Why do we need strong passwords?
Passwords are stored by using a one-way hashing algorithm to generate a representation of the original password on a securely designed system. Authentication mechanisms then compare the calculated hash of an entered password with the stored hash value to determine if the password is correct.
Because these hashing algorithms are not reversible, the only way to crack a password is to guess passwords and see if there is a hash match. It is therefore important to make the password resistant to cracking so that if a hashed password is compromised, either by gaining access to the database or capturing it from the network, the original password cannot be retrieved easily and used by an attacker. The way to do that is by using strong passwords.
What is a crackable password?
We have multiple dedicated password cracking servers, and we are cracking passwords 24/7 for our clients. The performance is phenomenal – we can try over 100 billion passwords every second for NTLM hashes, and we spend days trying to crack each hash. We try more than 17 quadrillion passwords for each hash that we receive.
With that performance in mind, brute forcing any 8-character password is trivial for typical hashing algorithms and we currently brute-force all but the most complex 9-character passwords. 10 characters represents a significant improvement over 9 characters, but these too will start to become vulnerable to cracking as commercially available processing power improves over the next few years.
The length of the password is not the only measure of strength. Passwords which are based on dictionary words, and even up to three dictionary words, are also not resistant to cracking.
Most university-educated people know around 20,000 words. Our cracking servers use a dictionary of 80,000 words and generates combinations of up to three words easily. So simply choosing three random words without any additional complexity is also not strong enough to be resistant to cracking.
Users tend to choose passwords based on various patterns, and over the years, attackers have built up dictionaries based on these patterns. Here are some that we check for:
- Character substitutions such as swapping an ‘e’ for a ‘3’ or an ‘a’ for a ‘@’ or ‘4’.
- Appending digits, symbols, and dates at the end of passwords, with ‘1’ and exclamation mark commonly used.
- Common phrases, famous quotes, towns, and sport teams.
- A huge number of keyboard patterns such as “1qaz2wsx3edc” as well as common shift key combinations.
The strength of a password is a combination of its length, character set, whether dictionary words or phrases are used, and other patterns which reduce the overall entropy of the password.
What do we recommend is a strong password?
Password managers should be used to store almost all passwords.
It’s the first recommendation because these allow using long and randomly-generated passwords that do not need to be memorised. There are cases where a password manager cannot be used such as the login password to the computer, and the password to the password manager. Every other password should be stored in a password manager.
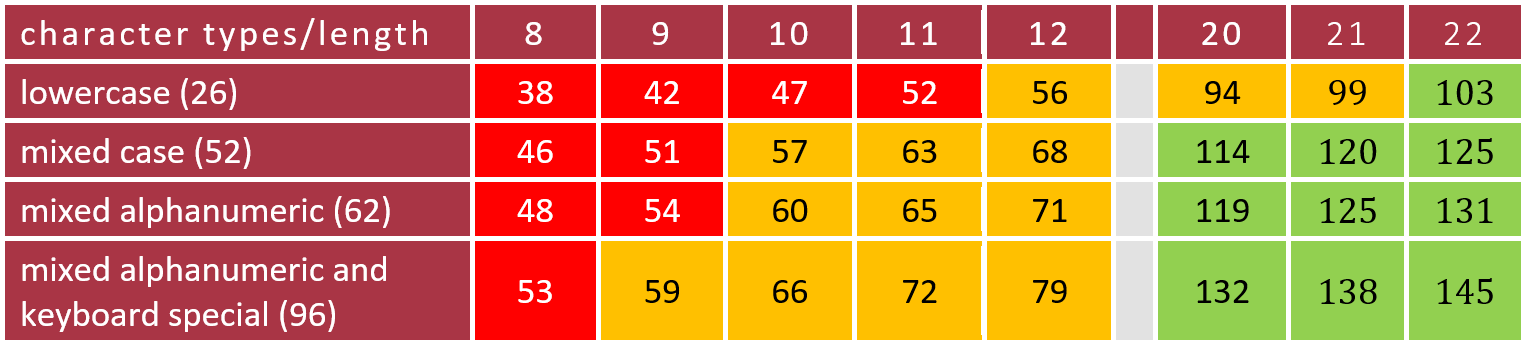
If the password uses a mix of character types (alphanumeric and special characters) and are at least 20 characters in length, that should provide over 128 bits of entropy (a measure of complexity) which would make it very expensive and time-consuming to crack.
In order achieve higher levels of entropy, it is possible to use a combination of length and complexity as shown below:
Entropy (in bits) for various password lengths and character types, a higher number is preferred. Red is crackable, yellow is not considered cryptographically secure, and green is pretty much uncrackable:
One of the issues with mandated password strategies is that if the strategy becomes known to an attacker, they could then solely focus on cracking passwords in that format. Knowledge of the format of the password often reduces the time required to crack it.
With that in mind, users should be free to choose their own strategies, however, the following example strategies could be provided as an aid with the understanding that they could be cracked by a determined attacker with enough compute resource:
Three random words, but with added complexity. Adding characters between the words, prepending or appending extra characters, and using words in multiple languages makes cracking three random word passwords a lot more time consuming.
Four random words, or the correct horse battery staple technique.
The security of this technique depends heavily on the commonality of the words chosen. The more common the word, the smaller the dictionary required, and this reduces the time taken to crack the combination.
If multiple users employed this strategy, an attacker may be tempted to use smaller dictionaries of more common words in an attempt to crack any single user. Even the most common 2000 words could be used and is likely to crack many four-word combinations in just a few minutes if no complexity was added. Using words which are less common or replacing a word with a 6-digit number also adds to the complexity.
10 random characters. This is probably the most secure of the options here, but also the most difficult to remember. Brute forcing 10 characters of multiple character types is just outside of our cracking capability for the time being.
First characters of a sentence. The idea is that a user would think of a sentence that would not be commonly used, so no phrases or quote, and then use the first character from each word. The problem is that the character set is reduced and adding in extra complexity, makes it difficult to remember.
The Link method. There are other strategies for remembering passwords, called the link, or story, method, but these techniques take a bit of practice to learn, so it’s not easy advice to give to everyone on a large domain. They could be suitable for some of people though, and it’s possible to generate passwords that would be very strong.
The paper method. We’ve become really good at securing bits of paper in our wallets and purses, so is there anything wrong with writing down a strong randomly generated password? As long as the password isn’t hidden under the keyboard or stuck to the monitor, using a password book that’s securely stored could be ideal for people that have trouble remembering passwords. Over time, they’ll probably start to remember it anyway and the book will become a backup that’s rarely accessed.
What should the password policy be?
For low privileged accounts 10-characters should be set as a minimum, but be prepared to increase that as the performance of password cracking improves or if regulation requires it.
Cyber Essentials requires the use of 12 characters if automatic blocking of common passwords is not in place. For privileged accounts such as domain administrators, there should be no need to remember these passwords, so the rules for passwords in password managers should apply – at least 20 characters, randomly generated from a mix of character types.
Creating a policy for Domain Admins in the Active Directory Administrative Center:
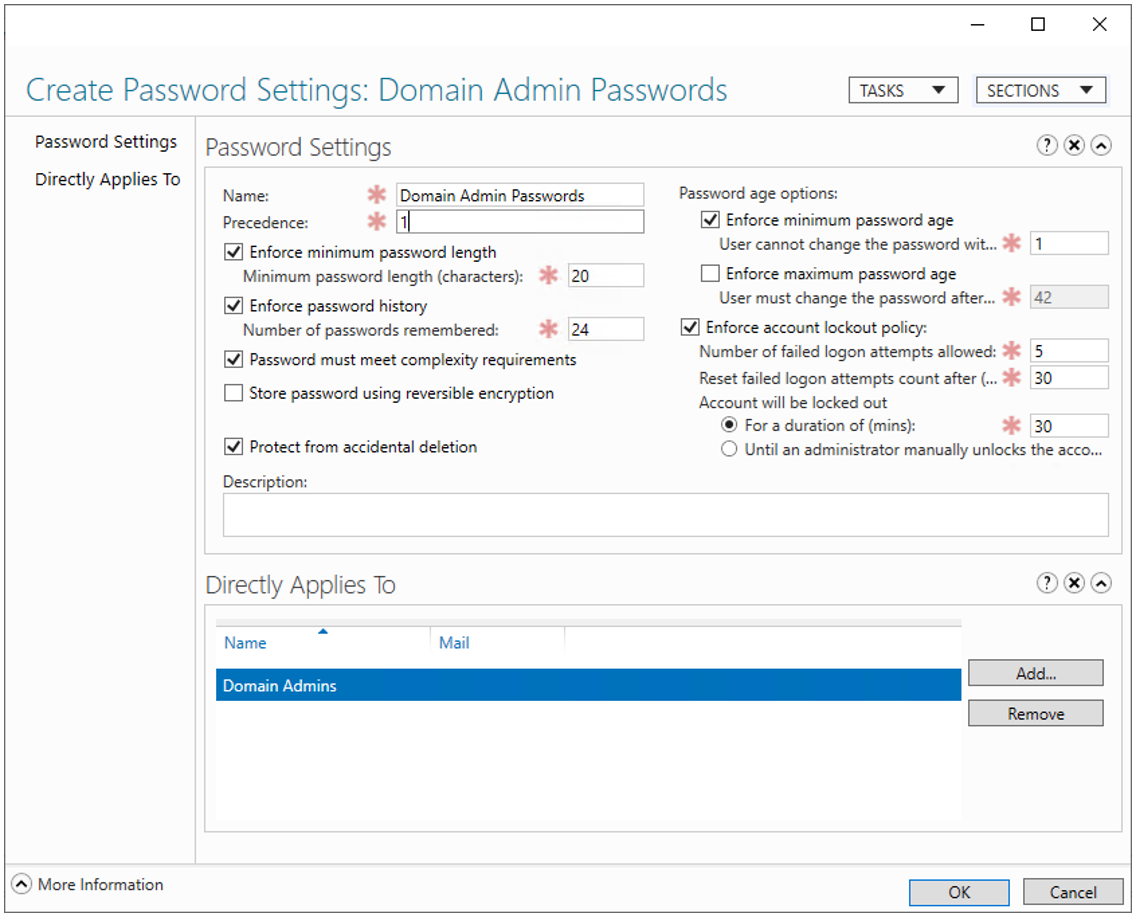
Complexity rules should be enforced if the minimum password length is set to 10 characters. It may be possible to remove some complexity requirements if the minimum length is increased which maintains a high level of entropy.
It is also important, where possible, to ensure that cryptographically secure hashing algorithms are in use. Lan Manager, MD5, and SHA1 are all now considered legacy algorithms and should not be used.
As well as setting a strong password policy, it is also important to consider account policies. NCSC currently recommends that accounts should not expire because users tend to pick weaker subsequent passwords, and often base the password on the previous one.
On the other hand, if accounts are compromised, expiring accounts can reduce the window of opportunity for an attacker. We recommend that a long (6 months or above) to never expiry be set where the passwords can be regularly audited in terms of both strength and publicly available password breaches.
Additional Security
There is always a chance that even the most random password will be cracked, therefore a defence in depth approach is to have multi-factor authentication wherever possible. This lies within the “something you have and something you know” mantra, meaning even if a password is cracked, an attacker would still require something else to gain access to the environment.
Commonly the second factor is a code on an authenticator app, but increasingly biometrics is playing a role. I often have to pick up my phone to authenticate with a finance application through Face ID after purchasing something on my laptop.
Conclusion
To summarise, we recommends various strategies to ensure that passwords meet a level of complexity depending on the access of the account in question. The use of password managers is ideal, and if a password manager cannot be used, then length, complexity, and strategy for content is key.