For a pen tester, the port scanning tool Nmap is used almost on a daily basis, however it can be rather handy for IT managers and system administrators who want to identify common “security gotchas” on their network. Let’s start with the Simple Network Management Protocol, more commonly known as SNMP, or to a select few “Security Not My Problem”.
This is a monitoring protocol often found running by default on printers, servers, routers and various network appliances. If incorrectly configured at best it can divulge various system and network information, at worst used as a mechanism to change system settings, or even pull back sensitive configuration files.
The Nmap Scripting Engine (NSE) is a way for users to extend the functionality of Nmap by writing scripts to automate a number of tasks, including finding vulnerabilities as we’ll dig into now.
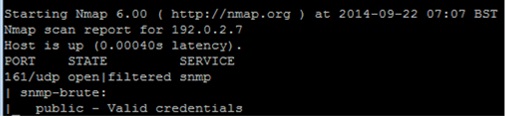
Say you want to scan across a network looking for devices that were set with trivial community string values such as public or private then you could use the NSE “snmp-brute” script as shown in the following example:
If a device was identified with a trivial value, then you’d receive output similar to the following:
When performing an internal pentest on Windows, one of the first things I’ll try is scanning across the systems looking for weak local administrator credentials.
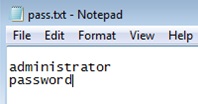
Let’s first create a small word dictionary (you can use notepad or your chosen text editor of choice to create a textfile):
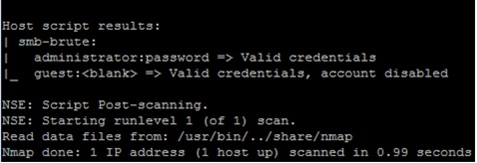
Let’s run Nmap, targeting specific Windows ports and passing it the “pass.txt” file that we created above:
If a server had the password of “password” set for the local Windows administrator, you’ll see output similar to the following:
With this rather handy technique you could adjust the command to look for old weak Administrator passwords that should no longer be in use, or check other types of credentials that you don’t want on your network.
The final feature I’m going to talk about today is operating system (OS) detection. This clever technique can be useful to identify outdated operating systems (such as Windows XP, Windows 2000…..), systems hidden away in your server room that you didn’t know you had and also devices introduced into the network without permission.
Below is an example of running Nmap with the OS detection feature turned on:
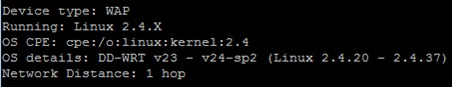
Nmap will try its best to fingerprint all devices it finds, and from this group them into device type. This can be particularly useful if for example you’re wanting to identify wireless access points (WAP) that may be on the network unauthorised:
To try out Nmap yourself, you can download it for Windows from here:
http://nmap.org/download.html
Alternatively, if you have a spare Linux server and are comfortable in that environment, most package managers allow you to install Nmap easily (e.g. apt-get install nmap).
Lots more documentation can be found here:
http://nmap.org/book/man.html
A word of warning, Nmap can be a very powerful and useful tool, though please ensure that you seek proper authorisation before trying it out on your own network. The tool can generate a significant amount of network traffic. While most newer platforms handle this fine, some devices running older operating systems or firmware can have stability issues.
Happy Nmapping!