I admit it, I have an Aga. Before I get a tonne of stick for energy inefficiency, I drive electric cars, have solar thermal panels and heat the house using a log boiler (that also has a Wi-Fi interface, more on that another time though).
Anyway, the latest Aga models are loads more efficient, so I looked in to replacing it. One even features ‘Total Control’ through a mobile and web app. I wanted to know more about its security before spending extra on this option.
We found that even Agas can be hacked. Seriously.
Inspecting the mobile app revealed that it simply passes messages to an API. Unsurprising.
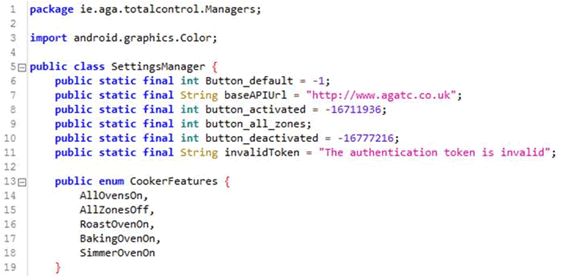
However, the mobile app communicates over plain text HTTP. The Android app explicitly disables certificate validation through use of ALLOW_ALL_HOSTNAME_VERIFIER. Even if it did offer SSL, it would thus be trivial for rogues to intercept and modify traffic.
Digging deeper, it turns out that a physical module is added to the Aga. It contains a GSM SIM, to which the customer has to subscribe to Orange/EE (at £6/month).
It looks like this; note the Tekelek branding on this one:

The Aga is controlled by SMS.
Seriously, the web app sends text messages to your cooker.
That’s really quite an odd concept, particularly as many Agas are in remote locations in the country so don’t have great mobile reception. Yet internet access and Wi-Fi routers are ubiquitous. So Aga’s choice of mobile comms costs customers >£70 extra per year and doesn’t help those in poor mobile reception areas!
We can only assume that Aga did it this way to keep costs down. A shame, as a Wi-Fi module done right and conventional mobile app/API would be unlikely to have cost them much more to develop.
The web app is where things got quite interesting
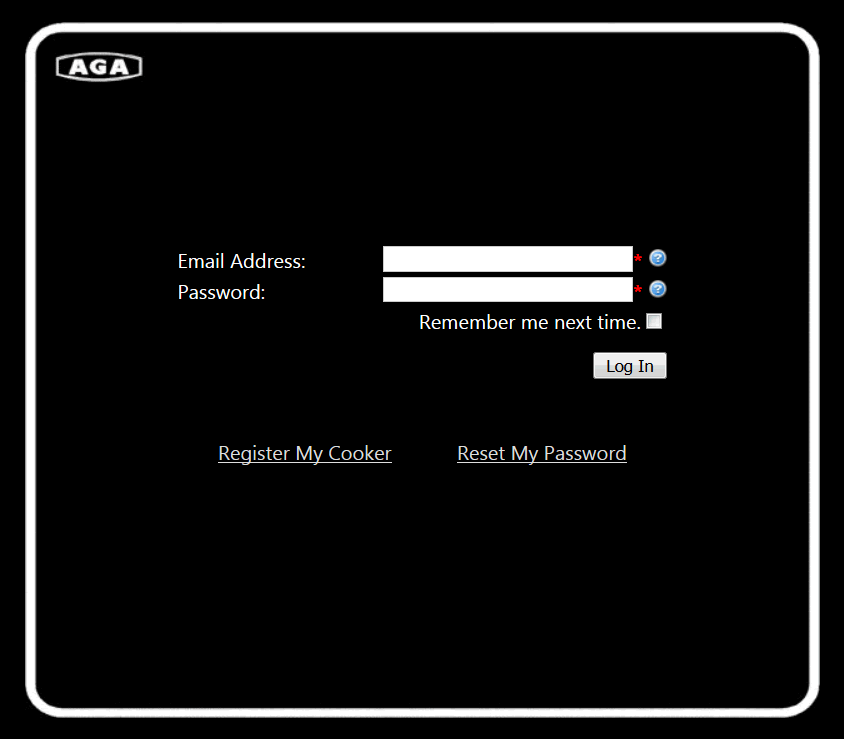
Here’s the login and registration page, all over plain text HTTP, just like that mobile app. They hadn’t bothered to protect customer data in transit at all:
There’s enumeration of the SIM Card Number. They don’t actually mean that, they actually mean the phone number. Mistype an entry and you get an error.
Put in a valid number (i.e. +44 845 712 52 as suggested by the app when you make an invalid entry) and you’ll see that it’s already registered. It’s not actually a valid phone number, so likely someone has been interfering with this web site!
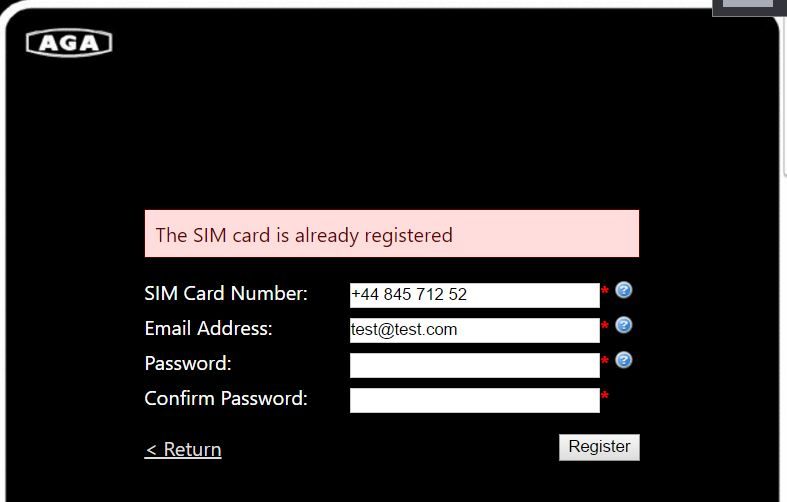
So those with nefarious intentions could enumerate a list of all the valid Aga cooker phone numbers. Time consuming, but likely effective.
Whilst we’re there, the password policy is only 5 characters. This is starting to get pretty irresponsible of Aga; customers will have their cookers compromised.

But surely there is validation of the number and authentication of messages, right?
Umm, no. There’s no link sent to validate the number or the account. Nothing.
Here’s the format of the message:
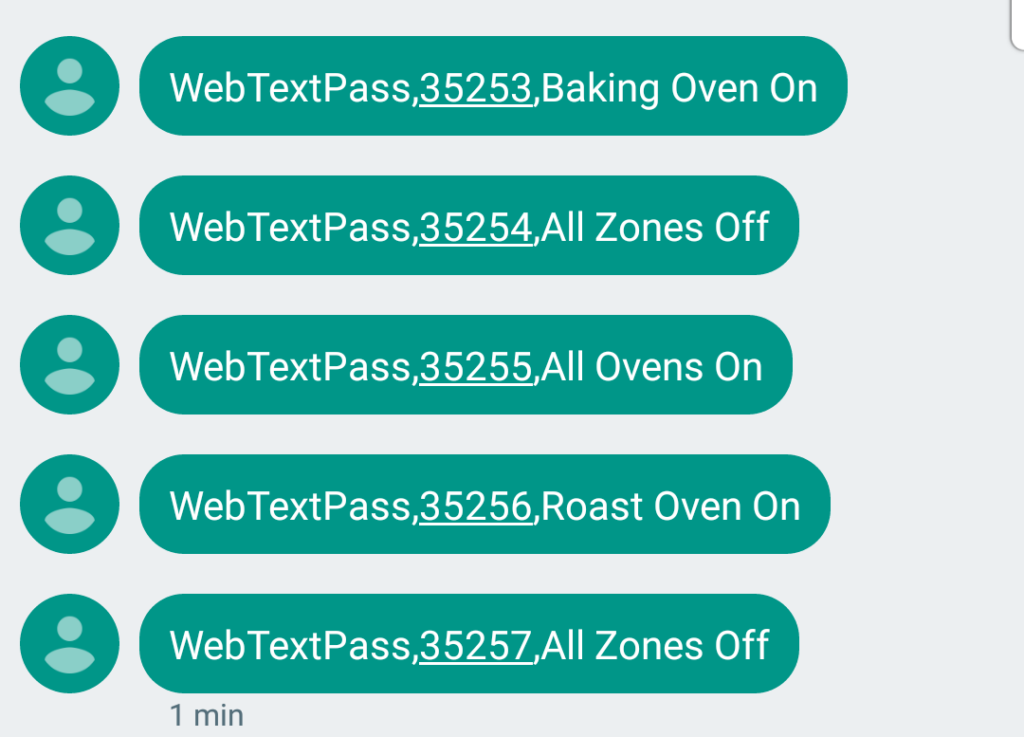
Yes, hackers could turn other people’s Agas off.
All you have to do is simply send a text message to the Aga. We didn’t, but it would be trivial for less ethical culinary threat actors to do so.
You probably know it takes hours for an Aga to heat up. Switch it off, annoy the hell out of people.
I suppose it would make my Aga rather more efficient. By never being on…
One could also power up people’s Agas when they’re not looking, wasting electricity. They draw around 30 Amps in full heat-up mode, so if you could switch enough Agas on at once, one could cause power spikes. That’s a bit fanciful though.
The web interface also lends itself to spamming the hell out of people using SMS at Aga’s expense.
Disclosure was a train wreck. We tried Twitter, every email address we could find and then rang them up. No response to any of the messages we left.
Come on Aga, sort it out. This isn’t acceptable. Get rid of the silly SMS based remote control module and put in a nice secure Wi-Fi enabled module with mobile app.
We believe that a business called Action Point (link opens Google cached PDF content) led the integration project. This led us on to the GSM module which we think is manufactured by Tekelek. Tekelek have a history in remote monitoring of oil storage tanks, heating systems, process control and medical devices among many things. These appear to be monitored using SMS, so I wonder where else this bizarre unauthenticated text messaging process might lead…
Recommendations
Aga: Take down the www.agatc.co.uk web site and fix these issues.
Aga owners: This only affects you if you have the latest Total Control cooker and bought the remote control option.
Will hackers take control of your Aga? Who knows, but it certainly shouldn’t be possible.
Disclosure
As always, we attempt to establish private contact with the manufacturer in order to pass details of the security vulnerability and agree a disclosure timeline.
This doesn’t always go well in IoT and certainly didn’t with Aga Rangemaster!
Timeline
30th March 2017 – Tweeted @aga_official asking for a follow so I could DM them details of a security vulnerability.
No response.
3rd April 2017 – Tweeted them again, same subject but also asked for email or phone contacts if that was preferred.
No response.
3rd April 2017 – Emailed security@, customerrelations@ and [email protected]. We received automated responses from the latter two indicating that we should expect a response within 72 hours.
No response.
6th April 2017 – Figured I would try their PR agency, Mabel Gray. Found the lady responsible via Google, then went to their web site. Was presented with a blank page and MySQL error!
6th April 2017 – Called the agency and asked to speak to the lady. Was informed that she was out of the office. I asked if they dealt with Aga PR, which they confirmed they did. I asked if I could report a security vulnerability to them. Was told that I couldn’t and to consider emailing her.
9th April 2017 – Discovered that @Aga_official had blocked me on Twitter! I was furious and nearly disclosed there and then; after all we’re trying to do them a favour by disclosing privately, then to have the door slammed in my face. But calmed down a bit.
10th April 2017 – Picked up the phone to Aga switchboard and asked to speak to Dave Carpenter (technical director and had managed the IoT integration, from Google searches) – call rang out with no voicemail.
Tried switchboard again, asked for the PA to the CEO. Was told that wasn’t going to happen. Explained in a bit more detail, was put through to ‘technical’.
Spoke to a Chloe who was friendly and helpful. I explained the urgency of the situation owing to the above failed disclosure process. Was assured of an urgent call back either ‘today or tomorrow’ (11th)
Finally, a friendly Andy from Aga technical support called. We had a 10 minute chat about the issue, though it was clear that he had no involvement or knowledge of the mobile app. I stressed the urgency of taking down the AGA TC web site today. I was quite disappointed that his attitude was along the lines of ‘we’ve had no reports of customers having their Agas hacked’ as that really missed the point. Let’s see…
I rang Andy back later this morning to see what progress had been made. Apparently my report had been passed on to ‘product development’. I asked if the web site would be taken down today, but the response was non-committal. I asked if I could be put through to the product development team, but apparently not. I then asked if I could speak to the technical director, but that wasn’t possible either.
I don’t blame Andy – he was trying to help, but it seems no-one at Aga had briefed their technical team about the mobile app, nor how to escalate a security incident.














