The World we’re living in is changing fast, from the way we work to new threats to our livelihoods. As such many of our clients are turning to us for reassurance that they will be able to respond to a cyber incident if the time comes. Many are now investing in incident response planning and simulated cyber incident tabletop exercises. Before we take a client on this journey, we first assess their current level of maturity for incident response. More frequently we see that the greatest gaps are in the identification and detection of an incident.
You can have the greatest team of incident response professionals poised, waiting to execute the best possible response plans and play books, but all of this is worthless if you can’t detect the breach quickly. A report produced by the cyber security firm Mandiant in 2020 on Security Effectiveness found that 53% of successful attacks infiltrated an organisation without being detected, and 91% of all incidents generated no alert at all. Two years on from this report it is highly likely that these numbers will only have gone up with the increases in state sponsored activity, increases in APT groups offering services for hire, and level of zero-day exploits being exposed.
Based on a survey conducted by IBM in 2020 on average an organisation will take 197 days to identify an incident and a further 69 days to contain the breach. I can support this with my own experiences as a DFIR consultant responding to client breaches where 120 – 270 days is the average I have experienced. Many of those were payment card data breaches where an external third-party (the banks themselves) had detected and identified a breach at the retailer.
Another survey conducted this time by Deep Instinct in 2021 identified the average time to respond to a detected incident was 20.9 hours. This survey highlighted that even when an incident was detected it would still take an organisation a further two days to organise and mount any effective response.
All of these surveys and statistics point to one conclusion: there is a large gap between an attacker breaching the defences and an effective response being engaged. Whilst having an effective and well-rehearsed incident response plan and process is a must, if an organisation is to recover from an incident, it first must be detected.
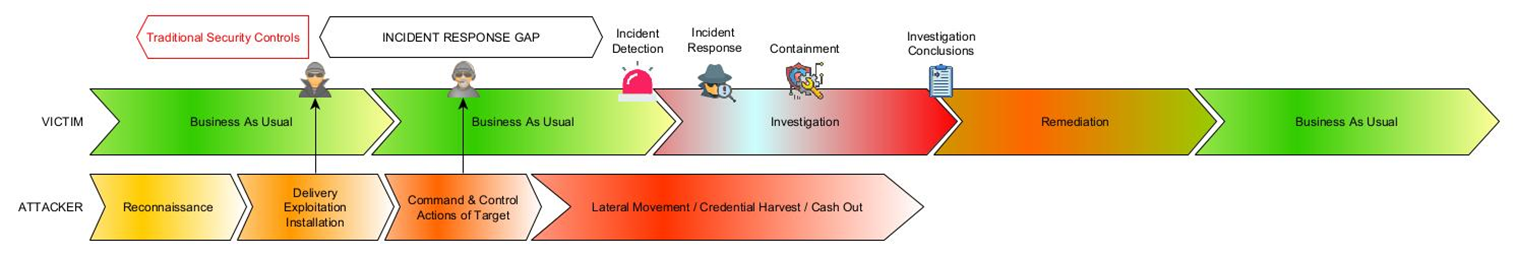
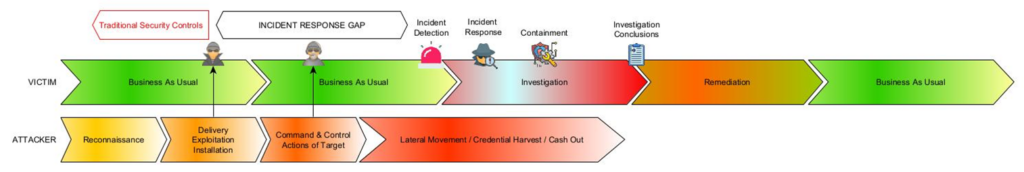
Figure 1 – Representation of the gap in incident response
This gap between intrusion and detection has been classified by the cyber security company Mandiant as “Dwell Time” and they have tracked the average Dwell Time over the past two decades where they have seen it decrease from 417 days to 24 days in their 2021 report.
This poses an interesting question, if we look at the studies and figures I have quoted above. Is this a true reflection of how well organisations are handling attacks now or is this decline in fact linked to the speed and efficiency that attackers are using to cash-out, often through ransomware, exposing the attack to the organisation.
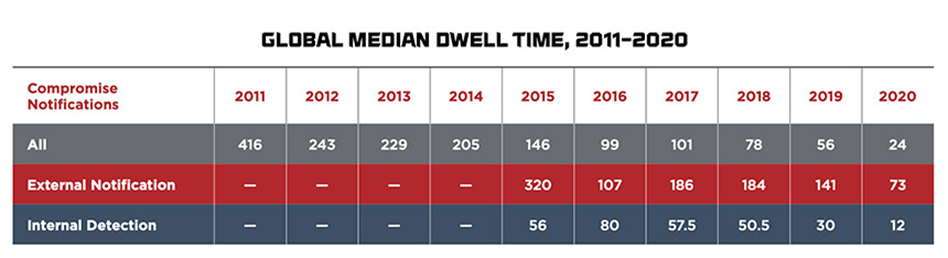
Figure 2 – Global median Dwell Time 2011- 2020 (source Mandiant)
To really bring these dwell time statistics into prospective we need to compare them with the other side of the coin, break out times (the speed with which an attacker will move laterally from the initial point of intrusion to compromise another host). Breakout times vary based on the origins and motives of the attacker, however, based on research conducted by CrowdStrike, the average breakout time is 1 hour and 38 minutes. This figure demonstrates the speed an attack can move and integrate themselves into your environment, long before you have had a chance to respond.
It can therefore be said that the true matrix of any cyber security effort is dwell time. To measure your own dwell time, you need to review three metrics:
- Time to detect and intrusion,
- Time to investigate an incident, understand criticality and scope, and what response actions are necessary,
- Time to respond to the intrusion, eject the attacker, and contain any damage
No matter what size the dwell time, one fact remains, organisations, on average, fail to detect a security breach early enough in the kill chain to prevent significant impact or damage. So, what can be done to reduce this significant gap in incident response?
An exercise with a Red Team, to demonstrate how real-world attackers can combine exploits and tactics to achieve their goal. It is an effective way to show that even the most sophisticated technology in the world means very little to an attacker and will help you to identify your capabilities to detect attackers within your environment and assess your own dwell time. This type of exercise can be expanded to include the time response and capabilities of the Blue Team to defend against simulated attacks – called Purple Teaming.
Tips to reduce your dwell time
Defence In Depth – Creating a network infrastructure with layers like those of an onion. At each layer intrusion detection should be put in place. Any critical systems and data should be held in the very centre of the network. The means of detection should be different throughout the network, prevent an attacker from finding a single IDS bypass.
Automated detection and response – invest in tools that will provide continuous event collection and monitoring of your assets and threat intelligence.
Advanced threat hunting solution – 62% of attacks are completely fileless and therefore may not trigger traditional intrusion detection or malware detection tools. Deploying an advanced threat hunting and threat intelligence solution throughout your environment cold dramatically reduce dwell time and improve your ability to respond.
Responding to alerts – Many organisations invest in expensive IDS, such threat hunting solutions or Security Event and Incident Management tools, but then become completely overwhelmed with the alerts they stop responding to the alerts. Refining your IDS to only alert on high or critical events and build in responding to alerts into your teams’ daily processes.
Response plan – By implementing a well-trained incident response team with clearly defined roles and responsibilities, and a documented incident response plan will reduce the time it will take your team to respond and mount an effective response, empowering your staff to react.