My colleague Andrew and I were poking around on the internet last week as part of our ongoing research in to DVRs for CCTV systems.
Mirai is not the end of this – we’ve subsequently made a ridiculous number of findings on DVRs, including RCE, though we’re working through responsible disclosure with the vendors concerned before release. Probably the most amusing find was a DVR that hooks up to your home alarm system. Mirai default creds -> compromise DVR -> disable your home alarm. Nuts!
Anyway, on the LinkedIn page for a CCTV installer, we found the following image:
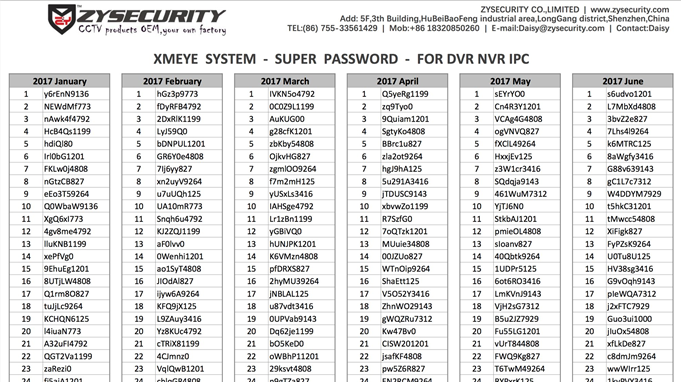
Yes, seriously. That’s a per-day super user password for a DVR service. As @InfoSecSpy pointed out on Twitter, one-time pads make for near-perfect encryption… assuming you can transmit the pad safely.
It’s not the only source either: @mikko noticed the same document was stored here and I then found some of the credentials on an Arabic language site here – search for ‘NEWdMf773’
Now, the hard part – working out what the heck the password is actually for!
The document references XMEye. Now, http://xmeye.net is a cloud service offered by ZY Security for remotely accessing DVR video streams. There’s a how-to here. Problem we’ve got is that the service only appears available to certain DVR types, which we can’t find on sale outside of China. Lead times are in months, not days.
Does anyone have one of these http://www.zysecuritytech.com/page463?product_category=238&brd=1 ? If so, please let us know!
XiongMai & Mirai
Anyone familiar with Mirai will have noticed the connection – ‘XMEye’ – those first two letters stand for XiongMai. If you want proof, check the name of the XMEye service plug-in – ‘web.cab’ from ‘Hangzhou XiongMai Information Technology Company’
Discussion on some CCTV forums suggests that the credentials are local only. We’re not sure that’s the case – why reference the XMEye service in the creds document if the credentials aren’t for that?
We will keep working on this, but whatever the conclusion, sharing super user account credentials with installers and expecting them not to leak is asking for trouble!
I do feel sorry for [email protected] though. Her inbox must have taken a hammering!
Update 10th Jan 2017 – the docs are still there, haven’t been removed yet. The full year’s list of creds are still on LinkedIn too.














