Contrary to alarmist stories in the press, it really isn’t practically possible to hack an airplane from the in-flight entertainment system (IFE/IFEC). The ‘C’ adds Connectivity, so internet access
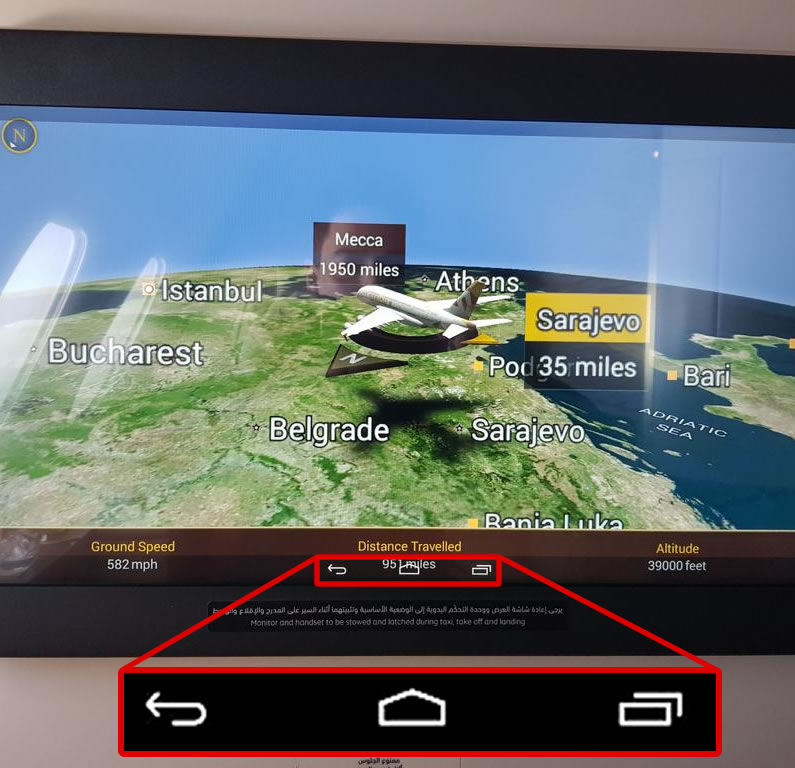
Whilst earlier moving map systems did take a feed from the flight management system, particularly so prior to widespread adoption of GPS when we relied instead on inertial reference systems, there has been a one-way data diode in place on that connection for a long time.
That feed would report position, speed, altitude etc, populating the map so that passengers could see how many movies they still had time to watch.
You’ll be familiar with the ‘box’ under the seat that feeds the IFE screens. We have a couple here; they’re older versions and are simply a 386 PC.

More recently, you’ve probably seen Android based IFE screens, evident from the navigation buttons. These offer potential for significant weight saving as the under-seat box starts to become unnecessary.
So, if the Aircraft Control Domain (ACD – the flight controls) can’t be hacked from the IFE, why does everyone get animated about IFE security?
Primarily to stop passengers getting panicked!
Consider the following scenarios
All the IFE screens pop up with scary messaging, indicating that the plane has been hacked and will shortly crash
The moving map misreports its position whilst in cloud and shows the plane descending directly towards an iconic landmark
A ‘breaking news’ report is broadcast, indicating that the flight has been hijacked
At the least these incidents would be very unsettling for passengers. At worst, they might lead to an airborne riot as passengers attempt to break in to the cockpit in the belief that they are trying to ‘save’ a flight crew overpowered by hijackers.
Would reassuring words from the captain over the cabin PA placate anyone? I doubt it.
Would turning off the IFE simply appear even more alarming?
Alarmist, possibly misleading, media coverage would also likely do further damage to the industry. ‘Airplane hacked’ is a tough story to correct, even when the truth is that only the IFE was tampered with & there was no risk to the ACD.
So that’s one good reason why the security of in flight entertainment systems is important.
There are other good reasons too:
Internet access in flight is becoming more widespread. It’s rarely free of charge, certainly in economy/coach seating, so becomes a useful revenue stream for airlines.
Billing is typically handled by credit card, so there’s another good reason for the IFE to be secure. Placing keyloggers or other card-data related malware in to the IFE could be an interesting way of scraping card numbers for fraud.
Tampering with the system to gain increased bandwidth or avoid payment isn’t uncommon where internet access is metered/payable. Expect to see attempts to bypass payment systems.
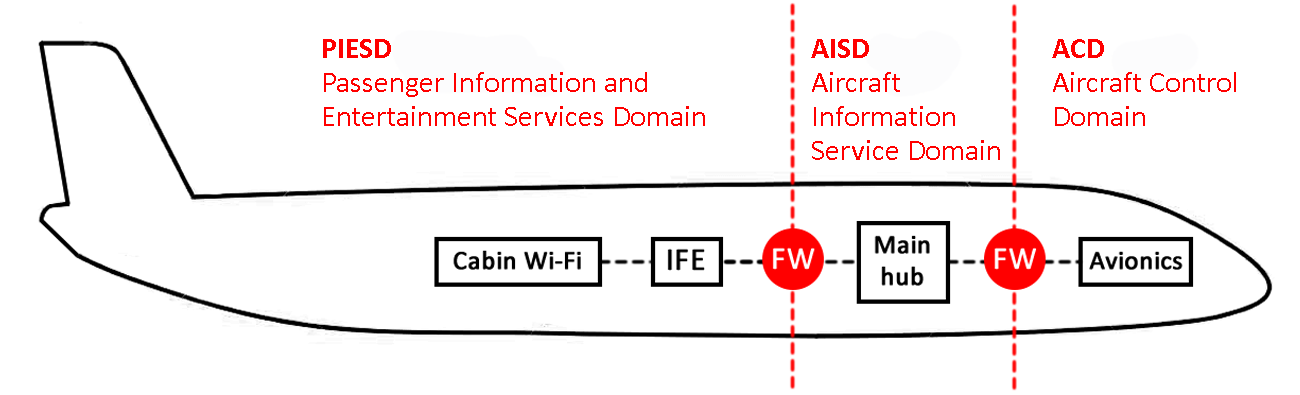
Whilst satellite terminals on board are one of the few places where IFE and ACD/PIESD (Passenger Information and Entertainment Services Domain) networks touch, they are very carefully segregated. ARINC 821 describes the requirements for segregation. However, defence in depth principles are wise here: why let the attacker bypass a layer of defence, so it’s worth keeping the IFE secure from attack.
Losing the IFE system through a hack in flight is also very irritating for passengers and crew alike. On long haul flights, complaints will be significant, often resulting in partial refunds or frequent flyer miles being issued to compensate customers for the lack of IFE. Whilst modern IFE systems are pretty robust and secure, it’s harder to defend against an airborne DoS of the network. Do we really expect an airplane to have on-board DoS mitigation?
Finally, it would be very disturbing if streamed content was tampered with. Even if not alarmist messaging, streaming unsavoury content to all pax screens would cause reputational damage.
Detection
One of the biggest challenges will be detection of a non-visual incident. Obviously, tampering with displayed content will be very obvious and trigger an investigation on the ground, however a more subtle attack would be very tough to detect.
Logs would have to be downloaded and analysed after landing, well after the incident. That assumes that logging is even sufficiently capable to monitor security incidents and note indicators of compromise.
Whist there is discussion of a SIEM-style system for the ACD and AISD (Aircraft Information Service Domain), I’m not aware of anything similar for the PIESD. There may be an opportunity there for a suitable solution.
Real time analysis is always going to be difficult though: should one even attempt to monitor airborne PIESD activity for rogue activity remotely?
Conclusion
IFE security is important, but not for the reasons you might expect.
Fortunately the major vendors in this space take security very seriously; modern in flight entertainment systems are rigorously tested.
However, older systems are not so robust. One of the big challenges is maintaining security of IFE systems that weren’t designed with today’s security approaches in mind. It’s not uncommon to see 8-10 year old IFEs in older fleets. Indeed, we worked on a recently-decommissioned short-haul airframe that had a S-VHS VCR for the video screens and a C90 cassette for cabin music. Not so easy to hack, that one!
















