There is much talk about supply chain security and reviewing your suppliers for cyber security. But how much information do they intentionally and unintentionally leak about your organisation online?
We see this particularly in the industrial controls sector as its cyber security maturity is perhaps a few years behind the wider cyber market.
Fortunately, this is something that you can audit yourselves, without needing to involve the supplier. It can make for useful negotiation points during procurement exercises, particularly if you engage your purchasing teams in the process.
Why make the hackers life easy?
New sales contracts
Technology suppliers like to make a song and dance about new contracts that they’ve won. Having public references can make the sales process easier. I would argue that it should make the sales process harder, as I would be quite upset if a supplier published a list of technology that they had sold to me!
Spend a few minutes online and take a look at some of the press releases said supplier has put out. Do they name clients, do they name technologies? Do they name the technology that they are replacing or upgrading?
It’s easy to find press releases from your suppliers that mention your brand. Google searches include:
- Site:<supplierwebsite> “your brand name”
- “supplier name” “your brand name”
A search of one OT supplier recently revealed a highly detailed solution outline that could trivially be used in a supply chain attack. Attack the supplier, obtain the reports, then target the sites with the security vulnerabilities included in the reports.

Press releases and news are one thing, but I would also include LinkedIn in your search. Overly keen sales people often publish their big wins without following corporate guidelines. Sometimes it’s simply a ‘thanks’ message that includes the name of a key person at the buying organisation allowing attackers to work out who the right target is.
You can find other posts easily by searching your company and viewing posts.
Legacy security
Should it really matter if suppliers name the new kit they are putting in? Arguably it shouldn’t and your security controls should not be ruined simply by a third party knowing what systems you have. But it doesn’t always work like that. Supply chain attacks are a very real thing and knowing who your suppliers are is crucial to many targeted attacks.
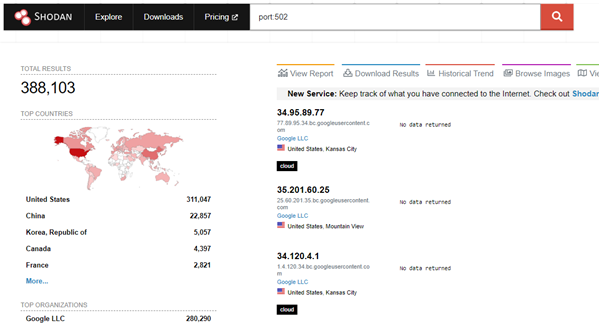
However, knowing what kit you have is another, especially is it’s old, and vulnerable. It’s even worse when it’s on the internet. So, search your IP space for OT kit. This is trivial with Shodan. Shodan have detailed documentation on how to find kit:
https://www.shodan.io/explore/category/industrial-control-systems
You need to adjust the search terms for your IP range and specific kit.
A search for the Modbus port 502 has loads of devices, some possibly not related to Modbus:
https://www.shodan.io/search?query=port%3A502
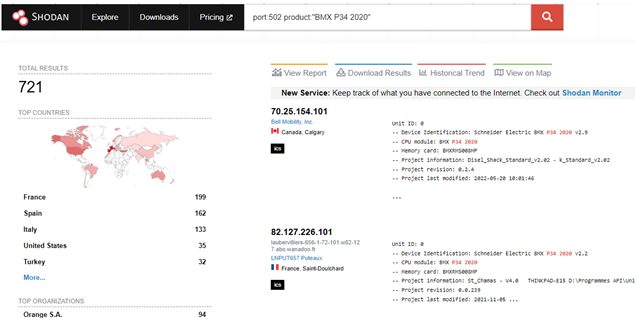
The search can be filtered by product, lets say you want to search for BMX P34 devices you can easily do this:
https://www.shodan.io/search?query=port%3A502+product%3A%22BMX+P34+2020%22
However, this may still not be relevant to your IP range, so we can tweak our search range to include only our IP range, using the Net parameter:
port:502 product:”BMX P34 2020″ net:<range>
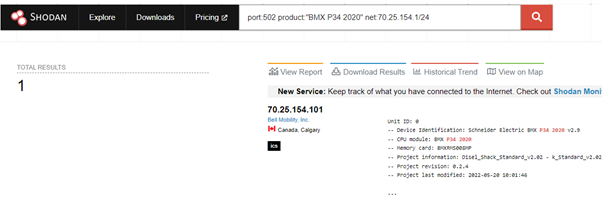
With some services you can view versions, which can allow you to easily see which services are vulnerable
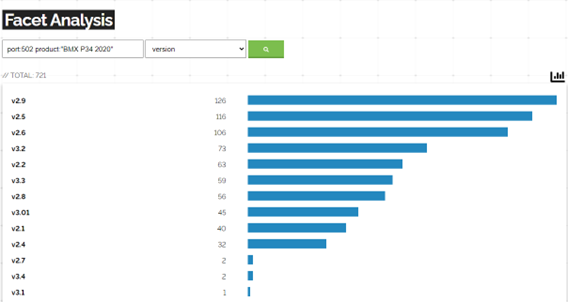
Which can then be searched on OpenCVE for vulnerabilities.
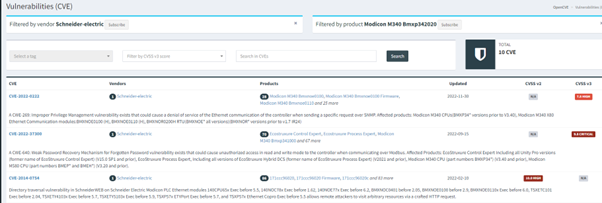
There is plenty more you can do on Shodan and finding OT is well documented already.
What else can you do on LinkedIn?
Some interesting ideas include following pre-sales engineers, your staff, your ex-staff. Each have their own benefits. Pre-sales engineers will often talk about meetings they have had and will commonly celebrate wins publicly, allowing attackers to link companies to products. Your staff and ex-staff will often list skills and job description, this can be quite revealing…
Public tender info
Outside of LinkedIn, many organisations, especially public organisations will list tenders publicly, this will allow attackers to see who is purchasing and who is winning bids. There are a couple of useful places:
https://bidstats.uk/
https://www.tendersinfo.com/
Bidstats is UK only, but tendersinfo.com is worldwide.
Photos
Finally, make sure that photos of critical safety and control systems don’t end up publicly accessible
We can’t keep smartphones out of control environments, but we can remind our workforce not to take photos.
The accidental and unintentional disclosure is often the most concerning – a selfie at a desk with a safety critical HMI in the background? It shouldn’t matter that the password was stuck to it with a Post-It; controls shouldn’t be that weak that it matters, but why make it easy?
Remember Stuxnet? A press photo of a tour of a nuclear facility by the Iranian president was thought to have revealed the cascade structure sequence of the uranium enrichment system controllers at the Natanz nuclear plant. That helped inform the Stuxnet authors.

Non-technical recon
It’s amazing what you can hear in the pub: large users of OT often have thousands of operatives, like many colleagues, they often socialise together, they typically live near the plant and so you can usually find them in the local chatting shop. A well-placed seat in a bar can often reveal many corporate secrets. This is not isolated just to OT, this applies with many industries, it’s just with OT, its often easy to pick the right pub, the local near your plant may well be the place your staff go to let off steam and discuss work.
What can you do?
Start with procurement. Check that your contracts have explicit clauses preventing suppliers from promoting their new client sales wins. Publication of a sales win is often used as a price negotiation tactic, but procurement teams may not understand the risk of a public disclosure. Help them understand.
Talk to HR. Do staff contracts cover non-disclosure of technologies? They probably do, but staff training & induction also needs to remind people of this. Simply explain why.
Do staff members understand the risks of disclosing technologies in use, particularly around job history on LinkedIn? People will naturally want to demonstrate expertise in certain systems to future employers, but the level of detail disclosed on public social media by some engineers is far too great.
OSINT your company, your suppliers, your networks, consider carrying out an Attack Surface Assessment.