When is a vulnerability not a vulnerability? I’m not sure this counts as a vuln per-se, but some easily-fixed and simple manufacturer mistakes result in trivial hijack of…. yes… your smart luggage.
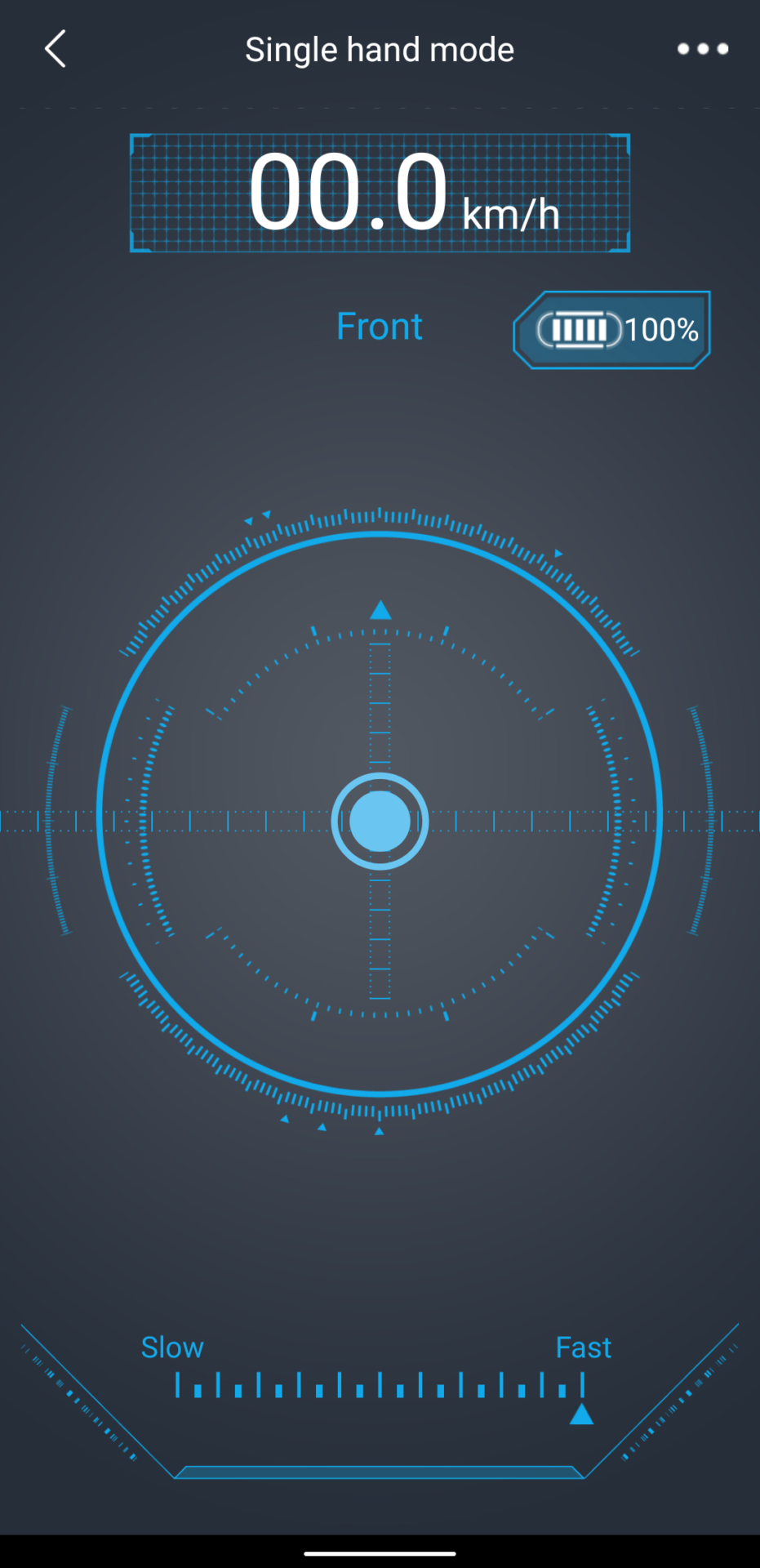
The Airwheel SR5 is the first smart luggage that we’ve seen. It can automatically follow the owner through an airport, avoiding obstacles along the way.
At €649 / $745 it certainly isn’t cheap. I’m also a little confused by its purpose: it’s a cabin-sized bag that can easily be pulled along using a handle, like conventional cabin luggage.
It strikes me as being smart for the sake of being smart, rather than solving a genuine problem.
Anyway, we had to buy one to see what we could do with it.
The luggage
A couple of wheels drop down when the luggage is powered up. These are driven from a removable battery pack.
The owner wears a watch-style BLE device that the luggage will ‘home in’ on. As the wearer walks off, the luggage pays attention and follows.
The luggage has four ultrasonic sensors for obstacle avoidance. In practice, we found the luggage would often take random turns in to walls and crash. This may be a result of RF signal interference or reflections. Hard to say without spending a lot of time on it. It also got ‘lost’ quite a bit, meaning the owner had to return to the luggage to get it to start following again.
Anyway, there is no security for the pairing process for the luggage to the wristband. No particular issue there, as it’s highly unlikely someone else would be trying to pair their luggage at the same time as you in the same location.
But…
There’s also a mobile app. It’s quite fun too: one can manually control the luggage on screen. It goes quite quickly too!
In order to pair, there’s a PIN of 11111111.
What’s unusual is that pairing with both the wristband and mobile app is possible concurrently. This is relatively unusual for BLE devices – typically connection to only one device is possible at a time. Yes, later versions of BLE support multiple concurrent connections, but it’s still unusual to see it implemented in consumer IoT.
See where this is going yet?
If the luggage owner hasn’t paired their luggage to the phone app as well as to the wristband (why would you?) then anyone else in Bluetooth range can trivially connect to their luggage and drive it off in a different direction. Smart luggage hijack!
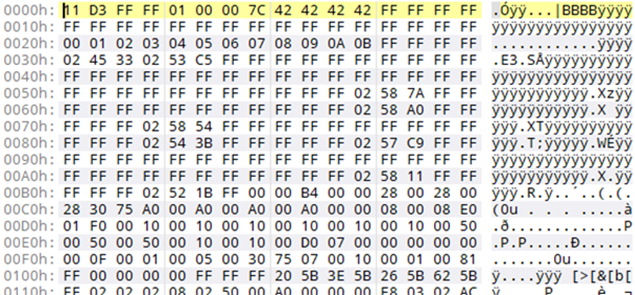
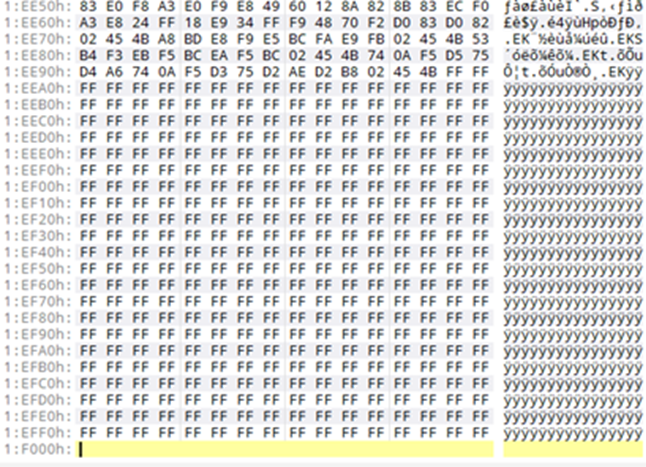
The Airwheel mobile app isn’t in the Play Store either, so has to be sideloaded. This isn’t a good sign for security. This app also allows new firmware to be pushed to the luggage. We had a quick look at the firmware header and tail. There was no evidence of firmware signing, meaning that one could push modified firmware to the luggage. Rogue smart luggage!
Fixing this
First, Airwheel would do well to force a change of the Bluetooth PIN on first use.
However, this doesn’t prevent the owner from never actually setting up the mobile app and never being forced to change that PIN.
Better would be to have a physical switch on the luggage to only allow pairing with the mobile app when the owner specifically chooses to.
Of course, they could also put a unique PIN per device on a piece of paper or similar on the inside of the luggage.
Firmware signing would be wise, as would putting their apps in to the Play Store.
Final thoughts
So what. It’s only a smart suitcase. Does it really matter? Maybe:
Airwheel use the same app for smart wheelchairs, including a separate remote control handset instead of a wristband. This is a really interesting use case, as the user of the wheelchair can have it drive to them, meaning they are more independent. Cool!
Except, someone nefarious could hijack the wheelchair too. Fail.














