(Credit also to @ghostie_ and @tautology0)
According to the ONS 86% of households in the UK are now connected to the Internet. A huge proportion of these are likely to be using a wireless router to allow their devices to connect to the Internet over Wi-Fi, and probably with the default settings left unchanged.
Most of those routers come with a password to connect to the Wi-Fi, and it’s that Wi-Fi password that we’re looking at.
The technology used to protect your Wi-Fi password is called WPA2, and is the successor to a flawed technology called WEP. WEP was extremely easy to crack, often crackable in under an hour. WPA2 doesn’t contain that flaw, so your Wi-Fi password is safe right?
Well, almost.
Because Wi-Fi is an over the air technology, it’s possible to capture the authentication handshake between your device and your ISP’s router. Remember that these days we’re not just talking about a laptop or a mobile phone, the Internet of Things means that your IoT fridge or doorbell will be making the same handshake too.
Brute forcing is a computational technique that tries every single possible combination of words, letters, and/or numbers. Given that WPA2 allows the password to be up to 63 characters, that could take a long time.
However, ISPs seem to be following set patterns when it comes to choosing their default Wi-Fi passwords, and that helps us a great deal! So, we’ve researched some common ISP Wi-Fi passwords, and using our custom password cracking rig, have listed the time it would take to crack the captured authentication handshake to reveal the Wi-Fi password.
| Device | PSK character set | PSK length | Time to crack |
| Orange | [2345679ACEF] | 8 | 5 minutes |
| AOL | [0-9,A-Z] | 8 | 2 hours |
| Virgin SuperHub | [abcdefghjklmnpqrstuvwxyz] | 8 | 2 days |
| Sky | [A-Z] | 8 | 4 days |
| TalkTalk | [ABCDEFGHJKMNPQRTUVWXY346789] | 8 | 5 days |
| BT HomeHub | [2-9,a-f] | 10 | 5 days |
| Plusnet | [0-9,A-F] | 10 | 19 days |
As a demonstration, we took a BTHome-Hub5 we had laying around, captured the authentication handshake and using the formulas above tried to crack the password.
Firstly we tried this using a standard laptop with a reasonable graphics card installed. As you can see this would take roughly 72 days to crack:
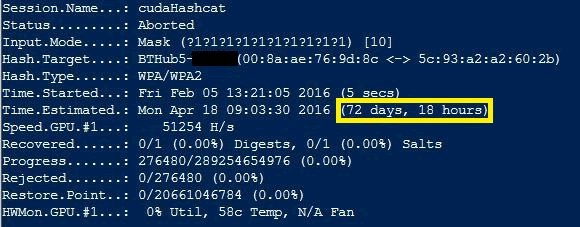
However, if we take the same handshake and attempt to crack it using our PTP password cracking rig, the estimated time comes down to a very nice 5 days. This isn’t great!:
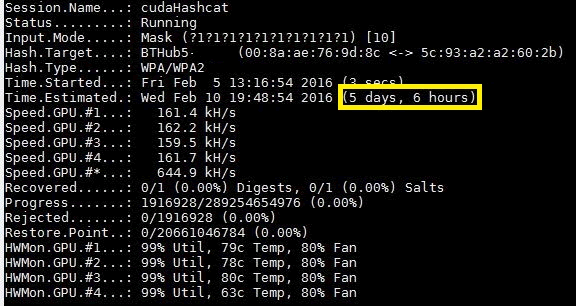
So, what’s the risk? Well, if malicious person does capture your Wi-Fi authentication handshake, and crack it to reveal the password, they can connect to your home network and from there it would be possible to see all the devices connected to your network. If any of those devices have vulnerabilities, i.e. you haven’t been keeping up to date with patches then they could take full control of them.
Also, most ISP provided routers have default user names and passwords to access the administration side. With that access, the malicious person could control all of your internet traffic, including capturing any user names and passwords that you use, for things like internet banking for example.
Of course, most ISPs in the small print, suggest changing the Wi-Fi password. But, a) who reads the small print, and b) how easy is it for the average home owner to change the password? It would help if ISPs increased the number of characters in the password. Even a simple increase from 10 to 12 characters would increase the cracking time from five days up to many many years. However, the best thing is for you to choose your own, complex Wi-Fi password and make it as difficult as possible for the attacker.













