A little while back we were testing for a client and found a rogue wireless access point through which we compromised the network.
Very 2004… except that it was a wireless screen casting system. Plenty of these can easily be found on https://wigle.net and vulnerable businesses can be identified and located.
Poor installation by the a/v supplier, weak default config by the manufacturer and a lack of security oversight by customers has exposed numerous businesses to trivial compromise.
The screen caster
The device in question is a Teqavit wireless presentation system.

It allows one to easily screen cast from a mobile device or laptop over Wi-Fi to a presentation screen or projector. Obviously, it creates a wireless access point in order to do this.
The default SSID is ‘WiD’ and there is no PSK. Not a good start.
The scary bit is at the rear:

Yes, that’s a RJ45 LAN port.
You guessed it: the audio visual supplier had installed the screen caster and also plugged it in to the corporate network!
Worse, the default configuration for the device was to bridge the wireless and wired networks.
PWNED!
So what? One would have to be in RF range and pretty lucky to find one.
Except that the SSID is searchable on wigle. It appears that installers either leave it default, or set the SSID to a ‘friendly’ name that indicates the device function.
Search wigle for “WiD” or “%wireless presentation” and you’ll find plenty of these devices:
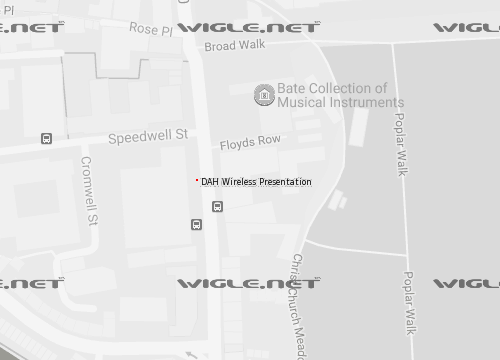
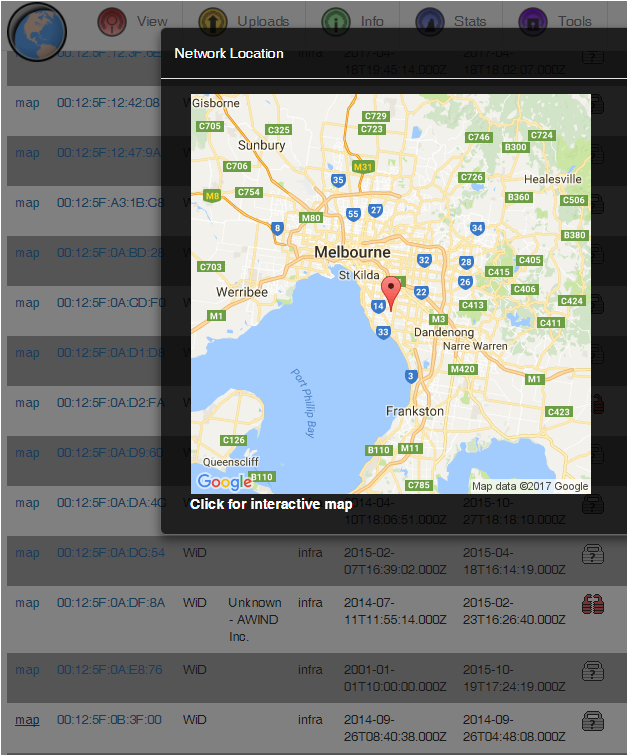
Who is to say that all of them are bridged on to the corporate network, but if the SSID is default there’s a fair chance some muppet installer plugged it in to the corp networks too.
Whilst we’re there, the embedded web server isn’t great either:

The default admin password is ‘Admin&11’, so if the connection wasn’t bridged and the default creds were unchanged, bridge away!
We haven’t spent any time looking at the firmware yet; there are clearly simpler issues to deal with first.
Advice
Do you have wireless screen casting systems in your offices? If so, go find out exactly how they work and be VERY sure they don’t bridge on to your corporate network.
We found the offending device in a ceiling void, behind a suspended ceiling, so be prepared to use a ladder!
Don’t just assume that the weird wireless AP near your office isn’t on your network. Go check properly.
Check you have the latest firmware on your Teqavit device too: we believe the latest f/w has better config and doesn’t bridge the wired and wireless by default.
For a/v installers: don’t just plug wireless devices in to the corporate network. Ask someone in the security department too.














