Penetration testing is like a car MoT or a service: it’s a snapshot in time of the security posture of a given environment. However, whilst a penetration test is a critical part of ensuring an environment is secure, you also need to know what is going on for the other 51 weeks of the year.
This how-to is intended to provide a quick guide for wireless testing. The idea is to get people up and running so they can start to discover what wireless networks are around. This is especially useful for companies/government/etc as, occasionally, ne’er-do-wells put rogue access points onto the corporate network. Finding such APs is critical in order to ensure that access to the private internal network isn’t broadcast outside of the physical boundary….
Kit
One of the most important aspects of wireless testing is the kit. Back in the dark ages of wireless testing you needed the right PCMCIA card (Orinoco Gold!), Kismet, and a great deal of patience to get them all working together. Nowadays things are a lot more straightforward and tools like Kismet are more mature. In general, I use the Alfa Network AWUS036H USB wireless adapter:

This has the advantage that it can be used with either a native Kali install or with a VM as it can be directly connected to the virtual machine. This is important as the device needs to be set into monitor mode (more on that later).
The next question regards what platform to use for the exercise. This all depends on what you’re looking to achieve. If it is a general scan of the wireless environment but spread over a reasonable area, then I recommend getting a small laptop or a netbook. I use either a Samsung N110 netbook or a HP EliteBook 2530p (thank you eBay!). The netbook is light and the battery lasts for up to 7 hours. Ideal for situations where a lot of walking is required and where no power is available. The EliteBook is heavier but still much more portable than a standard laptop. Unless you have arms like Arnie and the stamina of a Mountain Goat then I recommend either the netbook of the EliteBook for walking around. There are some options with Android based tablets. YMMV with those….
If there is no wandering around required then stick to your normal laptop, or even desktop, and run everything from a virtual machine.
What operating system?
Kali Linux is the best bet here. All of the tools I’m going to discuss are included as standard, and the Alfa card works without any fuss. The last thing you want when it comes to it is to have to mess around with the OS and/or hardware to get things doing. For me, the EliteBook and netbook both run Kali natively. However, that isn’t always an option so get Kali installed in your virtual machine software of choice. I’m not going to go into how to install Kali, that’s out of scope for this how to. I’m going to assume that you already have it installed and running.
Monitor mode
This is a critical aspect of wireless testing. Monitor mode is functionally equivalent to promiscuous mode for an Ethernet card. When set into monitor mode, a wireless card will “hear” everything in the air and pass it onto the listening application, for example Kismet. Kismet sets the card into monitor mode when you provide it with a source (e.g. wlan0), but there are other ways such as the aircrack suite of tools. AS we’re only using Kismet, I won’t go into any more detail, I’ll save that for a later blog post.
Kismet
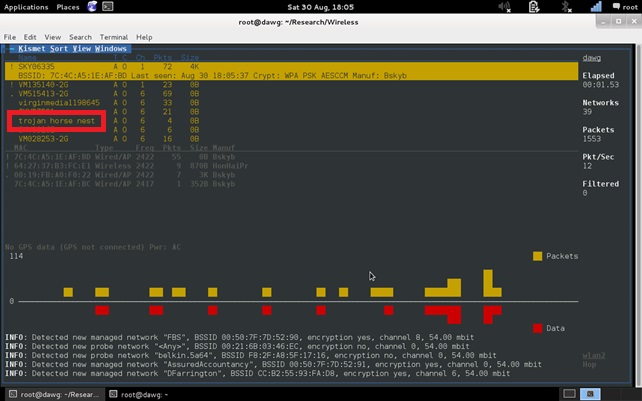
Kismet is probably the most popular of the wireless tools out there. It runs on all flavours of Linux/*BSD (and, allegedly, Windows!). It’s a command line tool, but it uses “curses” to display data in a terminal-based windows environment. You need to be reasonably comfortable with the command line, such as how to invoke a terminal and run a program from it. When Kismet first starts there are a couple of things that need to be done. One is to set the source that kismet receives data from- the network you want to check out.
The screenshot below shows the network “trojan horse nest” (no, I didn’t make it up, my neighbours are beginning to scare me….):
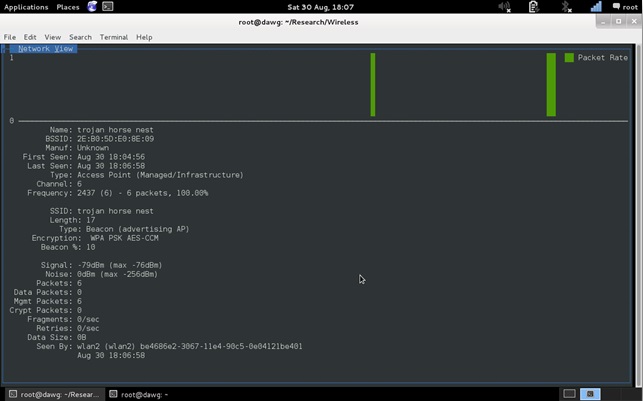
…then we can dig deeper. In the following screenshot we can see more information about the network. For example, as well as the ESSID we can also see the BSSID. The type, channel, encryption type, and other useful information is also available. It should be noted here that Kismet, for some reason, isn’t always accurate with the encryption type. Airodump-ng does a better job of determining what encryption is being used, but we’ll cover that in another blog post.
What are we looking for?
Once everything is set up, we need to know what the purpose of the wireless survey is. There are a number of goals that need to be achieved:
- A site survey of the campus. This is usually used to determine whether all of the legitimate access points are working, where they are, and signal strength in various locations.
- A site survey to discover rogue access points. Has an employee, contractor, or malicious agent installed a rogue access point? What is it called and where is it?
- Assess the configuration of legitimate access points. For example, test the guest network to make sure it really is doing what you’ve been told it is.
Of course, all of the above (and others) can be achieved in the same exercise.
One of the fun things to do, back in the day, was to go on a “wardrive”. This is taking your setup, along with a GPS, on a drive to see what access points are out there and to see how many unsecured or poorly secured access points there are. There’s an important point here: under no circumstances should you attempt to access an access point that does not belong to you. It’s illegal and you could end up in jail. You have been warned!
The picture below shows a typical wardriving set up (vehicle not shown in the picture, mainly because it won’t fit in the living room):

Conclusion
Wireless networking is, literally, almost everywhere. Hotels, fast food joints, coffee shops, and even public transport provide WiFi connectivity. It’s almost as if we can’t do without some form of Internet connection. Wireless site surveys are helpful in determining what legitimate access points are in an environment and whether there are any rogue access points. It can also help in determining what the configuration is and therefore whether it matches what was expected. In my next blog post I’ll go into detail about tool use with Kismet.