What do we mean by OT networks? You may also come across terms such as ICS (Industrial Control Systems) and SCADA (Supervisory Control and Data Acquisition) but generally we mean the serial data networks and devices that control machinery.
Examples of OT include propulsion control, steering, ballasting and many others. You are probably more familiar with an ethernet or IP network from your home or work computer; you’ll be familiar with the network cable that plugs in to your home router with a small clip. It’s called an RJ45 connector.

Serial networks operate differently; they are much more popular in industrial systems such as utilities and vessels where safety and reliability is paramount, however their cyber security is often non-existent or very weak. You may be familiar with 9 PIN serial cable connectors like this:

There’s a reason that their security isn’t great – for many years OT networks were completely isolated from the internet and from corporate networks. The threat vector was primarily from physical attack, so they were kept behind lock and key in, for example, electricity substations and water pumping stations.
Utilities faced a barrage of OT hacking incidents as systems were accidentally (or thoughtlessly) connected to the internet in the 2000’s. This culminated in the Stuxnet incident in 2009 and 2010; an attack by nation states against the Iranian uranium enrichment programme that got out of hand. Lift systems in Germany were affected, production lines in the USA were compromised, all users of similar OT to the Iranians. Those familiar with the ‘notPetya’ incident at Maersk will note similarities here, though that was an IT attack, not OT.
OT on vessels
Direct control from the bridge of, for example, the ships engine occurs by the engine levers sending network data over the OT network to the engine control systems in the engine control room.
There are numerous potential security flaws in the OT network that a hacker could exploit. First, we will look at the cabling
Serial network cabling isn’t often the best way to send OT data around a vessel. An IP network will usually be in place throughout, so serial to IP convertors are used to ‘encapsulate’ the serial OT control data and transport it to the control systems over the IP network.

The convertor receives serial data at one side, then sends it out over an IP network from the other side. A second convertor at the outstation (e.g. the engine control room) converts the data back to serial again.
Security of the convertors is very important:
The convertor must be ‘hardened’ against security attacks. This means ensuring that the administration passwords are not left default by the installer. Default passwords are VERY common
Default convertor passwords
Serial to IP convertors usually have a web interface for configuration. The default credentials are usually admin/superuser, superusr/<blank> or admin/<blank> in the case of Perle and usually admin/moxa, admin/admin or admin/<blank> in the case of Moxa convertors. These are published by the manufacturers on their own web sites
Once the hacker has the password, they can administrate the convertor. That means complete compromise and control of the serial data it is sending to the ships engine, steering gear, ballast pumps or whatever.
Exploitable convertors
There’s an interesting security flaw in some convertor firmware. An exploit is available in the Metasploit security exploit framework that is popular with hackers. One example vulnerability is referenced as CVE-2016-9361 and allows the hacker to recover the admin password, even if it has been changed from the default. This vulnerability has been fixed, but the software needs to be updated to apply the patch
Encrypting convertor communications
Many newer serial to IP convertors support SSH or similar traffic encryption, making man in the middle and similar hacking attacks much more difficult. Convertors should have encryption enabled. If they do not support encryption, check for software updates that do, or replace the convertors with more up to date models that support encryption.
Understanding NMEA0183
Almost all OT networks on board communicate using a protocol known as NMEA0183. This protocol offers no encryption or message authentication. The only validation that the message is correct is a 2-byte XOR checksum that is simply present to ensure the message was electrically correctly received.
A NMEA 0183 message might look like this:
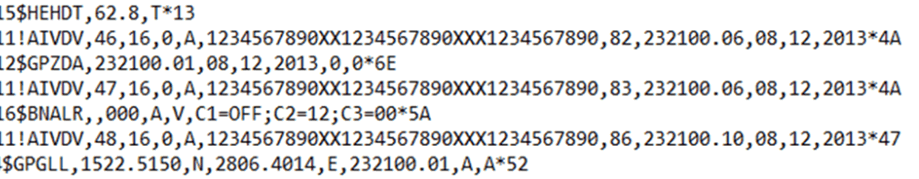
Where the 5-letter code beginning ‘$’ dictates what type of message it is, with the variables after passing useful information.
The example above was taken from a remote data storage module for a voyage data recorder. It shows GPS heading and location data plus AIS information.
Systems that use NMEA0183 include:
- Steering
- Propulsion
- Dynamic positioning
- Ballasting
- GPS
- AIS
- Navtex
- BNWAS
And many others
Clearly the security of the serial network and the NMEA 0183 messages is critical to the safety of the vessel
An example attack against NMEA 0183 data on a vessel OT network
If the hacker has established remote access to the vessel (perhaps through satcoms, creating a back door through a phishing attack or a physical network implant) the next step might be to tamper with the GPS data stream on the vessel network.
An ‘ARP poisoning’ attack involves the hacker instructing the various systems on the network to send their data to via them. The hacker effectively inserts themselves in to the data stream in what is known as a ‘man in the middle’ attack. By adjusting the GPS position reports from the GPS receiver in the NMEA 0183 data stream, the systems can be fooled.
Unlike GPS jamming or spoofing attacks, where no position data or gross position errors are received, this type of hack is much more insidious: the change in position is gradual and far harder to detect.
If the ECDIS is in track control mode whereby it directs the autopilot, the hacker can fool it through GPS data tampering and cause the ship to change direction.
Ships masters may counter that they would cross reference the ECDIS position with ARPA in the event of position uncertainty, though it is perfectly possible to insert identical position errors in to synthetic radar, removing the ability to verify by cross checking.
If the crew are alert, then they should pick it up and take control, but they are being presented with exactly the same tampered position data as the automated systems, so crew would need to be very alert indeed.
ECDIS security
An ECDIS is usually just a desktop computer. It may have a rugged case, screen and keyboard, but it is fundamentally just a PC.
Just like any computer, it requires updates to be applied, both to the underlying operating system, to its ECDIS software and to the digital charts. If any of those are omitted for any period of time, cyber security vulnerabilities creep in.
ECDIS are increasingly being connected to vessel networks to facilitate online chart updates, integration with other bridge systems and remote maintenance. Security flaws that did not matter so much in the past through a lack of connectivity are now becoming very important.
Even having dual redundant ECDIS on the bridge is no guarantee of availability: during research we discovered similar security flaws on multiple ECDIS brands. A hacker would have little difficulty in compromising both.
ECDIS USB security
The ECDIS system case must be kept in a robust locked cabinet to which only senior personnel have access. It should not be possible for other personnel to access the system case or any of the USB and network ports on it.
A source of several ECDIS security incidents has been from crew charging smartphones from the USB ports. Phones that have not been kept up to date may already be infected with malware.
Many ECDIS have USB ports present on their keyboards, as shown in the example below. Operators frequently report that, despite multiple ‘safe’ USB charging points being made available on the bridge, crew still charge phones from the ECDIS.

With this in mind, seriously consider installing USB port blockers such as the below. Whilst they are not difficult to remove, they do provide a visual deterrent to casual charging.

If the crew persist in charging from ECDIS USB, you may consider gluing the blocker in to the USB port. Bear in mind that chart updates can still be applied by opening the ECDIS cabinet and inserting clean USB keys directly in to the system case USB ports.
System updates and hardening
It is imperative that the ECDIS computer is subject to regular updates to its operating system. During vessel security audits, we have discovered ECDIS still running Windows NT, an operating system so old that Microsoft stopped supporting it in 2004! That means that any new security flaws in the software will NEVER be fixed.
Windows XP and Windows 7 are also commonly found on bridge systems. Even as recently as April 2018, Microsoft released 22 vulnerabilities rated ‘critical’. These updates must be applied, as hackers will quickly ‘reverse engineer’ the updates and work out how to exploit the security flaw.
Not all ECDIS are based on Microsoft operating systems. A smaller subset of vendors use Linux based operating systems, which require updating in just the same way.
Whilst downloading updates at sea over satellite can be expensive, the operator should determine how critical a new patch is to their systems. Truly urgent patches, such as the ‘Heartbleed’ flaw from 2014 would merit the expense of patching whilst at sea, though most could likely wait until the next port of call and updating over shore Wi-Fi.
All computers should be subject to ‘hardening’ during installation. This describes the process whereby it is configured to be as secure as possible; it should deliver minimum functionality in order to deliver its role as an ECDIS. For example, one would not expect Microsoft games to be present on an ECDIS, nor would one expect administrator passwords to be blank or simple
The Center for Internet Security publishes free CIS Benchmarks which offer good practice guides and checklists for hardening systems. Their web site is at www.cisecurity.org.













