Continuing my series on OSINT techniques you can use for reviewing your own corporate OpSec, one of the most common services available in a modern corporate office is of course wireless. How do we go about finding wireless access points and what can they tell us?
Finding wireless
We have spoken about Wigle.net many times before, its awesome and allows you to hunt for access points by name and location, which is really useful for us when performing OSINT.
Through analysis of the corporate website we can usually identify any office addresses. From that address we can search with Wigle.net.
Choosing a random location in London for the purposes of this post, let’s say we identify that our target’s office is on Belvedere Road in London.
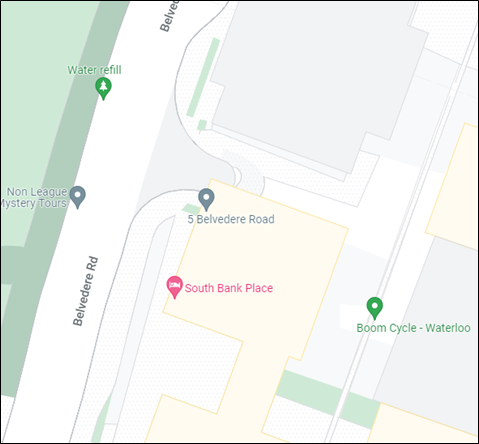
Using the address (or for more accuracy the GPS position) we can use Wigle to find all of the wireless access points in that area.
Finding technology
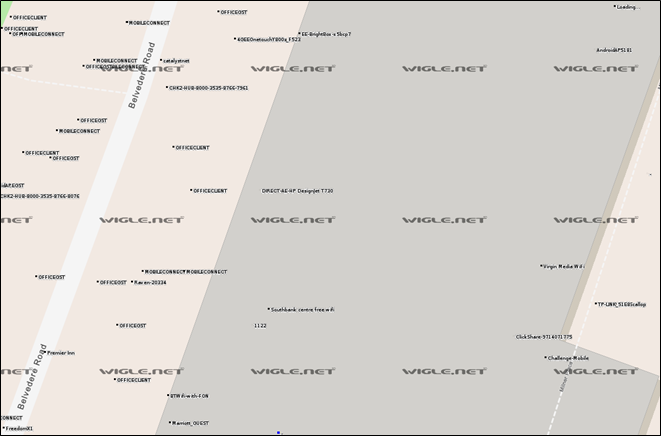
Due to the nature of wireless the detected devices are likely spread out over a fairly large area. When contributors collect wireless access point names the device they use will typically use its own GPS position when it detects it and so you may find some APs outside your target building that could still belong to your target. However, as more people find the APs Wigle will triangulate the AP and the location should become more accurate.
Looking in the results on Wigle we can see some really interesting access points:
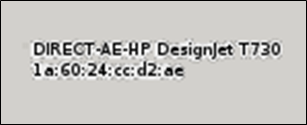
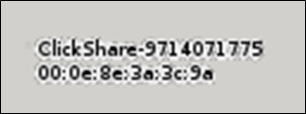
Suggesting the target make use of HP DesignJet printers, the T730 is a large-scale printer and scanner. Clickshare is commonly used to facilitate easy screensharing when meeting.
Depending on how these are configured they could offer a way into the internal network, commonly Clickshare is incorrectly configured and acts as a network bridge between networks. However, that’s for another time.
Finding corporate networks
If we look closer we can see a number of other networks that could potentially be used by staff to access network resources

This suggests mobile phones may be protected with MobileIron and that staff wireless is available on OFFICECLIENT.
As with most OSINT, this may not be the case, but it provides a potential avenue for further investigation. Using other office locations, we may be able to provide some correlation of names, giving us a stronger degree of confidence.
Conclusion
Wireless access point names are by no means the most revealing of information, however, depending on the office location and the APs found it could be useful supplementary information to an attacker. This could be useful in planning a targeted social engineering attack.
Additionally, imagine your APs are found on Wigle within your corporate office. However, alongside that, Wigle list a non-standard AP within your building. Could that be a rogue AP? Could attackers exploit that to gain access to your internal network?
Given the lower threat from this information, remediation my be of limited value when considering the effort, however, if you wish you can contact Wigle and they will remove your device from the service. Preventing broadcasting of your SSIDs’ outside of your office is a challenge, but maybe a sensible option if you can.