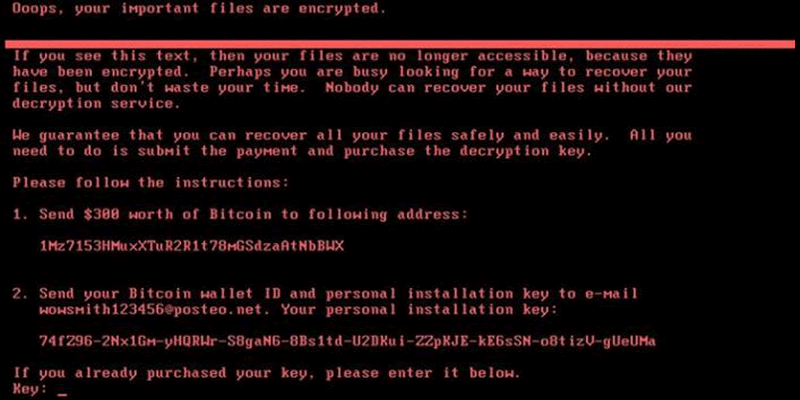
The recent NotPetya ransomware outbreak has caught people napping, again. Lately, malware is being written that uses a lot of automated techniques that we pen testers have employed manually in the past. The vulnerabilities they exploit are not new, and nor are the vectors. The main difference lies in the automation and (obviously) propagation.
With this outbreak NotPetya is using a host of different techniques, not just one, meaning that it is more efficient than those that have gone before. It does appear to be linked to a popular Ukranian accounts package; a rogue update was pushed to users.
Analysis of its behaviour is moving fast, so keep an eye on the following blogs and twitter accounts for real time updates:
…though there are plenty of other good sources.
Attribution
…is difficult, but it’s not well written as ransomware – the email address involved was clearly going to be blocked quickly, preventing decryption payments.
That makes many think that it is purely for disruption. Perhaps it was intended to damage Ukrainian government and businesses, but propagated more effectively than it was intended to?
This is similar to Stuxnet in that it was intended to attack just Iranian nuclear centrifuges, but was uncovered when infections started hitting industrial control systems elsewhere in the world.
Advice
Other sources have good real time advice around NotPetya. This is moving fast, including the ‘kill switch’ of a sort that can be added locally to prevent encryption. This is unrelated to the Wannacry kill switch, which was completely different.
Patch MS17-010 and MS17-012 if you haven’t already
Disable the ability to execute unsigned macros in Office documents using group policy settings, and sign legitimate macros from your own organisation, details here.
Ensure that you’re patched against CVE-2017-0199
Stop using common local credentials across multiple systems
Backup
Backup
Backup
…and after it’s settled down, get someone to red team on your network and show you how similar techniques can be used to escalate privilege. Then take their recommendations and lock down your network some more.