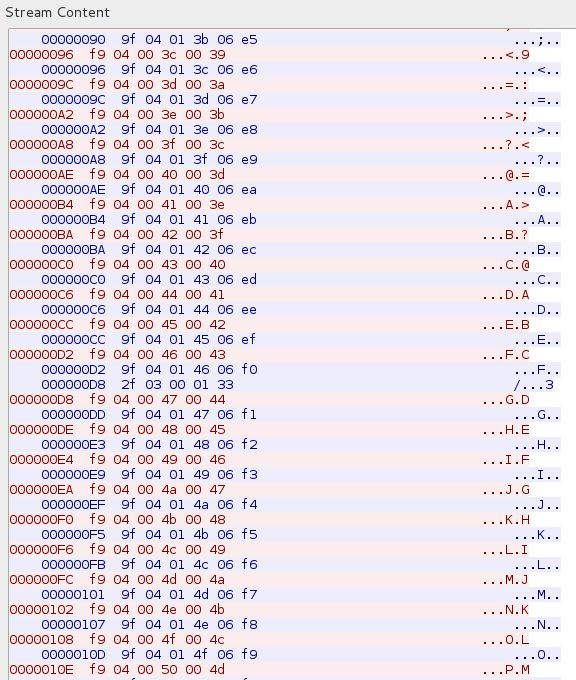
Packet syntax
Strange traffic aside we were able to use captured packet data to work out the syntax, as follows:
{
u8 type;
u8 length;
u8 unknown=0;
u8 cmd;
u8 params[];
u8 crc;
}
Populate a packet as follows:
type=0x6f (a message from the app to the car) length = 0x10 cmd = 0xc0 (192 or -64) params = 30 30 31 44 30 31 38 30 30 30 00 01 00 (001D018000) crc = (6f + 10 + 00 + c0 + 30 + 30 + 31 + 44 + 30 + 31 + 38 + 30 + 30 + 30 + 00 + 01 + 00) / 256 = 0x3e
Obviously the parameters will vary in length according to the length of the packet.
Want some lights?
To turn the lights on, send it this:
f6 04 00 0a 02
More commands will be disclosed next week














