TL;DR
Blackberry Cylance for Windows is affected by three vulnerabilities.
- CVE-2021-32021 – Denial of service in message broker.
- CVE-2021-32022 – Low privileged delete using CEF RPC server.
- CVE-2021-32023 – Elevation of privilege in message broker.
A heap overflow resulting in a denial of service, low privilege arbitrary file delete and an elevation of privilege from limited service accounts to SYSTEM.
It is recommended that the software is either upgraded to the latest 158x stream or version 1578 at the time of writing. Further information on the advisory can be found here.
CVE-2021-32021 Denial of Service
Cylance uses an intricate message broker system where various components of the software communicate over RPC using the ALPC mechanism. ALPC by its very nature is designed for local inter-process communication only, therefore the vulnerability is limited to local attack only.
The software is predominantly written in .NET but there is a native DLL that handles the dispatch of RPC calls to different components called CefServer.dll, and in here lies the problem.
The RPC mechanism limits the request size to 64k, most likely due to certain RPC limits present within older generations of Windows. When Cylance is required to send a larger RPC message, a special token is sent over the RPC mechanism to indicate that the RPC message should be read from a local file on disk instead.
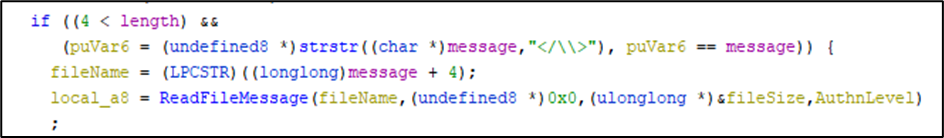
If the message starts with the string </\\> it is assumed the remaining part of the RPC message is a path to a local file on disk.
The bug it a type of TOCTOU (Time-Of-Check Time-Of-Use) class where the size of the allocated heap memory is not sufficient to hold the entire contents of the file.
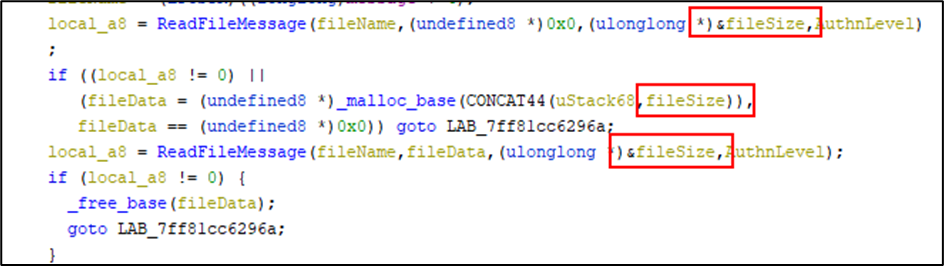
The first call to ReadFileMessage passes a pointer to the fileSize variable. On its return, the variable is populated with the current fileSize. This is used to allocate the memory to store the file contents using malloc.
The second call to ReadFileMessage then proceeds to pass in the block of allocated memory for reading. At this point all is well. Unfortunately, the ReadFileMessage function will a second time determine the file size using the GetFileSize API instead of using the fileSize variable that was already determined on the previous call.
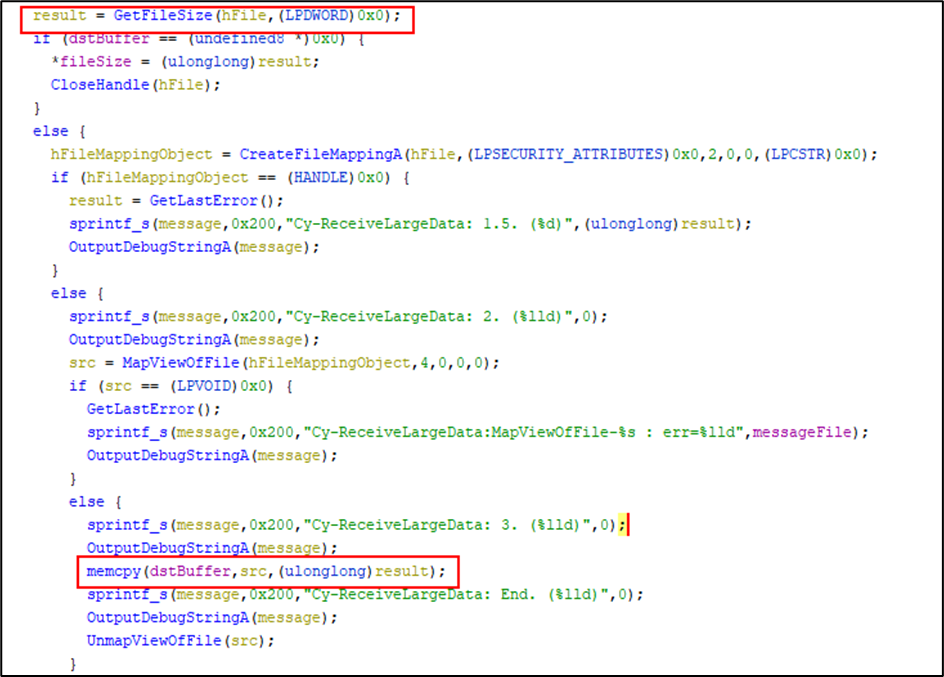
This results in a race condition. If the RPC message file increases in size between the first and second call to ReadFileMessage, the heap is overflowed when the memcpy function is called.
This will cause a denial of service within the Cylance service. The net result of this was no more detection of viruses or malware since the service was no longer operational.
CVE-2021-32022 Low Privilege Delete
Following on from the large RPC message as described above for CVE-2021-32021, the ReadFileMessage function was found to delete the RPC message file once the contents had been consumed.
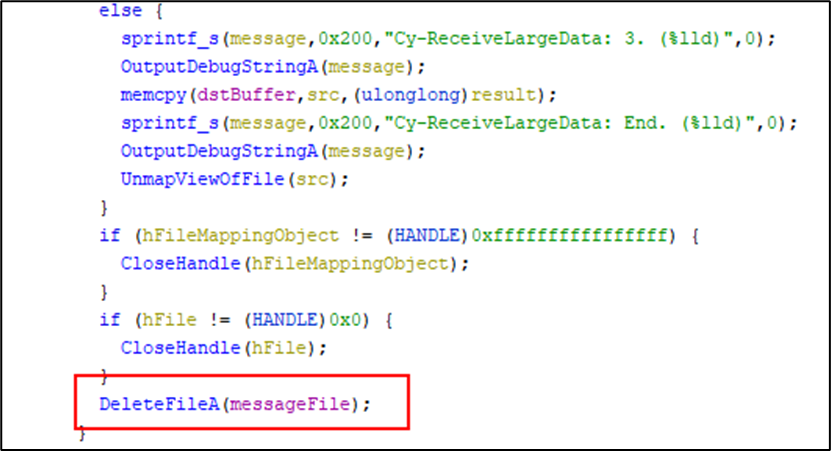
No checks were in place to determine if the path was outside of expected locations or if the message file was a valid RPC message first. Therefore, malicious actors can send an RPC message pointing to an arbitrary file on disk. Because the CefServer.dll is typically hosted inside the privileged Cylance service, the net result is that any file on the operating system that is not in use can be deleted by an unprivileged user.
CVE-2021-32023 – Elevation of privilege in message broker
The third and final vulnerability within the trio of issues is an elevation of privilege from a local unprivileged service account to SYSTEM. Similar to our previously reported impersonation abuse within Docker Desktop, Cylance suffers the same fate.
Like named pipes used in Docker’s RPC communication mechanism, ALPC also supports impersonating the connecting client. This was able to be abused through registering a custom ALPC port through Cylance’s publish and subscribe RPC messages.
The attack involves first sending a subscribe message indicating an endpoint id under the attacker’s control. This internally within the Cylance service registers the custom endpoint as a valid message end point.
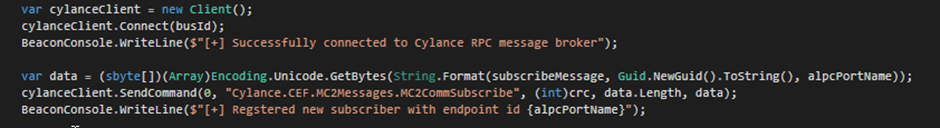
Once the custom ALPC endpoint is registered, the attacker can setup an ALPC port listening for incoming connections.
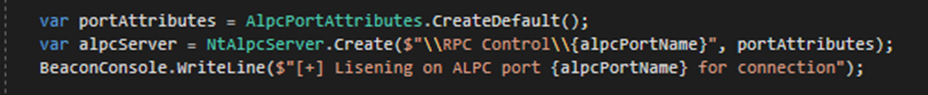
Finally, the attacker can now publish a bogus message to the same ALPC port, utilising the message broker inside the Cylance service. On receipt of the message, the Cylance service (running as SYSTEM) will connect to the attacker controlled ALPC port to dispatch the message.
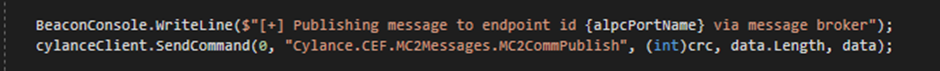
If the attacking process has the SeImpersontePrivilege, the SYSTEM token of the client can be impersonated, and the attacker can gain complete control of the machine.

Disclosure
Whilst it took several months for Blackberry to implement the fixes to these issues, the experience of disclosing with them was pleasant. A call was setup after confirmation of the vulnerabilities to discuss the plan of action. We were kept informed on a fortnightly basis of progress throughout. Vendors, be more like Blackberry!
- 4th May 2021 – Initial Disclosure
- 14th May 2021 – Issues confirmed, and tickets lodged with development team
- 26th May 2021 – Additional POC sent for CVE-2021-32023 to help replicate
- 2nd June 2021 – Call with Cylance team to discuss fix timeline and disclosure plans
- 4th August 2021 – Windows Agent v1580 release stream with all fixes implemented
- 8th September 2021 – Window Agent v1578 release with all fixes implemented
- 9th November 2021 – Coordinated disclosure














