This post could be either exciting, or not. It all depends on how you position yourself in the wonderful world of security and, specifically, the gaming industry.
This is a post about a vector of attack that I’ve been looking at for a while, but took me a while to actually get a real world exploit working.
To get the big stuff out of the way: I’ve found the circumstances where I can exploit a game player’s PC directly through content delivered by Steam’s Workshop.
Right, if you’re a PC game player and that’s freaking you out, then let me just quantify it: it’s only on one specific game and if you’ve chosen to download Workshop items for that game. I’m not going to name the game just yet as I am waiting for a response from the game company to explain the vulnerability.
So what’s this big vector: quite simply the game uses a LUA interpreter to execute code from Steam Workshop uploads without passing it through any form of sandboxing or restricting of dangerous methods, such as os.execute.
This is very dangerous as most people will run Steam as an administrator – all I need to do is put my dodgy remote access toolkit in the workshop item, upload it to the Steam Workshop and give it some reason for the game players to download it and run.
Getting the item to be downloaded can easily be done, if we tune it to our audience and advertise the mod as cheating the game, making it easy to get achievements or just providing dodgy Japanese cartoony style reskinning of the graphics then it will be downloaded by thousands before we can blink.
Proof of Concept
Of course doing this in theory is no fun: we need to prove that we can write a module. And upload it to the Steam Workshop. And run it.
So this is what I did: a very simple mod to just run Meterpreter and give a call back to my Metasploit listener. My version one literally shelled out to run the Meterpreter exe which I had packaged in the mod. This was immediately caught by my anti-virus software.
Annoyingly for me most people will have AV software, even if it is Windows Defender. This left two choices: a native Meterpreter client in LUA or to encode the client. There is no LUA meterpreter client and I don’t know enough about LUA to write one, so encoding there is.
Fortunately I have a colleague who’s very good at masquerading exes, a quiet shout to him and I had a bit of encoded Powershell that bypass all the four or five anti-virus clients I had to hand.
So the next step was to publish it to the Steam Workshop. And here it is, available for anybody to download: (well, except I then restricted public access)
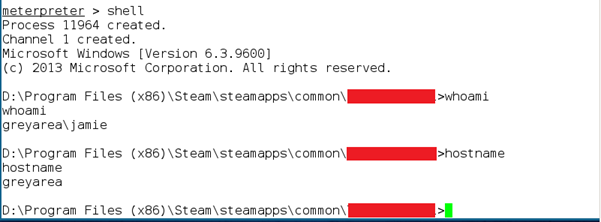
Then I got one of my colleagues to download it as a mod to the game and start to play the game, here’s a quick screen capture:
Conclusion
What’s the lesson here? Don’t trust Workshop items, a lot of game producers do not specialise in security and have little or no ideas about sandboxing and securing software.
It is also really, really hard to get hold of computer game writers, to alert them to this issue I submitted various forms, posted in forums and asked favours of moderators.
Computer game publishers: Set up a security contact and actually look at it, at least once a week.
If you’re going to let users provide content, sandbox it. Restrict running of any calls to read native files or run commands. I went through 10 different games where they had used sandboxing and I couldn’t perform an exploit before I got to this one.
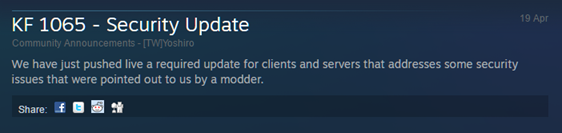
As a cautionary tale: I was procrastinating over writing this blog post, I happened to see this entry in the changelog for Tripwire’s Killing Floor, showing that there’s much, much more out there: