After speaking about Wi-Fi security at a rail industry conference last week, it struck me that very insecure passenger networks are making their way on to trains.
So, here’s a quick check list for making sure your pax Wi-Fi network is secure. Similar checks could be applied to your guest network in your office, Wi-Fi on planes and even buses and cars.
Is passenger Wi-Fi security really that bad today? Here are two examples from recent exercises; draw your own conclusions!
Accessing the staff and train control network from the passenger Wi-Fi network
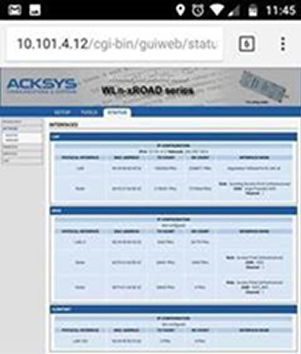
There was no segregation between the pax, staff and train control networks. The admin creds were default too, so one of your passengers could potentially interfere with wireless ticketing devices & potentially the train systems too.
Accessing customer credit card data from the passenger Wi-Fi network
For reference, this is the type of thing we mean when talking about card data:
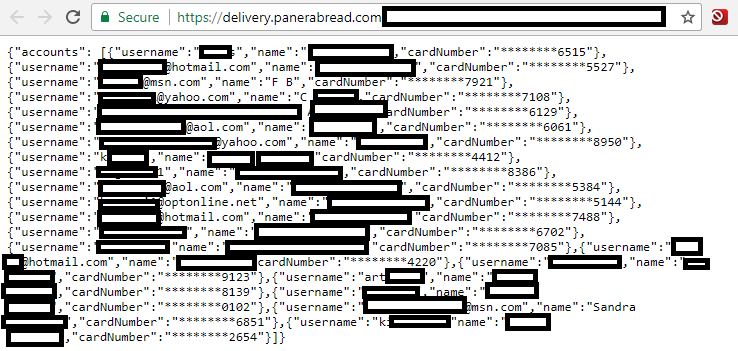
This example is from Brian Krebs post on the Panera breach.
First class passengers got free Wi-Fi, standard class access was paid-for. Whilst standard class customers could stand in the vestibules to cheekily get free first class access, most would pay with a credit card.
Again, segregation of networks wasn’t present. We could bridge the wireless network to the wired network, then found a database server with default creds on the connector. Moments later we had customer card data.
Fixing this. Here’s a checklist:
#1 Segregate passenger Wi-Fi
The most basic defence: ensure that your passengers can ONLY route traffic from their devices to the internet. They should NOT be able to access your staff/ticketing/train networks.
The wireless router admin interface should not be accessible to passengers either: an access control list should be in place to prevent this. Check that you can’t access the admin interface; it’s often available on the gateway IP address.
It’s more expensive, but consider completely isolated, physically separate hardware for passenger Wi-Fi. That’s how many businesses do Wi-Fi in their offices: a separate router and separate internet feed.
#2 Strong admin credentials on your Wi-Fi routers
The router admin interfaces should have very strong credentials in place. In many cases, we find that they haven’t been changed from the default or are far too simple.
Weak or default credentials means that the hacker can change the routing, potentially allowing them access to more sensitive networks on your train.
#3 How often do you update the software on the wireless routers
Security flaws are found all too often in networking hardware. These flaws can allow the hacker to bypass authentication and routing.
So, how often do you check for software/firmware updates for your wireless infrastructure and how often do you apply the patches to fix security flaws?
#4 Are your routers physically secure?
A motivated hacker will be prepared to open cabinets on the train. If your locks just use standard square keys, then that’s no protection at all.
Are your wireless routers behind easily accessed cabinets in the vestibules, or are they located in much more secure cabinets?
It takes moments to open a door and connect to one of the ethernet ports on your wireless router, after which access to more sensitive networks may be possible.
#5 Check that your satellite terminals for your passenger Wi-Fi aren’t on the public internet
Many train Wi-Fi networks offer satellite connectivity for cellular black spots.
From our work in maritime satellite comms, we’ve found the terminal providers and integrators in many cases haven’t secured the terminal.
Ask your satellite comms provider if:
- the terminals are on the public internet – they should be on a private IP address space
- how they keep the terminal software up to date
- whether the admin creds are strong
Don’t believe me? Go search https://www.shodan.io/ for the brand name of your satellite / Wi-Fi provider and you’ll find terminals all over the public internet!
#6 If you use trackside equipment to fill coverage blackspots, check their security too
Lineside cabinets can be trivial for a motivated hacker to access.
Are network ports easily accessible? If so, could you detect a malicious attacker connecting to the network and attacking your systems?
#7 Are your media servers secured?
To minimise bandwidth, many operators offer media streaming from local servers on the train.
Don’t forget to include these in your security check, as they could create a stepping stone on to more critical systems.
There have been a litany of security issues in the past with streaming servers, so check that yours are locked down and kept up to date.
Conclusion
All too often I hear operators say that they’ve had a third party do all the provision and integration of passenger Wi-Fi. That’s a good plan, as specialists understand the technology.
However, those same Wi-Fi specialists don’t always understand security. All it takes are some simple oversights and your train control and ticketing networks can be exposed.
Don’t take their word for it, go ask for PROOF and go through the above checks yourself or bring in a third party to allay your concerns.














