Loose lips sink ships, loose tweets sink fleets. Intelligence, espionage, technological advancements and other learnings from our annual company conference at the historic and underappreciated Latimer House.
“Loose lips [might] sink ships” was a phrase used in UK propaganda posters in WWII. It stressed the need to protect sensitive information and cultivated a culture of silence over military matters. The idea was to reduce the risk of valuable information such as troop movements, ship routes, or other plans falling into the wrong hands.
There’s a great story about two sisters in WWII who joined the Wrens, the women’s branch of the Royal Navy (fully integrated into the Royal Navy in the 1990’s). The Owtram sisters worked separately as codebreakers, and they only found out about each other’s involvement after the war, such was the importance of secrecy.
Decades later, in 2018, the British Navy revisited the saying with “Loose Tweets Sink Fleets”. Technological advancements, social media, and societal and cultural changes present new challenges when it comes to cyber security.
Latimer House
In December we met up at Latimer House for our annual company conference, followed by our end of year social. Latimer House is arguably as important as Bletchley Park for its role in WWII. It hasn’t had enough recognition and I think that needs shouting about.
We learned about the history of the estate, why it was essential to MI5 and MI6, and how it was given an unlimited budget for ‘secret’ purposes by Winston Churchill. We were also shown how the intelligence gleaned at Latimer House and its sister sites contributed towards the intelligence that enabled Britain to win the war.
Subtlety is everything…
Thousands of German prisoners, including many generals, passed through Latimer House between 1942 and 1945. Hitler’s Deputy Rudolf Hess was among them. British Intelligence knew that prisoners’ knowledge would be a great asset, but they needed to be clever about how they got it.
The Generals were treated well during their time at Latimer House. British Intelligence wanted to develop mutual respect and empathy with the prisoners so as to earn their trust. Our guest speaker told us that the generals were often taken on walks around the estate well as field trips to London. At one time, the gardener at Latimer House boasted no fewer than 15 German generals helping him work on the vegetable garden.
It is long acknowledged that the use of torture or extreme duress in interrogations is no good for getting reliable information. Because of that British Intelligence ran bogus soft interrogations to make the prisoners feel as though they had got one over on the interrogators. Later, back in their rooms, they would brag to their fellow prisoners about all the information they had managed to keep secret. What they didn’t know was that those conversations were being listened in on. Hundreds of covert microphones were spread around their living quarters and in the estate.
Secret listeners fluent in German worked around the clock documenting the conversations of over 10,000 prisoners. The prisoners had no idea that they were being overheard and consistently gave up useful information on the German war effort.
Intelligence, espionage, and technological advancements
During our event my colleagues gave talks on a wide range of subjects.
We had a talk from one of our Specialist Engineering Consultants titled “Don’t Call Me a Spy” explaining the differences between some of our more specialised OSINT and Physical Security engagements and actual espionage – spoiler alert, we have never knowingly killed anyone during an engagement!

There was a really cool talk on AI, Automation, and ChatGPT, expertly delivered by our Shelley Booker, along with what turned out to be my favourite topic “Navigating the Spectrum of Intelligence”.
It explained intelligence through the ages and how advancements in technology have contributed towards how intelligence can be gathered, and the inherent cyber security risks associated with that.
Intelligence through the ages and technological advancement
Where there is competition there is always the possibility of an advantage being gained through nefarious means. In the Spectrum of Intelligence talk our speakers went into detail about the world of geopolitics, and covered an early example of eavesdropping: The Thing, an early example of a covert listening device:

Image credit: Daderot, CC0, via Wikimedia Commons
https://commons.wikimedia.org/wiki/File:Great_Seal_bug_-_National_Cryptologic_Museum_-_DSC08048.JPG
It was designed by Russian inventor Leon Theremin (free points if you can guess the musical instrument he invented). This listening device was gifted to the US by the Soviet Union as a gesture of friendship. It was embedded in a carved plaque of the Great Seal of the United States, and was hung in the US Ambassador to the Soviet Union’s residential study for 7 years before being detected.
Maybe the most fascinating thing about this device is how covert it was. It had no electrical components or power supply. Listening required a radio signal of the correct frequency being fired at it from an external location.
Fast forward a few decades to 1985, Dutch computer scientist Wim van Eck published the first unclassified technical analysis of the security risks of emanations from computer monitors.
This attack vector became known as Van Eck phreaking and is still an issue today. An eavesdropper can detect and analyse digital signals using equipment that picks up electromagnetic emissions from a computer screen.
Fast forward to the current day and new eavesdropping technologies present potential new attack vectors. Laser microphone listening devices (some with a range of ~600m) which were once only available to the military are now available for anyone buy.
We decided to do our own research to understand how much one of these would cost, and therefore whether they would be a realistic attack vector. We reached out to one of the organisations who sell the long range ones online for a quote. Even at the “special discounted price” of $40k (no, we didn’t buy it) it would be a useful tool for a motivated malicious threat actor.
Cyber security vs. The laws of physics
What I find fascinating is the link between cyber security and the fundamental laws of physics. I’m no physicist, never studied it past GCSE level, however my natural curiosity in how the world works sometimes gets the better of me and in the case of the electromagnetic spectrum has led me down what turns out to be quite the rabbit hole.
There are people more qualified than me who could go into greater depth on this subject on a technical level, but for those of us with less of a scientific background I’ll explain some of what I believe are the most pertinent points and risks to consider.
Let’s start with some basic physics. By forcing an electron down a wire (i.e. electricity) this will produce frequencies. And here’s the thing – essentially, anything on the EM spectrum including the visible range produces off-products that could be sniffed / intercepted.
The electromagnetic spectrum
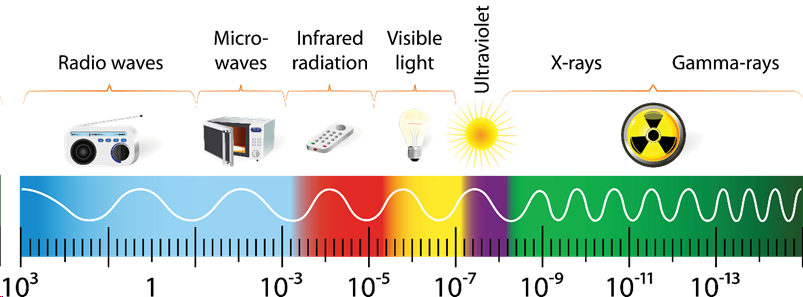
EM disruption is something that we have been trying to mitigate against pretty much since Michael Faraday first discovered the principle of electromagnetic shielding back in 1836. Faraday cages are now used in many industries, such as military, medical, and telecommunications. They continue to be a critical part of our technological advancement, providing protection against harmful electrical fields and ensuring the reliable operation of devices.
Most of us don’t realise just how commonplace Faraday cages are. For example they are used in cars to protect infotainment systems from signal interference, on the Space X launch pad to protect against damage from lighting strikes, and some prisons are designed in a particular way to act as a giant faraday cage. There are positives and negatives of course. A faraday cage bag / pouch could be used by shoplifters to steal goods with RFID tags, or by criminals to smuggle mobile phones:

EM shielding is vital in the automotive world and transport in general because of the many electronic systems they use. As technology evolves and the world gets increasingly more connected, this presents some unique challenges to industry.
RF interference can cause systems to malfunction, disrupting the electronic circuit functions. In the case of a car hurtling down the motorway at 70mph, having technology systems malfunction is clearly problematic. Thankfully properly installed EM shielding helps to protect these systems from interference and is a consideration during vehicle design, engineering, and manufacturing.
How do these risks relate to me?
Again, I feel we need to take a step back and understand the science behind electromagnetism (this time even touching on astrophysics – who do I think I am?!). A solar flare from the sun produces radiation across the magnetic spectrum which can disrupt communications and damage electronic systems here on Earth. This is an example of an electromagnetic pulse (EMP) – a brief burst of electromagnetic energy. The origin of an EMP can be natural or artificial, other examples of a natural EMP is lightning strikes or electro-static discharges.
An artificial example… well, without wanting to catastrophise, a nuclear explosion high in the atmosphere would produce a Pulse which could cause widespread damage to electronical systems across a vast area. MITRE published a fascinating news article on this a few years ago, available here.
But although these risks may affect us, they are all risks which, for the vast majority of us, we can’t feasibly do much about. What about the risks that could affect us that we can mitigate against? The ability to generate EM disruption in a non-nuclear environment is now highly sophisticated, doesn’t cost much, is accessible to many and requires little technical prowess. And it is these manifestations that we should think more carefully about.
DIY
It is worth considering that it is not at all difficult to find the parts needed to build an RF scanner. Given a clear set of instructions (a quick search on Google for ‘DIY RF scanner’ brings up dozens of results) most of us could build our own RF scanner using parts sold in high street electrical stores for ~£100.
Considering how easy it is to source the right parts and build your own scanner, this opens us up to a wider array of possible risks. Everything connected has an RF signature, from an RF profiling perspective you could theoretically scan a building from across the street and identify the technology an organisation is using. Potentially even down to the make and model of each individual part. A person with ill intent could sniff VoIP traffic with a scanner, and if they could decrypt it, Bingo! They’ve got access to potentially sensitive information.
Mitigation
Those of you in cyber security will be familiar with risk measurement. For high-risk environments where there are concerns about the likelihood and impact of an attack, EM / RF assurance should be explored.
In the UK, HM Government, their customers, and CNI entities can work with the NCSC to understand and manage the level of signals emanating from IT equipment, which may be at risk of unintentionally emitting sensitive data.
For organisations looking to protect classified data NCSC provide TEMPEST consultancy and testing via approved vendors, along with certification schemes used to assess certifying products and mobile platforms.
TEMPEST and EMS services help ensure that appropriate countermeasures are in place to mitigate against this level of risk. This gives end users confidence that the products meet the UK National TEMPEST requirements.
Non-classified but still concerned about EM / RF risks?
For those of you that don’t necessarily handle classified data, or for those that have other concerns such as protecting your intellectual property from competitors or journalists for example, there are still some lighter touch EM / RF assurance activities you could consider.
Some possible attack vectors and how you could remediate against them:
- Is your shielded room really shielded? – Scan wall to wall to see if there is any RF leakage.
- Is there a chance you are being watched / listened to? – Conduct a bug sweep of a room to look for hidden cameras or listening devices.
- Require further assurance? – You could consider creating a “clean room” procedure mandating a checklist of items to be reviewed and confirmed against a known safe state which can be inspected visually prior to a meeting (for example) to ensure no tampering or adjustments have been made.
- Is my Wi-Fi coverage appropriate? – Review how wide the range is on your Wi-Fi access points and manage/reduce power as appropriate to minimise signal leakage outside the building.
- Is my supply chain secure? – RF scanning of hardware to investigate whether the device is omitting any rogue frequencies. Could be done as part of logistics – scan before the hardware leaves manufacturing then another scan when it arrives at destination to make sure the RF output matches as expected for example.
- Concerned about data in transit? – Make sure you have strong encryption in place across any sensitive communication channels.
- Still concerned? – collaborate with industry / NCSC.
Conclusion
For non-classified organisations, what are the practical realities? Is it possible that you could be targeted by via EM / RF attack vectors? Maybe, however you can have a degree of confidence that this is less likely to happen and will be less damaging if it does (in comparison to higher risk environments at least – everything is relative!).
There are lessons to learn though. You would probably be better off spending time addressing OSINT leakages (remember, Loose tweets sink fleets!) and remotely exploitable issues.
Understanding the level of risk that must be considered and mitigated against in high-risk environments can help contextualise your own understanding of the risk. If you understand your attack surface and are aware of the risks pertinent to you and your organisation this will put you in a much better place to secure your environment to a suitable level.
There are loads of resources available to help you with this, such as ISO27001, NIST and Cyber Essentials which you could consider.














