I gave a talk in Athens recently to a number of shipping lines about infosec. One thing that struck me were the similarities between the challenges maritime cyber is facing now and the challenges industrial controls security in utilities started addressing several years ago.
Back in the day, ICS ran on dedicated, isolated networks. Network protocols were custom and arcane, security was non-existent in these safety critical systems. But it didn’t really matter that much, so long as physical security of the endpoints and comms was good. The threat vector and attacks seen were mostly grumpy, knowledgeable ICS/SCADA engineers.
Now ships: complex industrial controls, but floating. Traditionally isolated, now always-on, connected through VSAT, GSM/LTE and even Wi-Fi. Crew internet access, mashed up with electronic navigation systems, ECDIS, propulsion, load management and numerous other complex, custom systems. A recipe for disaster.
Yet there still seems to be an attitude of ‘it won’t happen to me’. So I took my talk down the route of exploiting satcom terminals and OSINT; to make it as real as possible by showing real ships and real people in real time.
As some of the pen test team here used to work on board container ships, we have a fascinating knowledge of ship systems security.
Let’s start with our friend Shodan:
Big brands in the maritime satcoms space include Inmarsat, Telenor and Cobham. Let’s see what we can find on www.shodan.io.
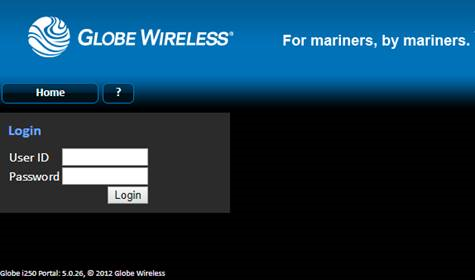
Inmarsat is a bit easy, so a search for ‘org:”Inmarsat Solutions US”’. You’ll see plenty of logins for Globe Wireless over plain text HTTP, also an earlier branding as ‘Rydex’. Globe were bought out and rebranded as Inmarsat in 2013, so you can date the comm box by the brand alone. Most of these are very old, undoubtedly running dated firmware.
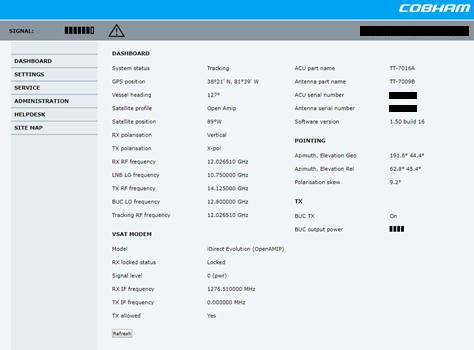
The Cobham ‘Sailor 900’ system is a bit more interesting from an information disclosure perspective:
Search ‘title:”sailor 900″’ and you’ll get the satellite antenna detail unauthenticated, e.g.
Now, in the absence of known exploits such as this one for the Sailor 900, to make changes or do malicious things, one needs to authenticate as an admin user. The default is admin/1234. I haven’t and won’t be checking these creds on someone else’s terminal, but what chance someone forgot to change these during installation?
Most of the maritime ‘hacking’ incidents reported in the press of late appear to me to be simple default/missing creds from comms terminals, then the ‘hacker’ clicking around a control system GUI. That doesn’t really count as a hack to my mind, though the consequence is the same.
Anyway, back to the talk and more searching Shodan:
Search for ‘html:commbox’ and you’ll see a nice collection of KVH CommBox terminals. This is where things got a bit silly.
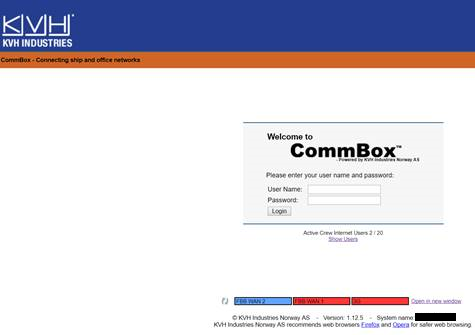
Yes, missing TLS on the login again. But it gets worse. Look bottom right, you’ll see the vessel name – I’ve redacted it in black in this case.
Below the login is the following:
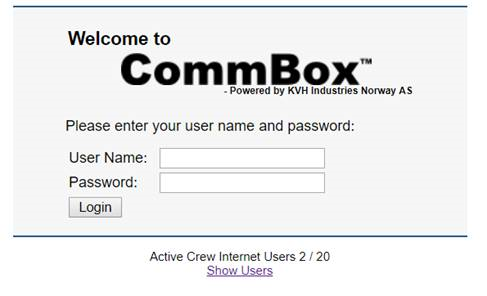
‘Show Users’ – WTF??
You can request the content by appending /rest.php?action=QCgetActiveUsers – or just click the link ?
From which comes a list of all the crew online at that point.
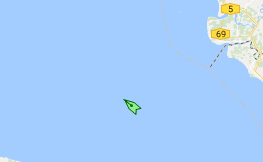
Here’s the ship.

Here’s where it was today, from AIS: In the Malacca Strait, heading for Tubarao in Brazil.
A moment on Google and we had the Facebook profile of the deck cadet who we had spotted using the commbox:
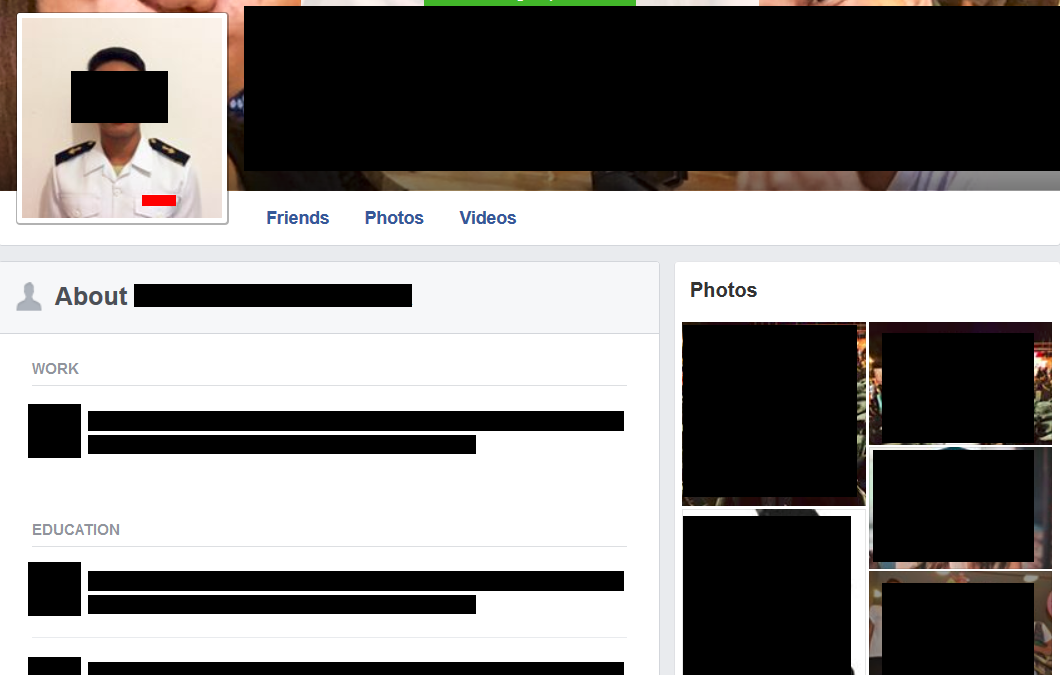
This poor chap is ripe for phishing – we know pretty much everything about him.
Simple phish, take control of his laptop, look for a lack of segregation on the ship network and migrate on to other more interesting devices.
Or simply scrape his creds to the commbox and take control that way.
It shouldn’t be this easy!
Oh, and here’s some of the network config, simply by hovering over the GUI
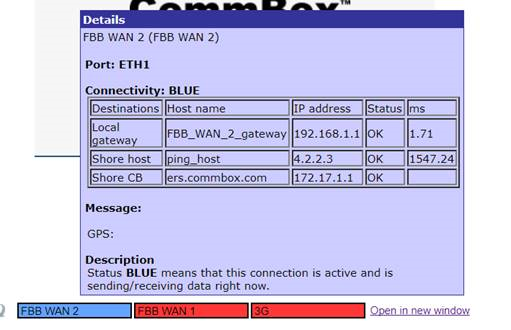
Addressing this
Let’s start with basics.
TLS needs to be in place on satcom boxes. How can this be still missing on live devices today?
Password complexity is a must, particularly for high privilege accounts.
These boxes must be updated as a matter of urgency. It’s simply not acceptable to leave vanilla firmware in place.
There are many routes on to a ship, but the satcom box is the one route that is nearly always on the internet. Start with securing these devices, then move on to securing other ship systems. That’s a whole different story.