Introduction
Recently we were engaged by a client experiencing a potential data leak incident. Amidst their expansion, they were constructing a new data centre. Due to pressing business needs, they accelerated the setup of part of their infrastructure.
This urgency led to them setting up a Domain Controller (DC) in a warehouse, however the building wasn’t particularly well secured physically. Monitoring of the physical security wasn’t great either, so CCTV didn’t cover the DC.
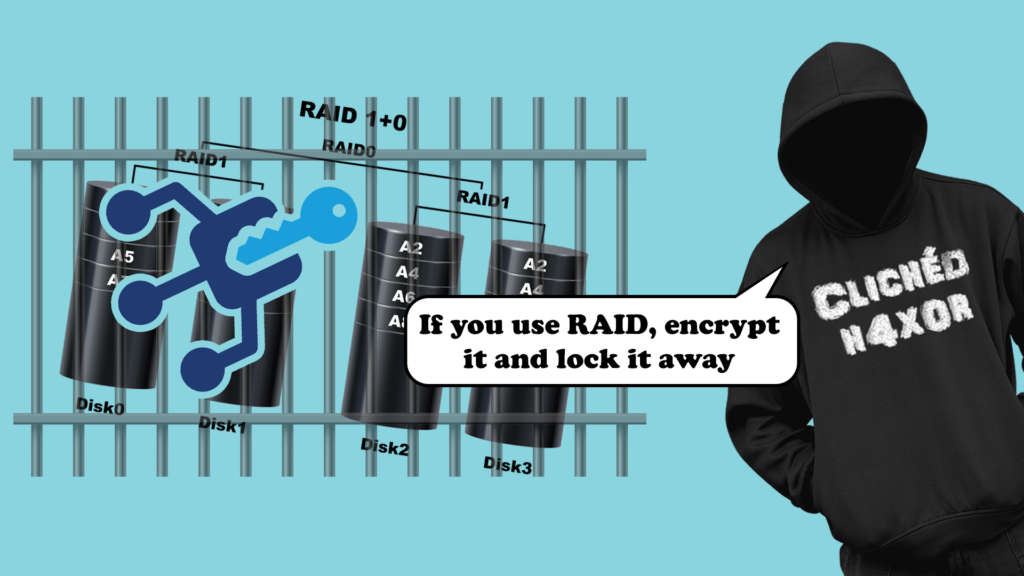
The DC was wisely configured in a RAID 10 setup, offering redundancy in the case of disc failure. However, one of the discs had been removed without authorisation and couldn’t be located, possibly stolen by a rogue employee.
RAID 10, for example, merges speed and data protection by mirroring and striping data across disks. Grasping the complexities of RAID is essential in understanding data security challenges.
This led to a challenge – what was on the removed disc and did the data loss present a problem?
Our initial step was to image the drives and verify their hashes, which, as expected, were entirely distinct.
Identifying RAID configurations through drive fingerprinting
A crucial aspect in extracting data from RAID systems is identifying their configurations, especially when the specific setup is unknown. This can be achieved through a process known as drive fingerprinting.
On unencrypted disks, the data patterns and structures on each drive can be examined, meaning that you can determine whether the drives are part of a striped, mirrored, or combined RAID setup. This knowledge is vital in scenarios where a RAID system is reconstructed or analysed for data theft or recovery.
Tools for data extraction from unencrypted drives
In cases where disks are unencrypted, tools such as Magnet Axiom, PhotoRec, and even Strings can be employed to extract data. These tools can recover various file types and analyse the content, proving invaluable in forensic investigations.
This allowed us to piece together the missing data.
The wider problem
The data wasn’t encrypted.
Despite RAID’s benefits in data protection, there are serious limitations in data breach scenarios. Disk encryption is critical here. It converts data into a code unreadable without the proper encryption key, ensuring that even if a disk is removed or accessed by unauthorised individuals, the data remains secure.
Consider an insider threat scenario within an organisation, where a disgruntled employee tampers with the disks in a RAID array. If these disks lack encryption, sensitive data might be compromised.
In an instance where a DC is set up without adequate physical security, the absence of disk encryption can lead to the exposure of critical information, including Remote Desktop Protocol session logs, Windows Event Logs, and user activity records.
It’s vital to understand that encryption does not impede data recovery in RAID setups. Authorised personnel can decrypt the data using the encryption keys, ensuring security and accessibility.
Effective disk encryption requires robust standards and secure encryption key management. Regular audits and updates of encryption protocols are crucial for maintaining data security.
Conclusion
This post highlights the essential need to integrate disk encryption with RAID technology to safeguard sensitive data.
While RAID offers redundancy and performance advantages, disk encryption adds a critical layer of security against data leaks. Combining physical and digital security measures is imperative in protecting critical data infrastructure.