Home security cameras whether indoor or outdoor are becoming very accessible and popular, especially those with cloud backup/recording facilities. The idea is simple. The camera sends a video feed up to the provider’s cloud storage. You can then review your footage should an incident occur.
What are we looking at?
Following a tip-off from a concerned citizen we decided to investigate the offerings from MySpotCam. We purchased the outdoor version which has free 24-hour recording and storage, a smartphone app, and is weather proof.
The MySpotCam camera also has motion detection and infra-red capabilities, with the ability to have alerts sent to an email address. A live feed of the camera and stored material for the last 24 hours, or 7 days if you pay a subscription, can be viewed either via the smart phone application or via the web site. The camera is designed to be connected to the owner’s Wi-Fi so it can be moved around the property easily.
Let’s investigate
A quick nmap scan reveals the following:
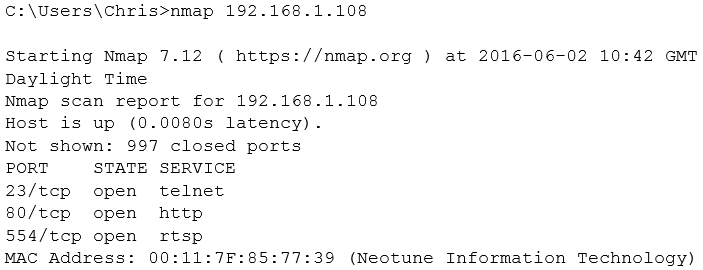
Telnet? That can’t be good surely. But we’ll come back to that. Let’s take a look at the web server being offered up. Browsing to the server gives this error:
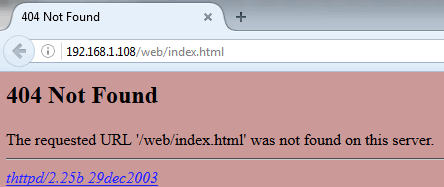
OK, so no index.html. But we can guess that a /web/ directory probably exists, let’s browse to that and see what we find:
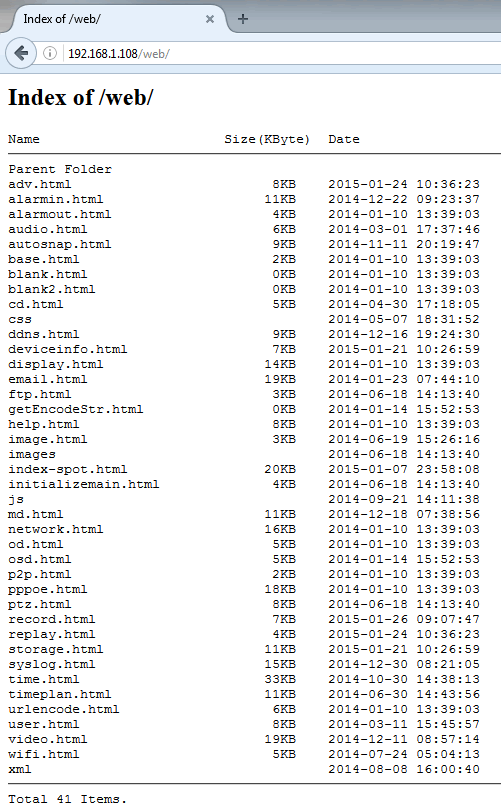
Interesting! Directory listing is enabled. I’m not sure I should have access to all this functionality (I have customised my onscreen display to show the current time as a watermark in the top corner, which I thought was useful). Checking the wifi.html gives some worrying information:
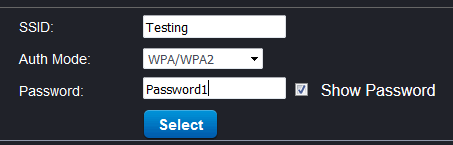
Oh dear, so anyone with a connection to our network can reveal the Wi-Fi password. Sure, it’s likely that most people connected to the network have been given the password or a connection already. But it’s not hard to de-auth the camera from its Wi-Fi point and create a fake AP with the same SSID. And from there connect to the webserver to reveal the WPA PSK of the real AP, in plain text.
Also, more worryingly, ours is the waterproofed version, allowing it to be located outdoors. The mounting plate can be screwed to the wall, however the camera just snaps into the plate with a couple of clips making it extremely easy to remove. On the back of the camera is a switch which fires up the camera’s internal AP so the smart phone app can pair it with the owner’s Wi-Fi for initial setup or a different Wi-Fi access point if needs be. Unfortunately the web server is available via the internal AP too making it really trivial to retrieve those plain text creds.
There’s more
Not a great start. But let’s move on to our concerned citizen tip-off. It appears each camera has its own ID which takes the form “SWA000” followed by 6 mixed case characters. I should also point out that each camera has the ability to be set as private (which is the default) or public i.e. the stream/feed is published on the SpotCam web site. When you browse your live feed from the MySpotCam web site, this little snippet appears in the site’s source code:
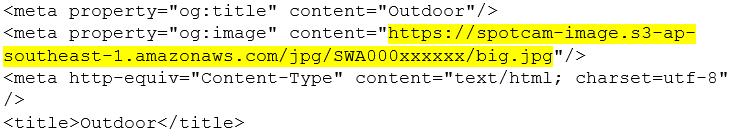
“Outdoor” is the name I gave to my camera, but what’s that jpg image coming from Amazon?
Browsing to: https://spotcam-image.s3-ap-southeast-1.amazonaws.com/jpg/SWA000xxxxxx/big.jpg shows a current snapshot of the camera, no need for credentials or to be logged in, it’s publicly available even though the feed is set to private?!
It’s my guitars, what the hell?

We could brute force the ID with a script to prove the theory, but we’re not comfortable with the legality of it, nor what we might find so we haven’t. However I’m pretty confident it would be straightforward to achieve.
Further issues
Some other issues we discovered. Going back to the telnet port, the hardware is very popular (hi3510) and hence the telnet password is pretty well known so it’s possible to log in and change whatever you like in the base operating system. Also, as we’ve seen, the /web/ directory is browsable, but so is the /spotcam/ folder and there were insecure privileges on the /tmpfs/ folder allowing you to browse to files like /tmpfs/syslog.txt. It’s also possible to view the RTSP stream from the local LAN. Opening the following in VLC rtsp://192.168.1.10:554/11 gives a live feed without needing any authentication. 11 appears to be the highest quality.
So:
• Easy to extract the owner’s Wi-Fi password
• Publicly available snapshots of private feeds
• Poor webserver configuration
• Well known telnet password
Conclusion
Overall, not the kind of security product I’d want in my home and allowing snapshots of private feeds to be publicly available doesn’t fill me with any confidence that security has been baked into this product’s development.
This whole situation is even more surprising/depressing given that Spot Cam UK is listed as an SBD (Secured By Design) provider by the official UK Police security initiative.
A representative from MySpotCam was eventually found and we highlighted the issues to them in January.
They indicated that the issues we reported would be fixed in March, but as yet we still haven’t seen or heard anything from them.














